Question 1
What network security concept requires multiple layers of security controls to be placed throughout an IT infrastructure, which improves the security posture of an organization to defend against malicious attacks or potential vulnerabilities?
What kind of Web application vulnerability likely exists in their software?
What kind of Web application vulnerability likely exists in their software?
Question 2
Cryptography is the practice and study of techniques for secure communication in the presence of third
parties (called adversaries). More generally, it is about constructing and analyzing protocols that overcome
the influence of adversaries and that are related to various aspects in information security such as data
confidentially, data integrity, authentication, and non-repudiation. Modern cryptography intersects the
disciplines of mathematics, computer science, and electrical engineering. Applications of cryptography
include ATM cards, computer passwords, and electronic commerce.
Basic example to understand how cryptography works is given below:
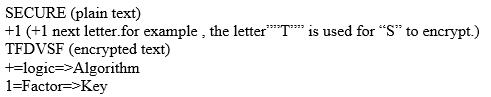
Which of the following choices true about cryptography?
parties (called adversaries). More generally, it is about constructing and analyzing protocols that overcome
the influence of adversaries and that are related to various aspects in information security such as data
confidentially, data integrity, authentication, and non-repudiation. Modern cryptography intersects the
disciplines of mathematics, computer science, and electrical engineering. Applications of cryptography
include ATM cards, computer passwords, and electronic commerce.
Basic example to understand how cryptography works is given below:
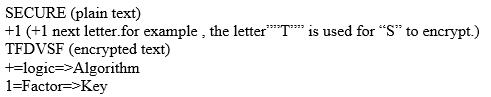
Which of the following choices true about cryptography?
Question 3
You just set up a security system in your network. In what kind of system would you find the following
string of characters used as a rule within its configuration? alert tcp any any ->192.168.100.0/24 21
(msg:""FTP on the network!"";)
string of characters used as a rule within its configuration? alert tcp any any ->192.168.100.0/24 21
(msg:""FTP on the network!"";)
Question 4
Which of the following tools will scan a network to perform vulnerability checks and compliance auditing?
Question 5
If an attacker uses the command SELECT*FROM user WHERE name = 'x' AND userid IS NULL; --'; which type of SQL injection attack is the attacker performing?

