Question 106
Which of the following analyzes network traffic to trace specific transactions and can intercept and log traffic
passing over a digital network? Each correct answer represents a complete solution. Choose all that apply.
passing over a digital network? Each correct answer represents a complete solution. Choose all that apply.
Question 107
Which of the following network monitoring techniques requires extra monitoring software or hardware?
Question 108
Which of the following policies is used to add additional information about the overall security posture and serves to protect employees and organizations from inefficiency or ambiguity?
Question 109
Which of the following protocols is used for inter-domain multicast routing and natively supports "source- specific multicast" (SSM)?
Question 110
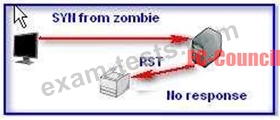
Which of the following steps are required in an idle scan of a closed port?
Each correct answer represents a part of the solution. Choose all that apply.
Each correct answer represents a part of the solution. Choose all that apply.