Question 11
Which architecture is based on the principle of "never trust, always verify"?
Question 12
You want to make API calls against other OCI services from your instance without configuring user credentials. How would you achieve this?
Question 13
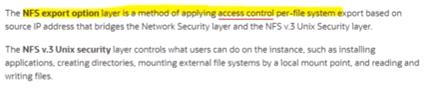
A company has OCI tenancy which has mount target associated with two File Systems, CG_1 and CG_2. These File Systems are accessed by IP-based clients AB_1 and AB_2 respectively. As a security administrator, how can you provide access to both clients such that CGI has Read only access on AB1 and CG_2 has Read/Write access on AB_2?
Question 14
How can you convert a fixed load balancer to a flexible load balancer?
Question 15
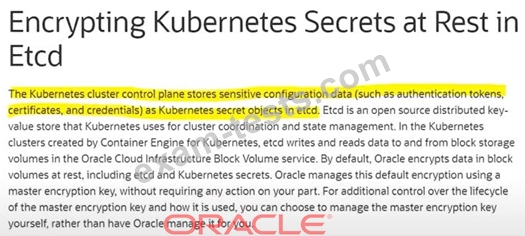
Where is sensitive configuration data (like certificates, and credentials) is stored by Kubernetes cluster control plane?