Question 26
Which of the following types of social engineering attacks can be prevented by the destruction of documents with personal or sensitive information?
Question 27
An administrator wants to search a file on a Linux server for the plus symbol (+). Which of the following will the administrator MOST likely use?
Question 28
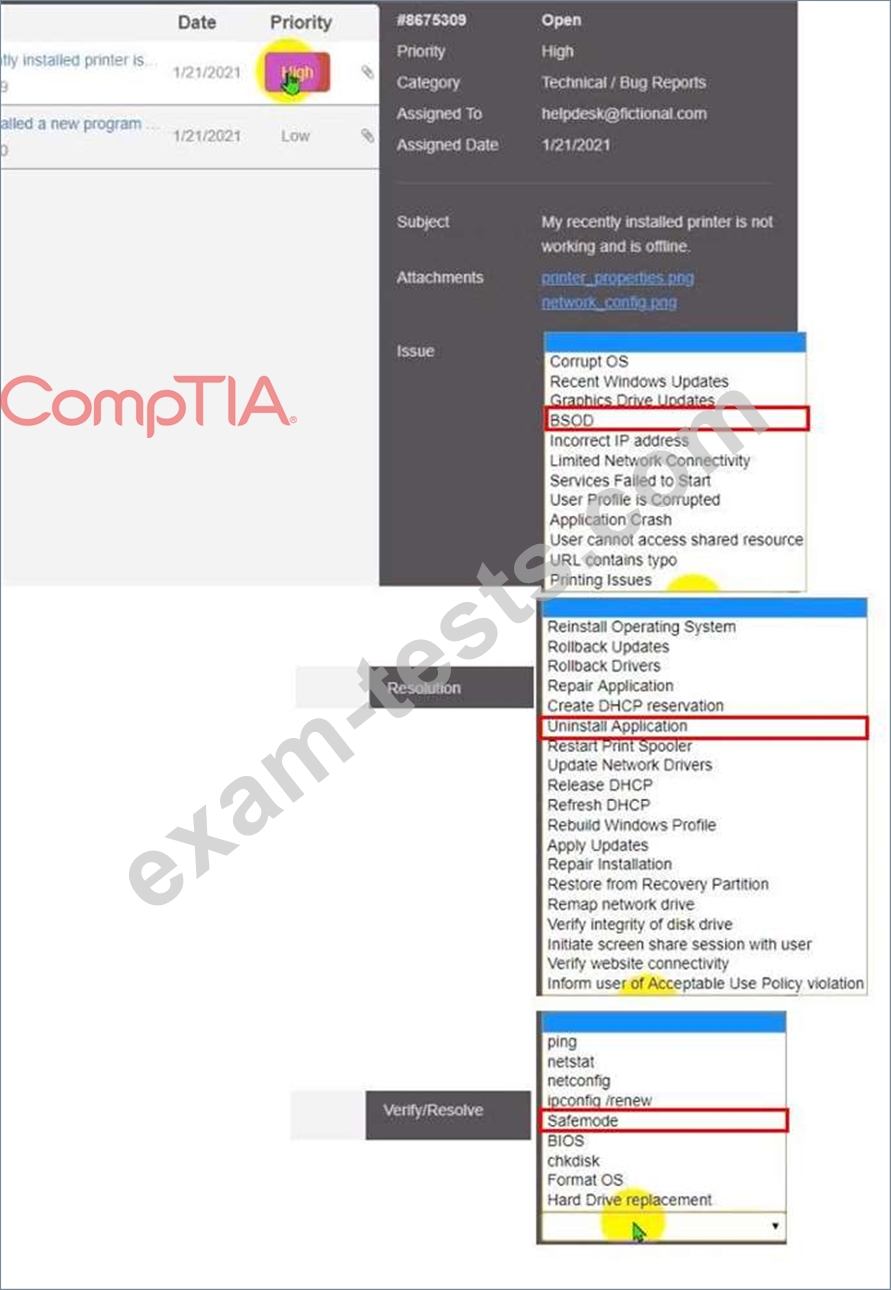
Welcome to your first day as a Fictional Company. LLC helpdesk employee. Please work the tickets in your helpdesk ticket queue.
Click on individual tickers to see the ticket details. View attachments to determine the problem.
Select the appropriate issue from the 'issue' drop-down menu. Then, select the MOST efficient resolution from the 'Resolution' drop-down menu. Finally, select the proper command or verification to remediate or confirm your fix of the issue from the Verify Resolve drop-down menu.


Click on individual tickers to see the ticket details. View attachments to determine the problem.
Select the appropriate issue from the 'issue' drop-down menu. Then, select the MOST efficient resolution from the 'Resolution' drop-down menu. Finally, select the proper command or verification to remediate or confirm your fix of the issue from the Verify Resolve drop-down menu.


Question 29
A small business has an open WiFi network for employees but does not want customers to connect to the access point. A technician has been dispatched to address the business's concerns.
Which of the following configuration settings should the technician change to satisfy the requirements of the business? (Choose two.)
Which of the following configuration settings should the technician change to satisfy the requirements of the business? (Choose two.)
Question 30
A technician is installing new software on an older laptop that has a current OS. The software contains a database back end that also requires installation. Which of the following should the technician review to ensure the software will run before installing it? (Choose two.)