Question 176
Which of the following connects a PC to its default gateway?
Question 177
Which of the following cloud computing technologies is used by enterprises to give employees access to individual Windows-based line-of-business applications on tablets, phones thin clients and other devices?
Question 178
A user logs on a PC and receives a message stating there is a duplicate IP address on the network. After
a system restart, the user notices the same error.
Which of the following is the MOST probable cause of the error?
a system restart, the user notices the same error.
Which of the following is the MOST probable cause of the error?
Question 179
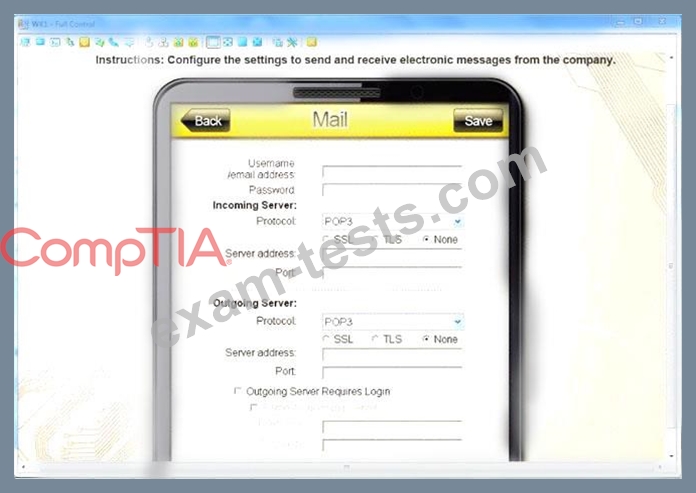
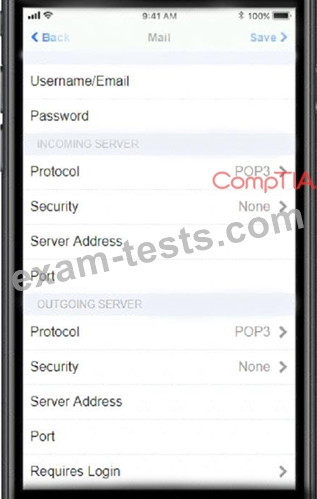
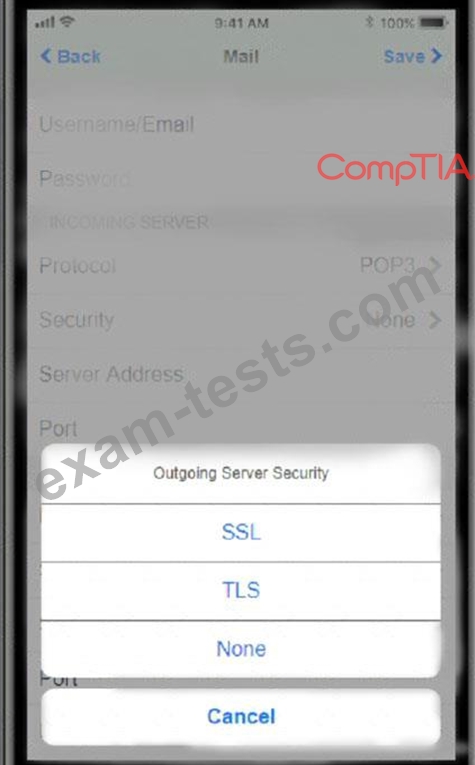
You need to configure your mobile device to send and receive electronic messages from your company.
You must use the company's WLAN as all e-mail services are on default non-secure ports.
The company's WLAN is broadcasting across the company for easier access.
Users must authenticate to the server with the same credentials in order to send and receive email.
