Question 101
A technician is recycling PCs to be reused by a middle school. Which of the following methods is MOST appropriate for ensuring data hasbeen removed from the PCs?
Question 102
A technician is performing service on a computer and notices it is responding very slowly. The computer has 4GB of RAM. a four-core 3GHz processor, and a SATA I 54O0rpm 300GB HOD. The technician logs the following process information:
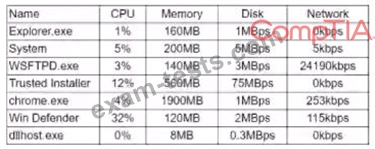
Based on this data, which of the following is the MOST likely cause of the performance issues?

Based on this data, which of the following is the MOST likely cause of the performance issues?
Question 103
A technician accessed a network share from a computer joined to workgroup. The technician logged in as
"user1" and directed the computer to save the username and password. Several weeks later, the technician wants to log in to this network share using the administrator account. The computer does not prompt for a username and password, but it automatically logs in to the network share under the "user1" account. Which of the following would allow the technician to log in using the "administrator" username?
"user1" and directed the computer to save the username and password. Several weeks later, the technician wants to log in to this network share using the administrator account. The computer does not prompt for a username and password, but it automatically logs in to the network share under the "user1" account. Which of the following would allow the technician to log in using the "administrator" username?
Question 104
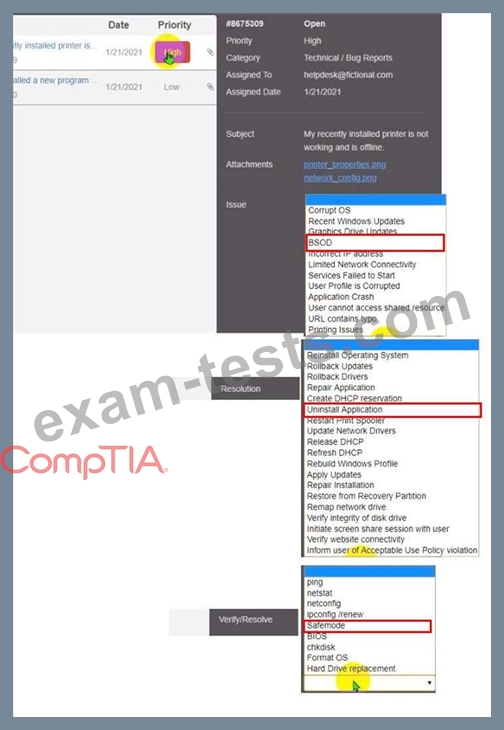
Welcome to your first day as a Fictional Company. LLC helpdesk employee. Please work the tickets in your helpdesk ticket queue.
Click on individual tickers to see the ticket details. View attachments to determine the problem.
Select the appropriate issue from the 'issue' drop-down menu. Then, select the MOST efficient resolution from the 'Resolution' drop-down menu. Finally, select the proper command or verification to remediate or confirm your fix of the issue from the Verify Resolve drop-down menu.


BSOD
Uninstall Application
Safemode
Click on individual tickers to see the ticket details. View attachments to determine the problem.
Select the appropriate issue from the 'issue' drop-down menu. Then, select the MOST efficient resolution from the 'Resolution' drop-down menu. Finally, select the proper command or verification to remediate or confirm your fix of the issue from the Verify Resolve drop-down menu.


BSOD
Uninstall Application
Safemode
Question 105
Joe. a technician, receives notification that a share for production data files on the network Is encrypted. Joe suspects a crypto virus Is active. He checks the rights of the network share to see which departments have access. He then searches the user directories of those departmental users who are looking for encrypted files. He narrows his search to a single user's computer. Once the suspected source of the virus is discovered and removed from the network, which of the following should Joe do NEXT?