Question 281
Which path below is available only when CoreXL is enabled?
Question 282
What is the main difference between Threat Extraction and Threat Emulation?
Question 283
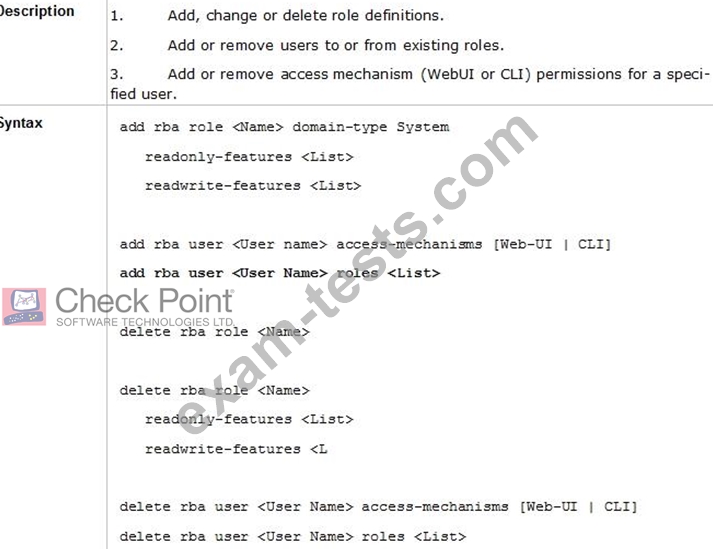
Which command is used to add users to or from existing roles?
Question 284
What are the three authentication methods for SIC?
Question 285
Fill in the blank: The IPS policy for pre-R80 gateways is installed during the _______ .