Question 61
On the following picture an administrator configures Identity Awareness:
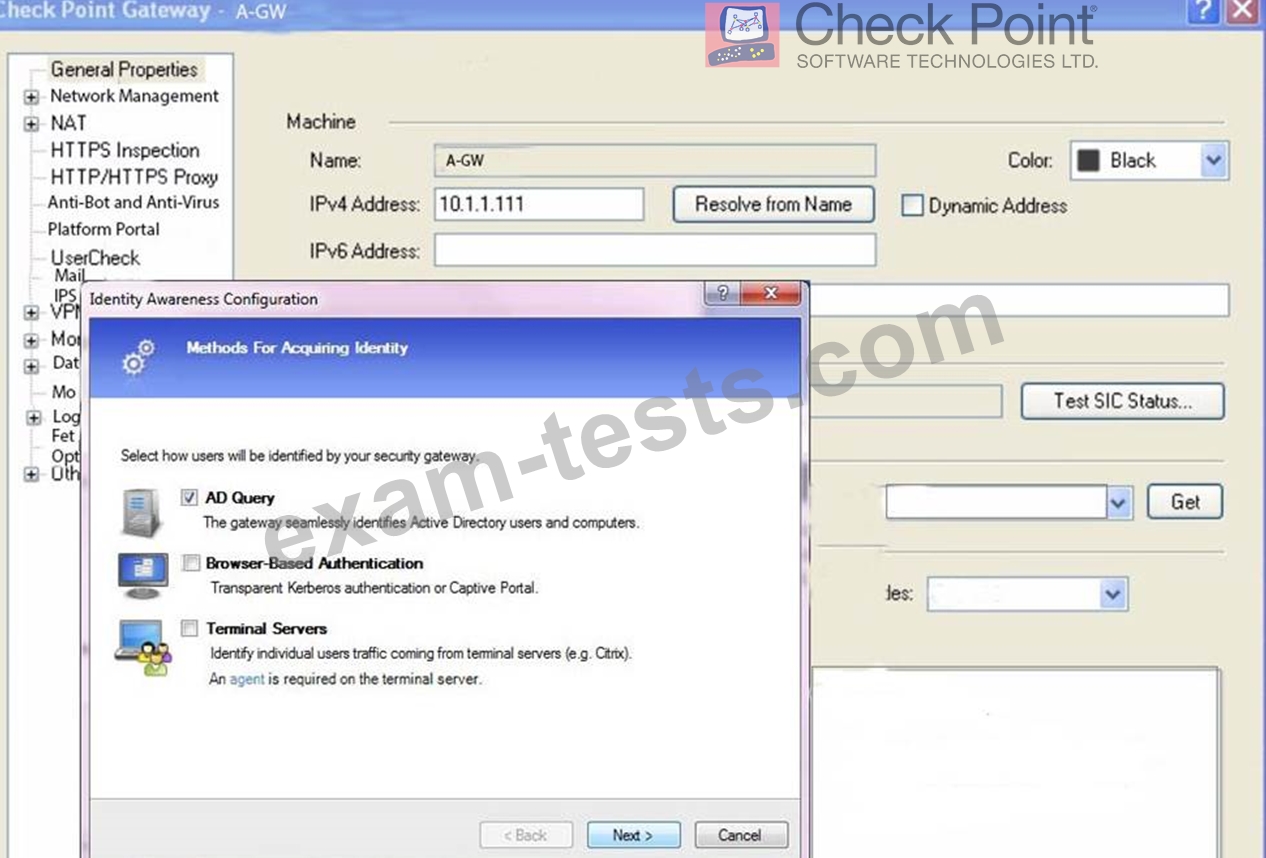
After clicking "Next" the above configuration is supported by:

After clicking "Next" the above configuration is supported by:
Question 62
Which authentication scheme requires a user to possess a token?
Question 63
Which software blade enables Access Control policies to accept, drop, or limit web site access based on user, group, and/or machine?
Question 64
Please choose correct command syntax to add an "emailserver1" host with IP address 10.50.23.90 using GAiA management CLI?
Question 65
You have discovered suspicious activity in your network.
What is the BEST immediate action to take?
What is the BEST immediate action to take?

