Question 31
After reviewing a Proof of Concept (PoC) environment for Citrix Virtual Apps and Desktops, the corporate security team advises that user access to Regedit, command line, and PowerShell must be disabled.
Which technology can a Citrix Architect use to address this requirement with the least amount of effort?
Which technology can a Citrix Architect use to address this requirement with the least amount of effort?
Question 32
Scenario: Eight hundred users from a newly acquired company based in another continent will immediately require access to several Citrix applications being added to a zone within the Citrix Virtual Apps Site. Approximately 40 Citrix servers are being deployed in that zone.
Management informs a Citrix Architect that the new company has an unused Citrix ADC MPX 24xxx series applies that should be used to address Citrix Gateway requirements. The design must support updating the Citrix ADC firmware without user interruption.
What should the architect do to ensure that the Citrix ADC MPX 24000-series appliance addresses these requirements?
Management informs a Citrix Architect that the new company has an unused Citrix ADC MPX 24xxx series applies that should be used to address Citrix Gateway requirements. The design must support updating the Citrix ADC firmware without user interruption.
What should the architect do to ensure that the Citrix ADC MPX 24000-series appliance addresses these requirements?
Question 33
Scenario: IT management has decided which server hardware model to use for new XenApp and XenDesktop Sites and needs guidance on sizing the Hardware Layer.
Click the Exhibit to view the host details.
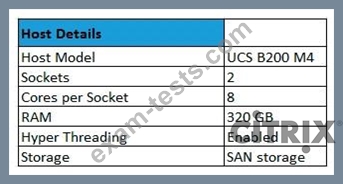
A Citrix Architect is planning to install XenServer 7.x on this host.
How many vCPUs will be available to the XenServer host?
Click the Exhibit to view the host details.

A Citrix Architect is planning to install XenServer 7.x on this host.
How many vCPUs will be available to the XenServer host?
Question 34
Scenario: A Citrix Architect needs to design a new XenApp and XenDesktop environment. The customer previously installed all applications locally on managed laptops and desktops but is willing to evaluate other application delivery methods as part of the new deployment. The environment will be standardized on Windows 10 and Windows Server 2016 for the Virtual Delivery Agent (VDA) machines.
As part of an application analysis performed earlier in the project, the information in the Exhibit was collected regarding one of the required applications.
Click the Exhibit button to view the information.
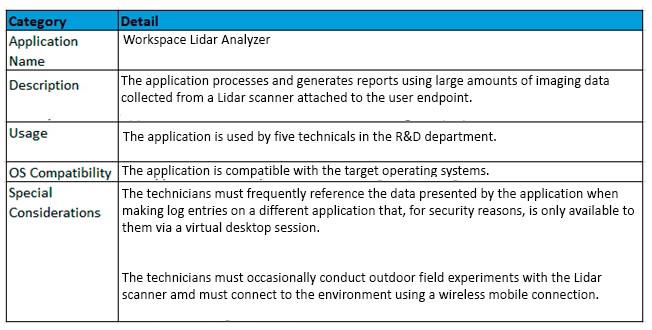
The customer has an additional objective to minimize the number of network traffic in the environment, particularly on WAN or metered links.
How should the architect install the application?
As part of an application analysis performed earlier in the project, the information in the Exhibit was collected regarding one of the required applications.
Click the Exhibit button to view the information.

The customer has an additional objective to minimize the number of network traffic in the environment, particularly on WAN or metered links.
How should the architect install the application?
Question 35
Scenario: A Citrix Architect needs to design a new XenApp and XenDesktop environment.
The architect has identified the User Layer requirements, as shown in the Exhibit.
Click the Exhibit button to view the requirements.
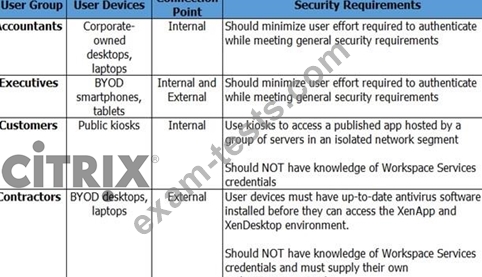
Additionally, management at the organization has identified the following general Access Layer requirements:
A multi-factor authentication method is required for any connections to the XenApp and XenDesktop environment originating from outside the corporate

network.
External connections must be authenticated by a NetScaler Gateway virtual server located in a DMZ network.

Internal connection traffic should NOT leave the internal corporate network.

Which authentication method should the architect use for the Accountants group?
The architect has identified the User Layer requirements, as shown in the Exhibit.
Click the Exhibit button to view the requirements.

Additionally, management at the organization has identified the following general Access Layer requirements:
A multi-factor authentication method is required for any connections to the XenApp and XenDesktop environment originating from outside the corporate

network.
External connections must be authenticated by a NetScaler Gateway virtual server located in a DMZ network.

Internal connection traffic should NOT leave the internal corporate network.

Which authentication method should the architect use for the Accountants group?

