Question 331
From SecureXL perspective, what are the tree paths of traffic flow:
Question 332
The Firewall kernel is replicated multiple times, therefore:
Question 333
On the following picture an administrator configures Identity Awareness:
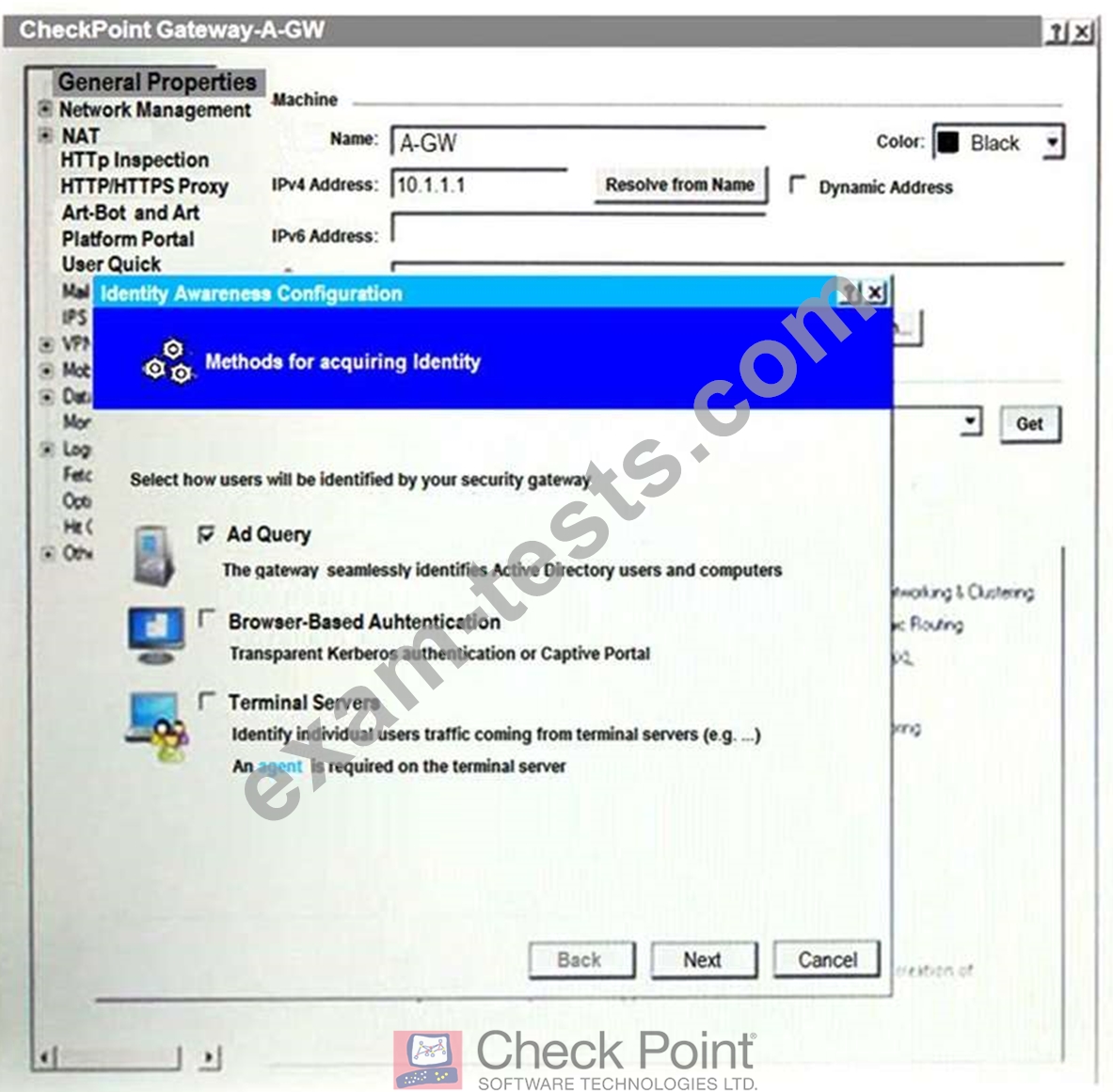
After clicking "Next" the above configuration is supported by:

After clicking "Next" the above configuration is supported by:
Question 334
In R80 spoofing is defined as a method of:
Question 335
After making modifications to the $CVPNDIR/conf/cvpnd.C file, how would you restart the daemon?

