Question 36
Which command set configures a Cisco Catalyst 9800 Series Wireless Controller so that the client traffic enters the network at the AP switch port?


Question 37
A user is trying to connect to a wireless network that is configured for WPA2-Enterprise security using a corporate laptop. The CA certificate for the authentication server has been installed on the Trusted Root Certification Authorities store on the laptop. The user has been prompted to enter the credentials multiple times, but the authentication has not succeeded. What is causing the issue?
Question 38
Refer to the exhibit.
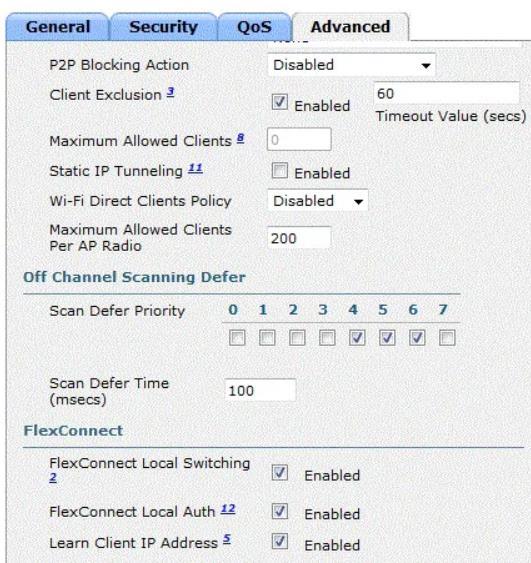
A customer has implemented Cisco FlexConnect deployments with different WLANs around the global and is opening a new branch in a different location. The engineers' task is to execute all the wireless configuration and to suggest how to configure the switch ports for new Aps. Which configuration must the switching team use on the switch ports?

A customer has implemented Cisco FlexConnect deployments with different WLANs around the global and is opening a new branch in a different location. The engineers' task is to execute all the wireless configuration and to suggest how to configure the switch ports for new Aps. Which configuration must the switching team use on the switch ports?
Question 39
For security purposes, an engineer enables CPU ACL and chooses an ACL on the Security > Access Control Lists > CPU Access Control Lists menu. Which kind of traffic does this change apply to, as soon as the change is made?
Question 40
Refer to the exhibit.
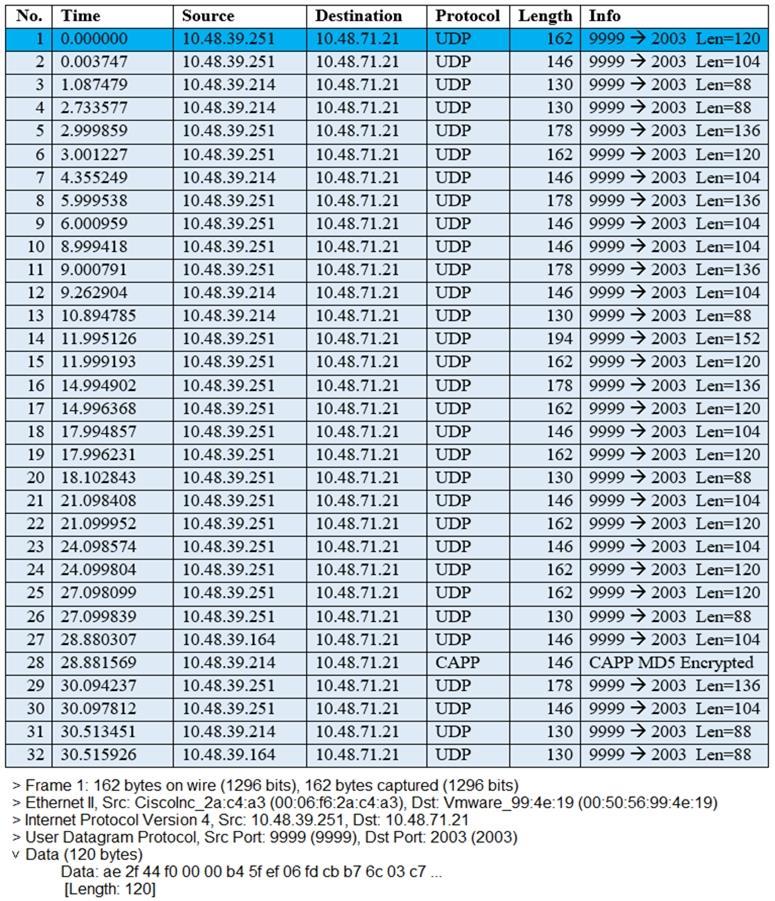
The image shows a packet capture that was taken at the CLI of the Cisco CMX server. It shows UDP traffic from the WLC coming into the server. What does the capture prove?

The image shows a packet capture that was taken at the CLI of the Cisco CMX server. It shows UDP traffic from the WLC coming into the server. What does the capture prove?