Question 106
Which two fields are available when creating an endpoint on the context visibility page of Cisco IS? (Choose two )
Question 107
What must match between Cisco ISE and the network access device to successfully authenticate endpoints?
Question 108
When planning for the deployment of Cisco ISE, an organization's security policy dictates that they must use network access authentication via RADIUS. It also states that the deployment provide an adequate amount of security and visibility for the hosts on the network. Why should the engineer configure MAB in this situation?
Question 109
An administrator is configuring TACACS+ on a Cisco switch but cannot authenticate users with Cisco ISE. The configuration contains the correct key of Cisc039712287. but the switch is not receiving a response from the Cisco ISE instance What must be done to validate the AAA configuration and identify the problem with the TACACS+ servers?
Question 110
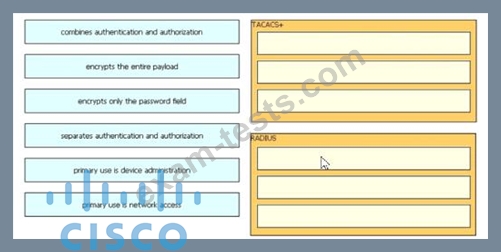
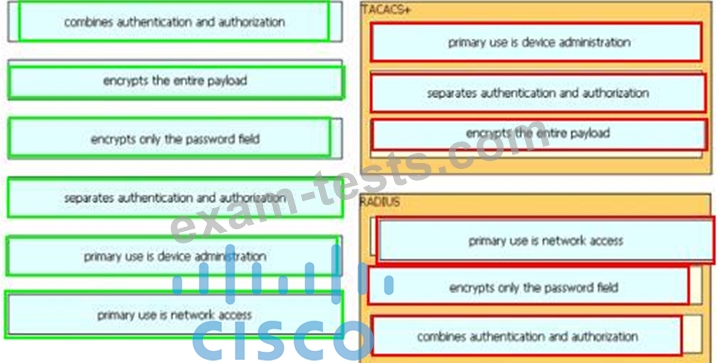
Drag and drop the description from the left onto the protocol on the right that is used to carry out system authentication, authentication, and accounting.