- Home
- Cisco Certification
- 350-701 Exam
- Cisco.350-701.v2022-10-19.q571 Practice Test
Question 31
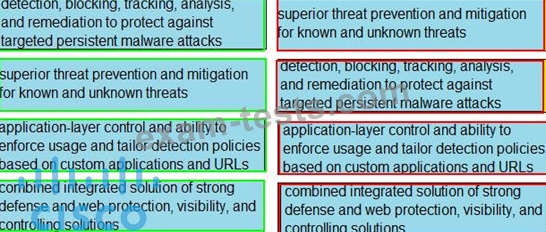
Drag and drop the capabilities from the left onto the correct technologies on the right.
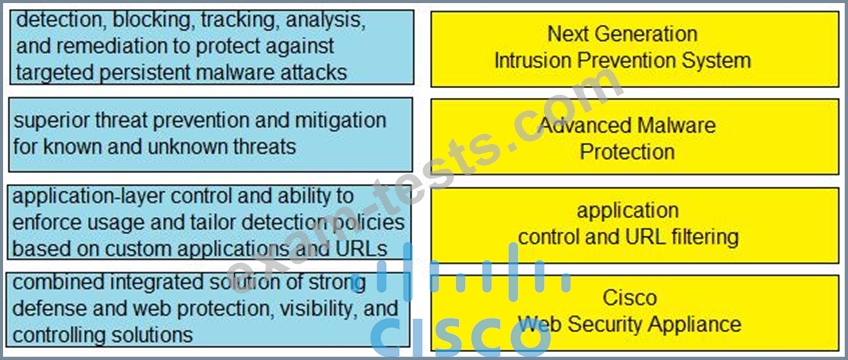

Correct Answer:
Question 32
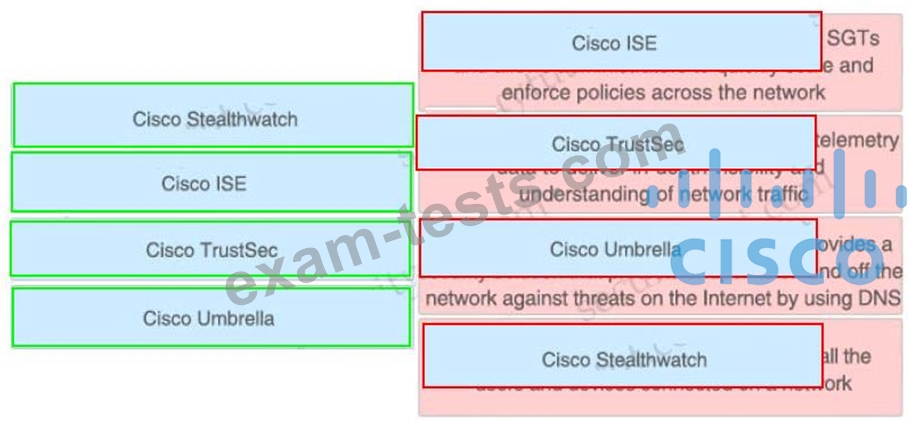
Drag and drop the solutions from the left onto the solution's benefits on the right.
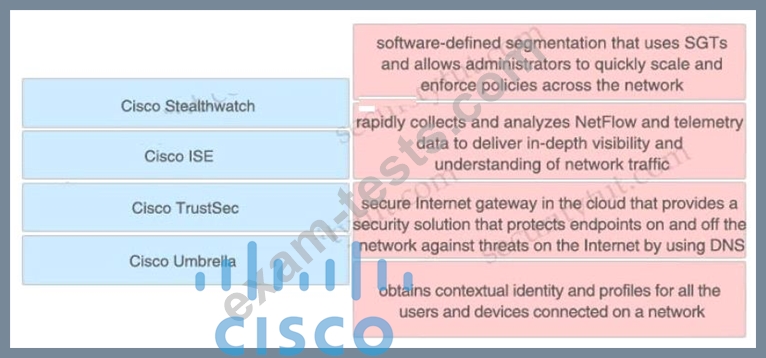

Correct Answer:
Question 33
What are the two most commonly used authentication factors in multifactor authentication? (Choose two)
Correct Answer: A,D
Multi-factor Authentication (MFA) is an authentication method that requires the user to provide two or more verification factors to gain access to a resource. MFA requires means of verification that unauthorized users won't have. Proper multi-factor authentication uses factors from at least two different categories. MFA methods: + Knowledge - usually a password - is the most commonly used tool in MFA solutions. However, despite their simplicity, passwords have become a security problem and slow down productivity. + Physical factors - also called possession factors-use tokens, such as a USB dongle or a portable device, that generate a temporary QR (quick response) code. Mobile phones are commonly used, as they have the advantage of being readily available in most situations. + Inherent - This category includes biometrics like fingerprint, face, and retina scans. As technology advances, it may also include voice ID or other behavioral inputs like keystroke metrics. Because inherent factors are reliably unique, always present, and secure, this category shows promise. + Location-based and time-based - Authentication systems can use GPS coordinates, network parameters, and metadata for the network in use, and device recognition for MFA. Adaptive authentication combines these data points with historical or contextual user data. A time factor in conjunction with a location factor could detect an attacker attempting to authenticate in Europe when the user was last authenticated in California an hour prior, for example. + Time-based one-time password (TOTP) - This is generally used in 2FA but could apply to any MFA method where a second step is introduced dynamically at login upon completing a first step. The wait for a second step-in which temporary passcodes are sent by SMS or email-is usually brief, and the process is easy to use for a wide range of users and devices. This method is currently widely used. + Social media - In this case a user grants permission for a website to use their social media username and password for login. This provide an easy login process, and one generally available to all users. + Risk-based authentication - Sometimes called adaptive multi-factor authentication, this method combines adaptive authentication and algorithms that calculate risk and observe the context of specific login requests. The goal of this method is to reduce redundant logins and provide a more user-friendly workflow. + Push-based 2FA - Push-based 2FA improves on SMS and TOTP 2FA by adding additional layers of security while improving ease of use. It confirms a user's identity with multiple factors of authentication that other methods cannot. Because push-based 2FA sends notifications through data networks like cellular or Wi-Fi, users must have data access on their mobile devices to use the 2FA functionality. Reference: https://www.cisco.com/c/en/us/products/security/what-is-multi-factor-authentication.html The two most popular authentication factors are knowledge and inherent (including biometrics like fingerprint, face, and retina scans. Biometrics is used commonly in mobile devices).
