Question 191
In R80 spoofing is defined as a method of:
Question 192
You have three servers located in a DMZ, using private IP addresses. You want internal users from 10.10.10.x to access the DMZ servers by public IP addresses. Internal_net
10.10.10.x is configured for Hide NAT behind the Security Gateway's external interface.
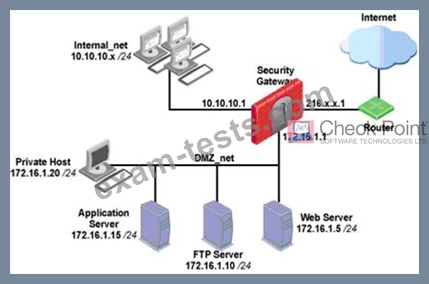
What is the best configuration for 10.10.10.x users to access the DMZ servers, using the DMZ servers' public IP addresses?
10.10.10.x is configured for Hide NAT behind the Security Gateway's external interface.

What is the best configuration for 10.10.10.x users to access the DMZ servers, using the DMZ servers' public IP addresses?
Question 193
When simulating a problem on CLusterXL cluster with cphaprob -d STOP -s problem -t 0 register, to initiate a failover on an active cluster member, what command allows you remove the problematic state?
Question 194
When deploying multiple clustered firewalls on the same subnet, what does the firewall administrator need to configure to prevent CCP broadcasts being sent to the wrong cluster?
Question 195
Which web services protocol is used to communicate to the Check Point R80 identity Awareness Web APi?

