Question 76
Which syntax is used to write a StyleBook?
Question 77
A Citrix Engineer needs to protect a website that contains sensitive data such as employee ID numbers and customer ID numbers.
Which security check can the engineer implement to protect the sensitive data?
Which security check can the engineer implement to protect the sensitive data?
Question 78
Scenario: A Citrix Engineer needs to ensure that the flow of traffic to a web application does NOT overwhelm the server. After thorough testing, the engineer determines that the application can handle a maximum of 3,000 requests per minute. The engineer builds a limit identifier, rl_maxrequests, to enforce this limitation.
Which advanced expression can the engineer write in the Responder policy to invoke rate limiting?
Which advanced expression can the engineer write in the Responder policy to invoke rate limiting?
Question 79
Which three items does Citrix Application Delivery Management (ADM) require when adding an instances?
(Choose three.)
(Choose three.)
Question 80
Scenario: A Citrix Engineer created the policies in the attached exhibit.
Click the Exhibit button to view the list of policies.
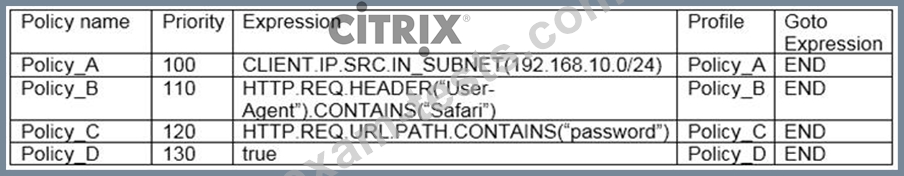
HTTP Request:
GET /resetpassword.htm HTTP/1.1
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64; rv:64.0) Gecko/20100101 Firefox/64.0 Host: www.citrix.com Accept-Language: en-us Accept-Encoding: gzip, deflate Connection: Keep-Alive Which profile will be applied to the above HTTP request?
Click the Exhibit button to view the list of policies.

HTTP Request:
GET /resetpassword.htm HTTP/1.1
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64; rv:64.0) Gecko/20100101 Firefox/64.0 Host: www.citrix.com Accept-Language: en-us Accept-Encoding: gzip, deflate Connection: Keep-Alive Which profile will be applied to the above HTTP request?

