Question 141
What did the following commands determine?
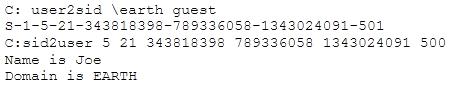

Question 142
You are a security officer of a company. You had an alert from IDS that indicates that one PC on your Intranet is connected to a blacklisted IP address (C2 Server) on the Internet. The IP address was blacklisted just before the alert. You are starting an investigation to roughly analyze the severity of the situation. Which of the following is appropriate to analyze?
Question 143
Shiela is an information security analyst working at HiTech Security Solutions. She is performing service version discovery using Nmap to obtain information about the running services and their versions on a target system.
Which of the following Nmap options must she use to perform service version discovery on the target host?
Which of the following Nmap options must she use to perform service version discovery on the target host?
Question 144
What is the role of test automation in security testing?
Question 145
Bill has been hired as a penetration tester and cyber security auditor for a major credit card company. Which information security standard is most applicable to his role?

