Question 66
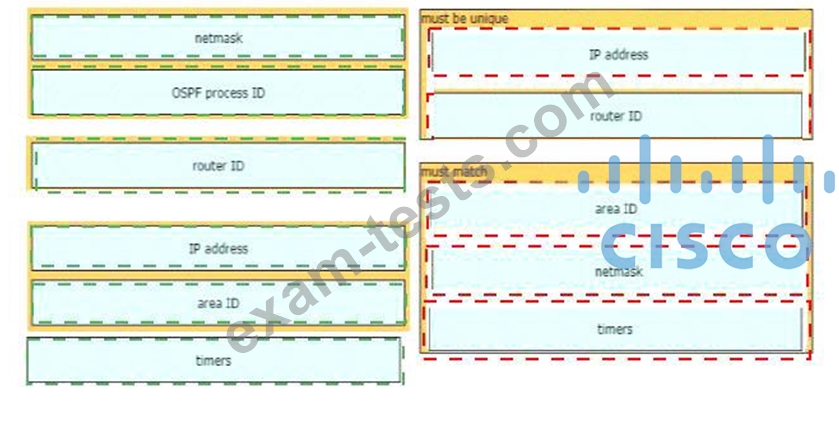
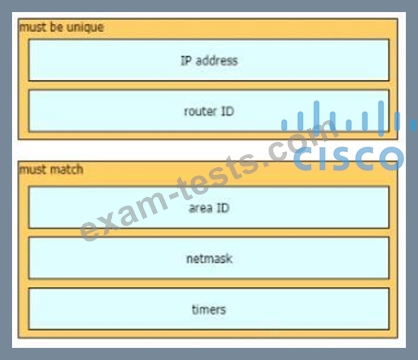
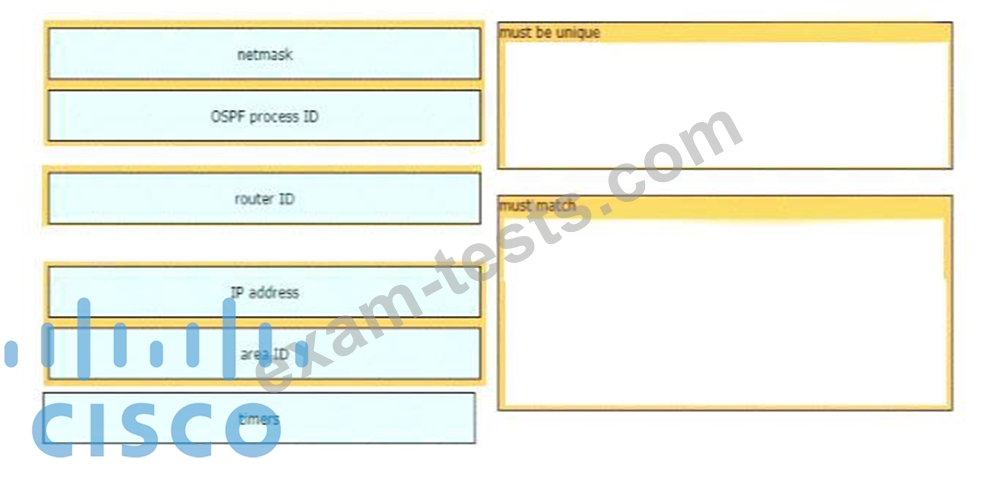
A network engineer is configuring an OSPFv2 neighbor adjacency Drag and drop the parameters from the left onto their required categories on the right. Not all parameters are used

Question 67
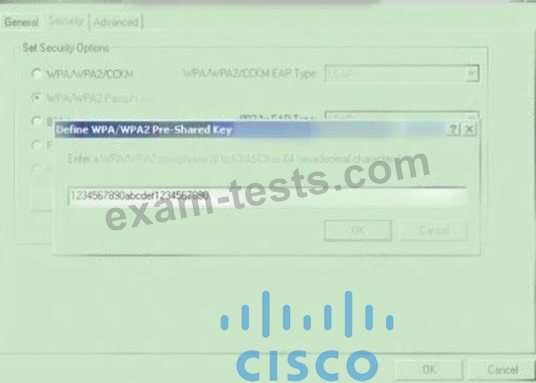
Which type of wireless encryption is used for WPA2 in preshared key mode?
Question 68
Refer to the exhibit.
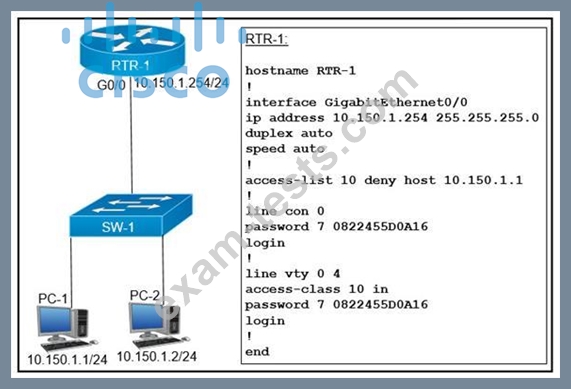
An access list is created to deny Telnet access from host PC-1 to RTR-1 and allow access from all other hosts A Telnet attempt from PC-2 gives this message:"% Connection refused by remote host" Without allowing Telnet access from PC-1, which action must be taken to permit the traffic?

An access list is created to deny Telnet access from host PC-1 to RTR-1 and allow access from all other hosts A Telnet attempt from PC-2 gives this message:"% Connection refused by remote host" Without allowing Telnet access from PC-1, which action must be taken to permit the traffic?
Question 69
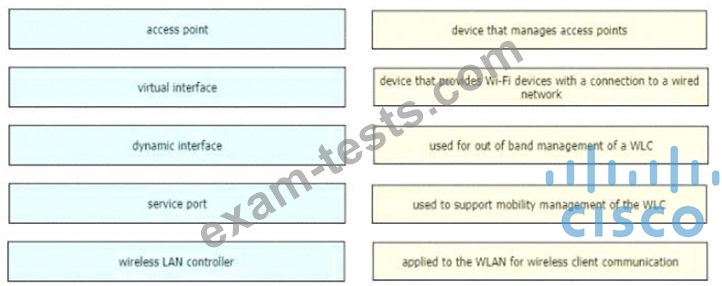
Drag and drop the WLAN components from the left onto the correct descriptions on the right.

Question 70
Refer to the exhibit.

Which switch in this configuration will be elected as the root bridge?
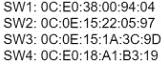

Which switch in this configuration will be elected as the root bridge?