Question 41
Your customer has gone through a recent reorganization. As part of this change, they are organizing their Oracle Cloud Infrastructure (OCI) compartment structure to align with the company's new organizational structure. (Refer to the exhibit)

They have made the following change:
Compartment A is moved, and its new parent compartment is compartment Dev.
Policy defined in compartment A: Allow group G1 to manage instance-family in compartment A Policy defined in root compartment: Allow group admins to manage instance-family in compartment Ops: Test: A After the compartment move, which action will provide users of group G1 and admins with similar privileges as before the move?

They have made the following change:
Compartment A is moved, and its new parent compartment is compartment Dev.
Policy defined in compartment A: Allow group G1 to manage instance-family in compartment A Policy defined in root compartment: Allow group admins to manage instance-family in compartment Ops: Test: A After the compartment move, which action will provide users of group G1 and admins with similar privileges as before the move?
Question 42
You are working as a security consultant with a global insurance organization which is using Microsoft Azure Active Directory (AD) as identity provided to manager user login/passwords. When a user logs in to Oracle Cloud infrastructure (OCI) console, it should get authenticated by Azure AD.
Which set of steps are required to configure at OCI side in order to get it enabled
Which set of steps are required to configure at OCI side in order to get it enabled
Question 43
You have created compartment called Dev for developers. There are two IAM groups for developers: group-devl and group-dev2. You need to write an Identity and Access Management (IAM) policy to give users in these groups access to manage all resources in the compartment Dev.
Which of the following IAM policy will accomplish this?
Which of the following IAM policy will accomplish this?
Question 44
You have been asked to review some network proposals by a major client. The client's IT director needs to provision two Virtual Cloud Network (VCN) for a major application. Both applications use a large number of virtual machine instances, and so will ideally occupy VCNs with as many address spaces as possible. Additionally, in the future, VCN peering will be required to allow communication between the VCNs.
Which of the following are valid IP ranges to consider for the VCNs?
Which of the following are valid IP ranges to consider for the VCNs?
Question 45
You have an Oracle database system in a virtual cloud network (VCN) that needs to be accessible on port 1521 from your on-premises network CIDR 172.17.0.0/24.
You have the following configuration currently.
Virtual cloud network (VCD) is associated with a Dynamic Routing Gateway (DRG), and DRG has an active IPSec connection with your on-premises data center.
Oracle database system is hosted in a private subnet
The private subnet route table has the following configuration
The private subnet route table has following configuration.
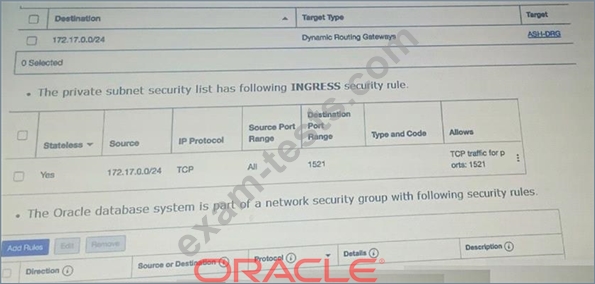
However, you are still unable to connect to the Oracle Database system.
Which action will resolve this issue?
A)
Add an EGRESS rule in network security group as following.

B)
Add a route rule in the private subnet route table as following.
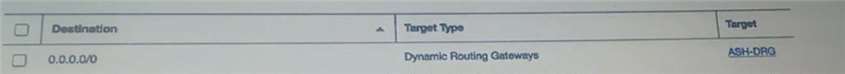
C)
Add an EGRESS rule in private subnet scurity list as following.
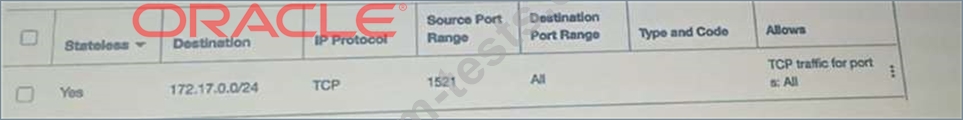
D)
Add an EGRESS rule in private subnet security list as following.
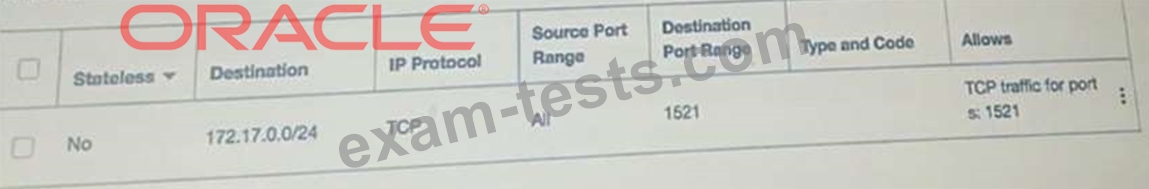
You have the following configuration currently.
Virtual cloud network (VCD) is associated with a Dynamic Routing Gateway (DRG), and DRG has an active IPSec connection with your on-premises data center.
Oracle database system is hosted in a private subnet
The private subnet route table has the following configuration
The private subnet route table has following configuration.

However, you are still unable to connect to the Oracle Database system.
Which action will resolve this issue?
A)
Add an EGRESS rule in network security group as following.

B)
Add a route rule in the private subnet route table as following.

C)
Add an EGRESS rule in private subnet scurity list as following.

D)
Add an EGRESS rule in private subnet security list as following.


