Question 281
Refer to the exhibit.
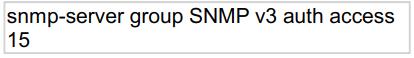
What does the number 15 represent in this configuration?
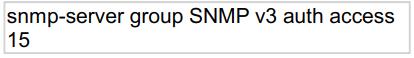
What does the number 15 represent in this configuration?
Question 282
Which statement about IOS zone-based firewalls is true?
Question 283
Which direction do attackers encode data in DNS requests during exfiltration using DNS tunneling?
Question 284
An organization has a requirement to collect full metadata information about the traffic going through their AWS cloud services They want to use this information for behavior analytics and statistics Which two actions must be taken to implement this requirement? (Choose two.)
Question 285
With Cisco AMP for Endpoints, which option shows a list of all files that have been executed in your environment?

