Question 251
The "white box testing" methodology enforces what kind of restriction?
Question 252
A hacker named Jack is trying to compromise a bank's computer system. He needs to know the operating system of that computer to launch further attacks.
What process would help him?
What process would help him?
Question 253
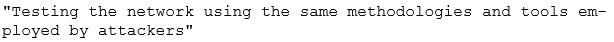
Identify the correct terminology that defines the above statement.
Question 254
What is the most common method to exploit the "Bash Bug" or "ShellShock" vulnerability?
Question 255
A company's Web development team has become aware of a certain type of security vulnerability in their
Web software. To mitigate the possibility of this vulnerability being exploited, the team wants to modify the
software requirements to disallow users from entering HTML as input into their Web application.
What kind of Web application vulnerability likely exists in their software?
Web software. To mitigate the possibility of this vulnerability being exploited, the team wants to modify the
software requirements to disallow users from entering HTML as input into their Web application.
What kind of Web application vulnerability likely exists in their software?