Authentication should be enforced in the settings of the mobile device using the following parameters:
* Username: [email protected]
* Password: P@$$w0rd
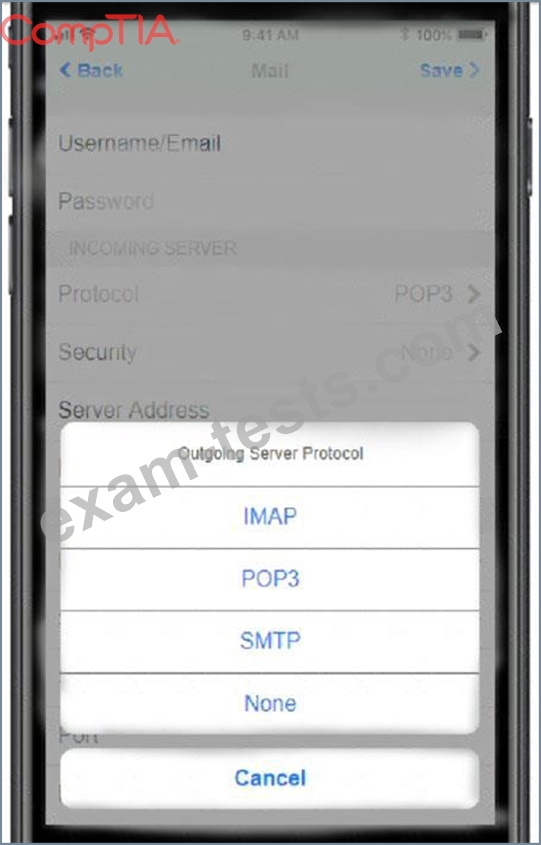
* Outgoing server: mail.techies.com
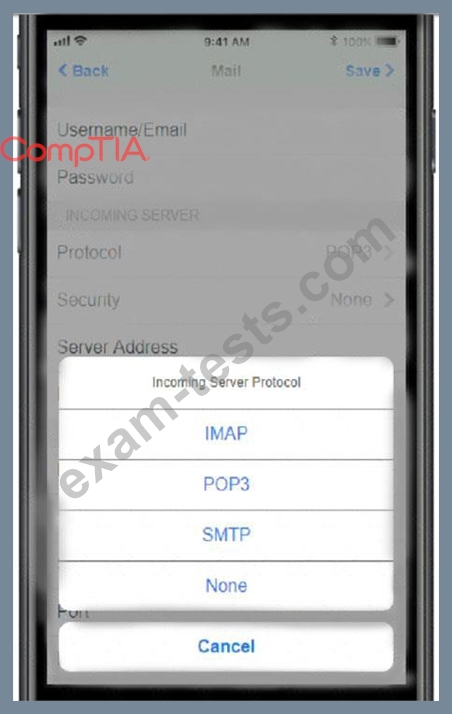
* Incoming server: pop3.techies.com
* Company SSID: Techies
* Security Key: CA:FE:33:71:00
INSTRUCTIONS:
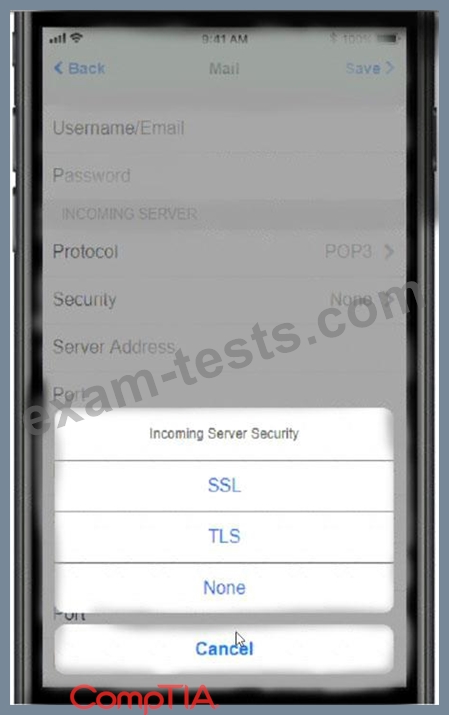
Update the mobile device's parameters to fit the criteria and support the strongest encryption available.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
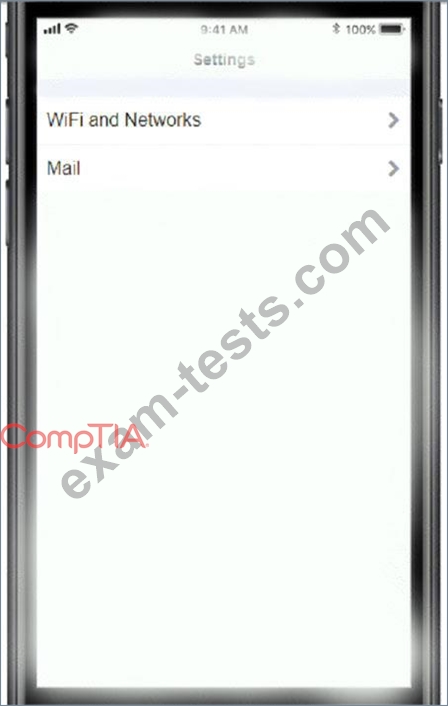
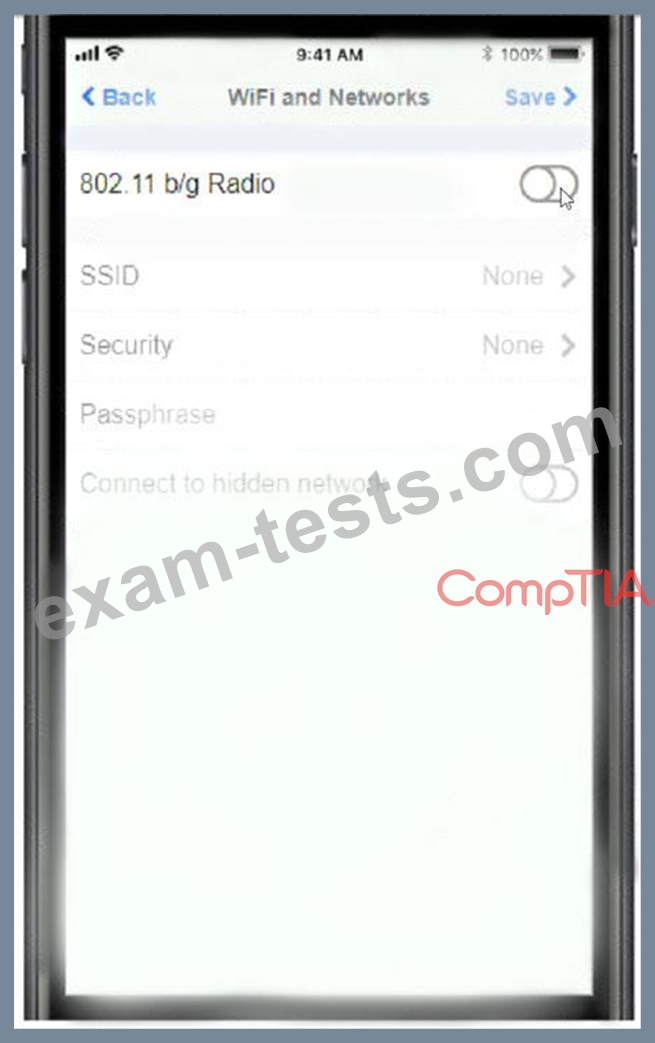
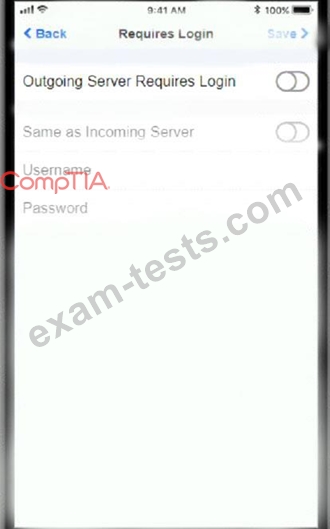
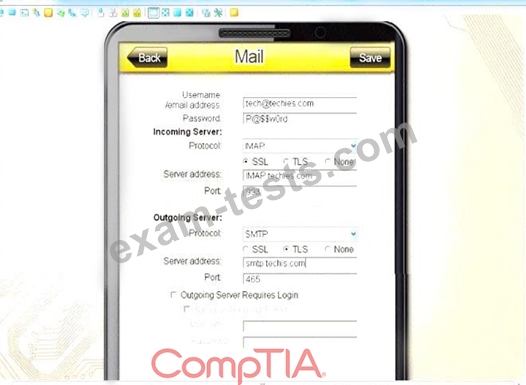
You must use the company's WLAN as all e-mail services are on default non-secure ports.
The company's WLAN is broadcasting across the company for easier access.
Users must authenticate to the server with the same credentials in order to send and receive email.
Authentication should be enforced in the settings of the mobile device using the following parameters:
* Username: [email protected]
* Password: P@$$w0rd
* Outgoing server: mail.techies.com
* Incoming server: pop3.techies.com
* Company SSID: Techies
* Security Key: CA:FE:33:71:00
INSTRUCTIONS:
Update the mobile device's parameters to fit the criteria and support the strongest encryption available.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.








Question 180
A customer recently moved a high-end graphics card from a known-working computer to a different computer. The computer works without issue when viewing email and web pages or when using certain applications. However, when a game with high-end graphics requirements is opened, the program will run for a few minutes before the computer shuts down. Which of the following is MOST likely causing the problem?