Question 56
Scenario: When reviewing the activity logs for a web application, a Citrix Engineer notices a high number of requests for the page, /setup.aspx. Further investigation reveals that most of these requests originated from outside the network. Which protection can the engineer implement to prevent this?
Question 57
Scenario: A Citrix Engineer is reviewing the Citrix Web App Firewall log files using the GUI. Upon further analysis, the engineer notices that legitimate application traffic is being blocked.
What can the engineer do to allow the traffic to pass through while maintaining security?
What can the engineer do to allow the traffic to pass through while maintaining security?
Question 58
Which build-in TCP profile can a Citrix Engineer assign to a virtual server to improve performance for users who access an application from a remote office over an ATM connection?
Question 59
Scenario: A Citrix Engineer has configured Citrix Application Delivery Management (ADM) to monitor applications presented by Citrix ADC appliances. When reviewing the App Security Dashboard, the engineer finds no data.
What must the engineer do to ensure data is being collected from the applications?
What must the engineer do to ensure data is being collected from the applications?
Question 60
Scenario: A Citrix Engineer has deployed Front-end Optimization on NetScaler. Below is the snippet of the content before and after optimization.
Before Optimization:
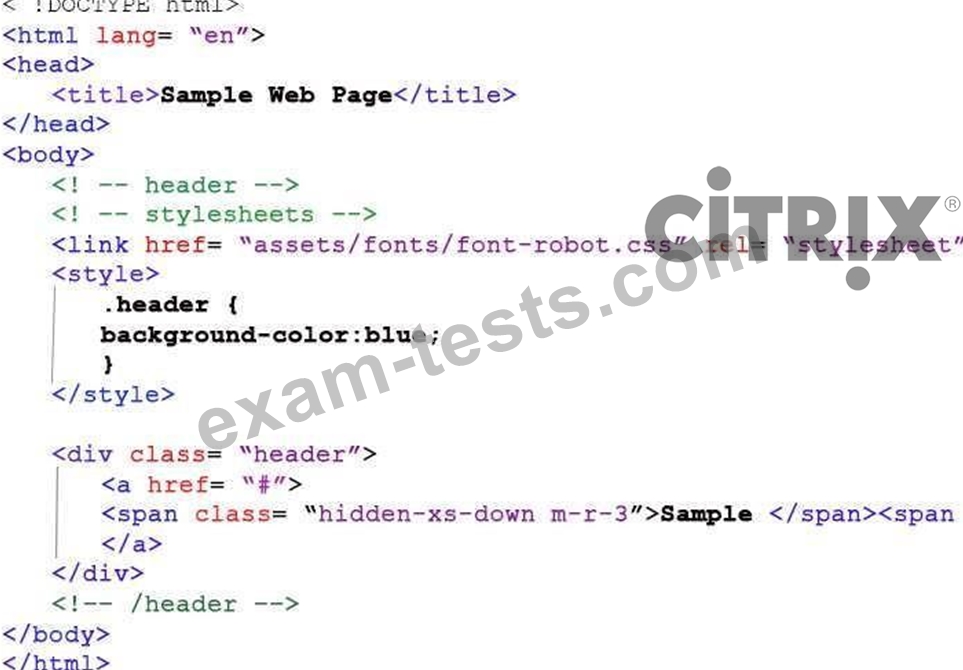
After Optimization:
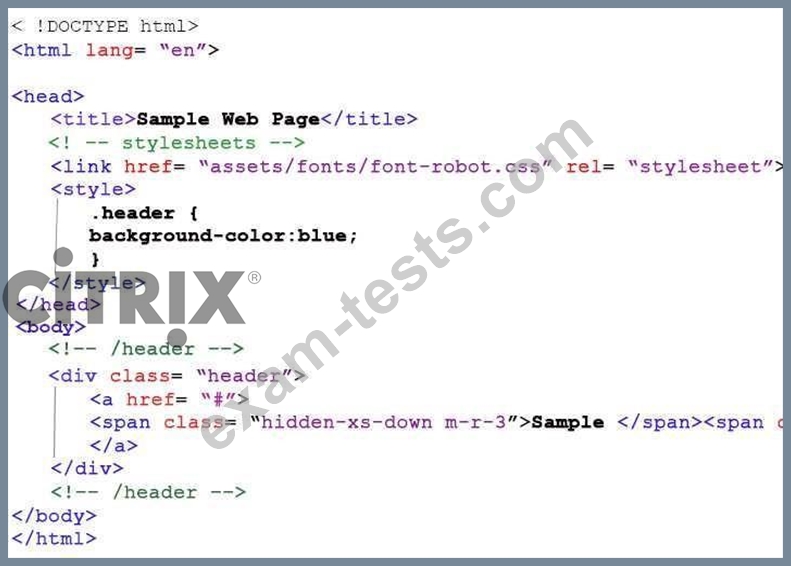
Which optimization technique has been applied to the content?
Before Optimization:

After Optimization:

Which optimization technique has been applied to the content?

