Question 1
Which type of attack attempts to find data by repeatedly trying similar SQL with a modified predicate?
Question 2
Which type of masking directly masks and subsets data In a nonproduction database with minimal or no Impact on production environments?
Question 3
Examine these commands and responses:

Which object privilege must be granted to allow execution of the stored procedure?

Which object privilege must be granted to allow execution of the stored procedure?
Question 4
As the SYSKM user you must create the password-based keystore, which will be used for TDE. Examine this list:
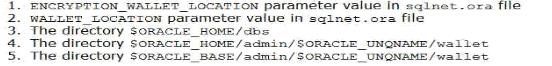
Identify the sequence that Oracle uses to search for the keystore and its location.

Identify the sequence that Oracle uses to search for the keystore and its location.
Question 5
Which two are true about auditing in an Oracle Database?

