Question 71
In R80 spoofing is defined as a method of:
Question 72
You have a Geo-Protection policy blocking Australia and a number of the countries. You network now requires a Check point Firewall to be installed in Sydney, Australia. What must you do to get SIC to work?
Question 73
When gathering information about a gateway using CPINFO, what information is included or excluded when using the "-x" parameter?
Question 74
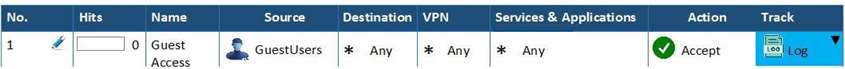
You have created a rule at the top of your Rule Base to permit Guest Wireless access to the Internet. However, when guest users attempt to reach the Internet, they are not seeing the splash page to accept your Terms of Service, and cannot access the Internet. How can you fix this?

Question 75
Check Point Support in many cases asks you for a configuration summary of your Check Point system. This is also called:
Premium Bundle
Newest 156-315.80 Exam PDF Dumps shared by BraindumpsPass.com for Helping Passing 156-315.80 Exam! BraindumpsPass.com now offer the updated 156-315.80 exam dumps, the BraindumpsPass.com 156-315.80 exam questions have been updated and answers have been corrected get the latest BraindumpsPass.com 156-315.80 pdf dumps with Exam Engine here:

