Question 126
A network engineer is configuring a switch so that it is remotely reachable via SSH. The engineer has already configured the host name on the router. Which additional command must the engineer configure before entering the command to generate the RSA key?
Question 127
Which level of severity must be set to get informational syslogs?
Question 128
Refer to the exhibit.
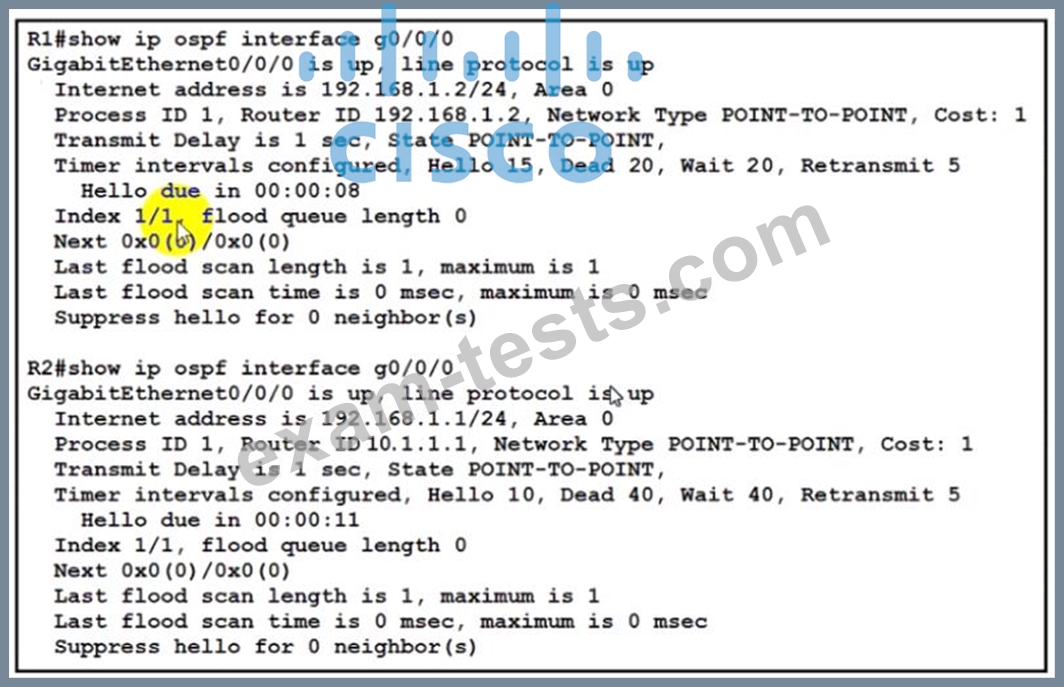
The network engineer is configuring router R2 as a replacement router on the network After the initial configuration is applied it is determined that R2 failed to show R1 as a neighbor Which configuration must be applied to R2 to complete the OSPF configuration and enable it to establish the neighbor relationship with R1?
A)
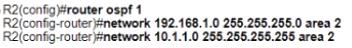
B)

C)

D)


The network engineer is configuring router R2 as a replacement router on the network After the initial configuration is applied it is determined that R2 failed to show R1 as a neighbor Which configuration must be applied to R2 to complete the OSPF configuration and enable it to establish the neighbor relationship with R1?
A)

B)

C)

D)

Question 129
Which technology is appropriate for communication between an SDN controller and applications running over the network?
Question 130
Which two IPv6 addresses are used to provide connectivity between two routers on a shared link? (Choose two)
Premium Bundle
Newest 200-301 Exam PDF Dumps shared by BraindumpsPass.com for Helping Passing 200-301 Exam! BraindumpsPass.com now offer the updated 200-301 exam dumps, the BraindumpsPass.com 200-301 exam questions have been updated and answers have been corrected get the latest BraindumpsPass.com 200-301 pdf dumps with Exam Engine here:

