Question 31
Which of the following file contains the traces of the applications installed, run, or uninstalled from a system?
Question 32
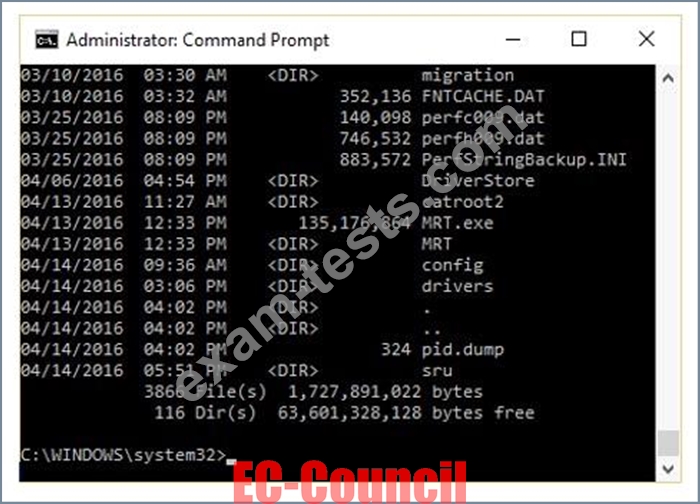
The given image displays information about date and time of installation of the OS along with service packs, patches, and sub-directories. What command or tool did the investigator use to view this output?

Question 33
Pick the statement which does not belong to the Rule 804. Hearsay Exceptions; Declarant Unavailable.
Question 34
Wireless access control attacks aim to penetrate a network by evading WLAN access control measures such as AP MAC filters and Wi-Fi port access controls. Which of the following wireless access control attacks allow the attacker to set up a rogue access point outside the corporate perimeter and then lure the employees of the organization to connect to it?
Question 35
What will the following Linux command accomplish?
dd if=/dev/mem of=/home/sam/mem.bin bs=1024
dd if=/dev/mem of=/home/sam/mem.bin bs=1024

