Question 61
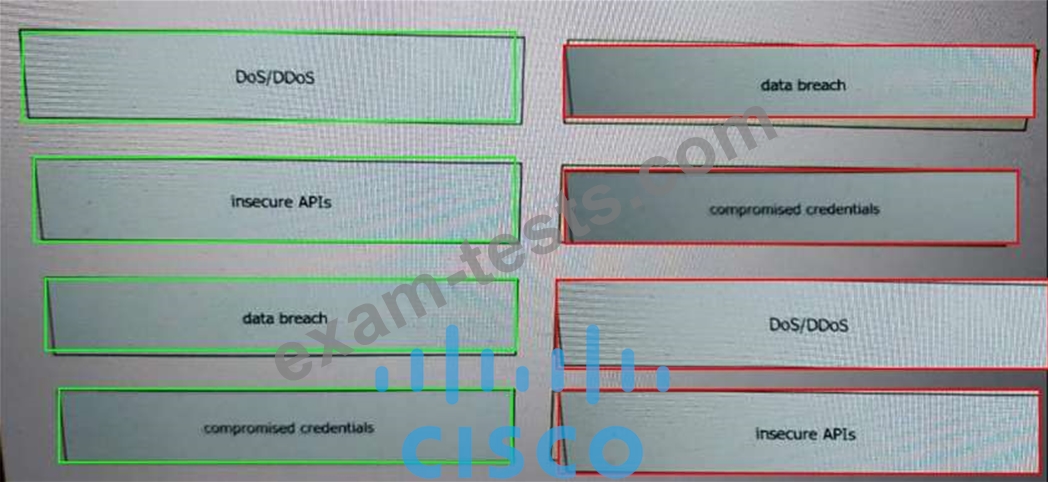
Drag and drop the threats from the left onto examples of that threat on the right


Question 62
What is the result of running the crypto isakmp key ciscXXXXXXXX address 172.16.0.0 command?
Question 63
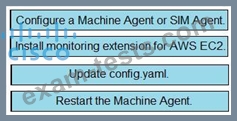
Drag and drop the steps from the left into the correct order on the right to enable AppDynamics to monitor an EC2 instance in Amazon Web Services.


Question 64
Refer to the exhibit.
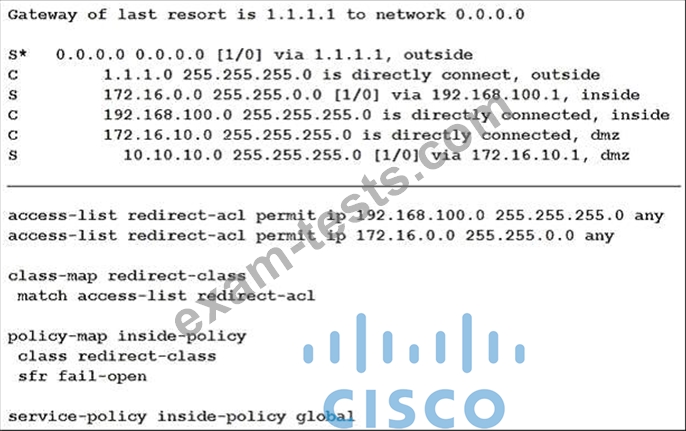
What is a result of the configuration?

What is a result of the configuration?
Question 65
An organization has two systems in their DMZ that have an unencrypted link between them for communication.
The organization does not have a defined password policy and uses several default accounts on the systems.
The application used on those systems also have not gone through stringent code reviews. Which vulnerability would help an attacker brute force their way into the systems?
The organization does not have a defined password policy and uses several default accounts on the systems.
The application used on those systems also have not gone through stringent code reviews. Which vulnerability would help an attacker brute force their way into the systems?