Question 86
An email user has been lured into clicking a link in an email sent by their company's security organization.
The webpage that opens reports that it was safe but the link could have contained malicious code. Which type of security program is in place?
The webpage that opens reports that it was safe but the link could have contained malicious code. Which type of security program is in place?
Question 87
Refer to the exhibit.
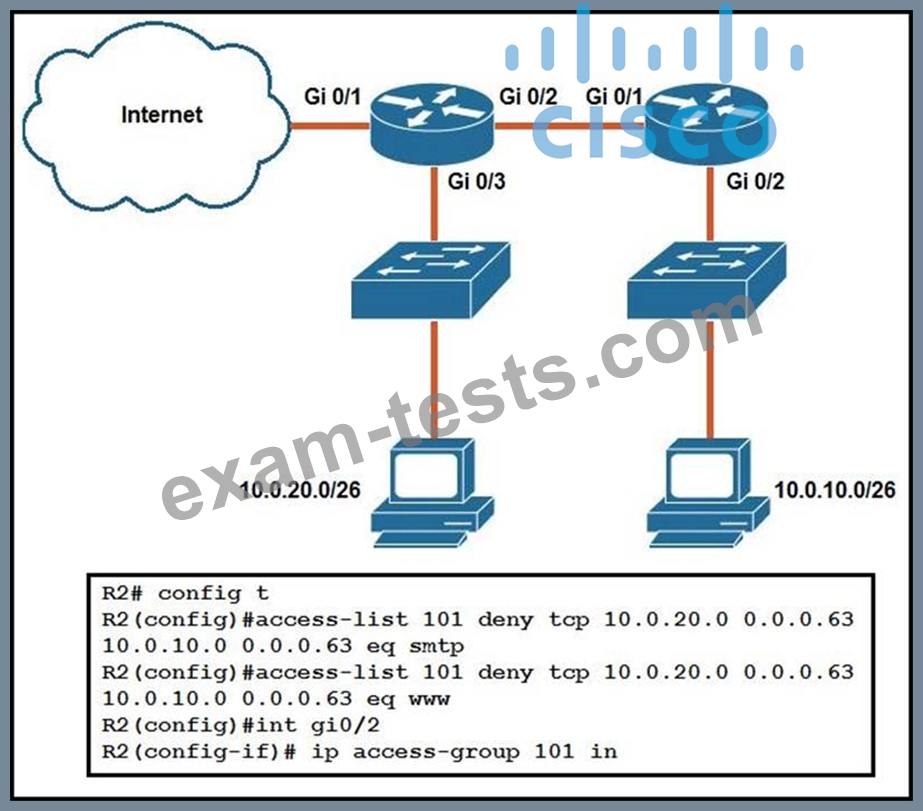
An extended ACL has been configured and applied to router R2. The configuration failed to work as intended.
Which two changes stop outbound traffic on TCP ports 25 and 80 to 10.0.20.0/26 from the 10.0.10.0/26 subnet while still allowing all other traffic? (Choose two.)

An extended ACL has been configured and applied to router R2. The configuration failed to work as intended.
Which two changes stop outbound traffic on TCP ports 25 and 80 to 10.0.20.0/26 from the 10.0.10.0/26 subnet while still allowing all other traffic? (Choose two.)
Question 88
An engineer has configured the domain name, user name, and password on the local router. What is the next step to complete the configuration for a Secure Shell access RSA key?
Question 89
I1
Which two command sequences must be configured on a switch to establish a Layer 3 EtherChannel with an open-standard protocol? (Choose two)
Which two command sequences must be configured on a switch to establish a Layer 3 EtherChannel with an open-standard protocol? (Choose two)
Question 90
Which two of these are characteristics of the 802.1Q protocol? (choose two)

