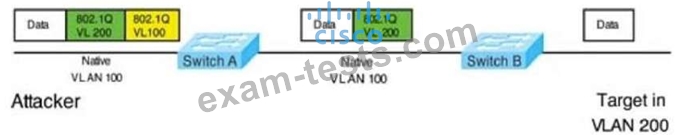
Question 31
Which Type of ipv6 unicast ip address is reachable across the internet?
Question 32
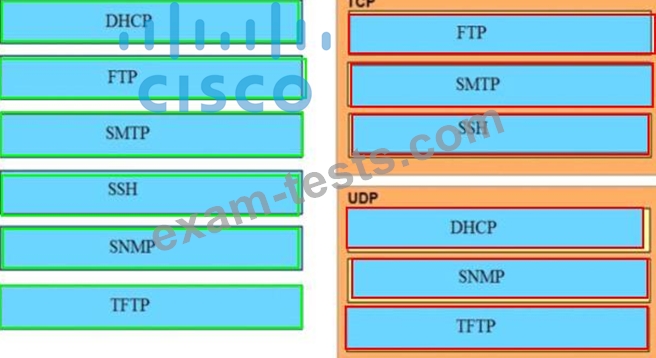
Drag and drop the application protocols from the left onto the transport protocols that it uses on the right
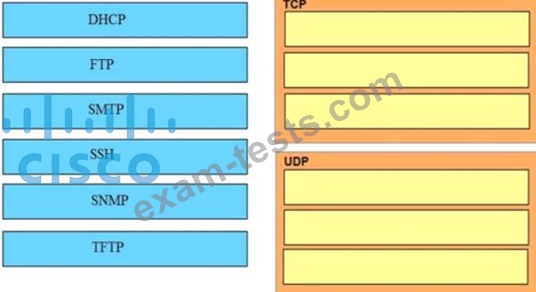

Question 33
A network administrator is asked to configure VLANS 2, 3 and 4 for a new implementation. Some ports must be assigned to the new VLANS with unused remaining. Which action should be taken for the unused ports?
Question 34
If a notice-level message is sent to a syslog server, which event has occurred?
Question 35
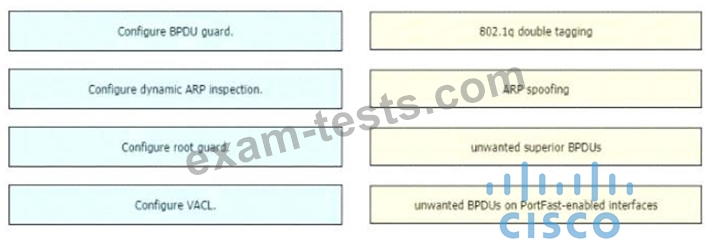
Drag and drop the threat-mitigation techniques from the left onto the types of threat or attack they mitigate on the right.