verification factors to gain access to a resource. MFA requires means of verification that unauthorized users won't have.
Proper multi-factor authentication uses factors from at least two different categories.
MFA methods:
+ Knowledge - usually a password - is the most commonly used tool in MFA solutions. However, despite their simplicity, passwords have become a security problem and slow down productivity.
+ Physical factors - also called possession factors-use tokens, such as a USB dongle or a portable device, that generate a temporary QR (quick response) code. Mobile phones are commonly used, as they have the advantage of being readily available in most situations.
+ Inherent - This category includes biometrics like fingerprint, face, and retina scans. As technology advances, it may also include voice ID or other behavioral inputs like keystroke metrics. Because inherent factors are reliably unique, always present, and secure, this category shows promise.
+ Location-based and time-based - Authentication systems can use GPS coordinates, network parameters, and metadata for the network in use, and device recognition for MFA. Adaptive authentication combines these data points with historical or contextual user data.
A time factor in conjunction with a location factor could detect an attacker attempting to authenticate in Europe when the user was last authenticated in California an hour prior, for example.
+ Time-based one-time password (TOTP) - This is generally used in 2FA but could apply to any MFA method where a second step is introduced dynamically at login upon completing a first step. The wait for a second step-in which temporary passcodes are sent by SMS or email-is usually brief, and the process is easy to use for a wide range of users and devices. This method is currently widely used.
+ Social media - In this case a user grants permission for a website to use their social media username and password for login. This provide an easy login process, and one generally available to all users.
+ Risk-based authentication - Sometimes called adaptive multi-factor authentication, this method combines adaptive authentication and algorithms that calculate risk and observe the context of specific login requests.
The goal of this method is to reduce redundant logins and provide a more user-friendly workflow.
+ Push-based 2FA - Push-based 2FA improves on SMS and TOTP 2FA by adding additional layers of security while improving ease of use. It confirms a user's identity with multiple factors of authentication that other methods cannot. Because push-based 2FA sends notifications through data networks like cellular or Wi-Fi, users must have data access on their mobile devices to use the 2FA functionality.
Reference:
The two most popular authentication factors are knowledge and inherent (including biometrics like fingerprint, Multi-factor Authentication (MFA) is an authentication method that requires the user to provide two or more verification factors to gain access to a resource. MFA requires means of verification that unauthorized users won't have. Proper multi-factor authentication uses factors from at least two different categories. MFA methods: + Knowledge - usually a password - is the most commonly used tool in MFA solutions. However, despite their simplicity, passwords have become a security problem and slow down productivity. + Physical factors - also called possession factors-use tokens, such as a USB dongle or a portable device, that generate a temporary QR (quick response) code. Mobile phones are commonly used, as they have the advantage of being readily available in most situations. + Inherent - This category includes biometrics like fingerprint, face, and retina scans. As technology advances, it may also include voice ID or other behavioral inputs like keystroke metrics. Because inherent factors are reliably unique, always present, and secure, this category shows promise. + Location-based and time-based - Authentication systems can use GPS coordinates, network parameters, and metadata for the network in use, and device recognition for MFA. Adaptive authentication combines these data points with historical or contextual user data. A time factor in conjunction with a location factor could detect an attacker attempting to authenticate in Europe when the user was last authenticated in California an hour prior, for example. + Time-based one-time password (TOTP) - This is generally used in 2FA but could apply to any MFA method where a second step is introduced dynamically at login upon completing a first step. The wait for a second step-in which temporary passcodes are sent by SMS or email-is usually brief, and the process is easy to use for a wide range of users and devices. This method is currently widely used. + Social media - In this case a user grants permission for a website to use their social media username and password for login. This provide an easy login process, and one generally available to all users. + Risk-based authentication - Sometimes called adaptive multi-factor authentication, this method combines adaptive authentication and algorithms that calculate risk and observe the context of specific login requests. The goal of this method is to reduce redundant logins and provide a more user-friendly workflow. + Push-based 2FA - Push-based 2FA improves on SMS and TOTP 2FA by adding additional layers of security while improving ease of use. It confirms a user's identity with multiple factors of authentication that other methods cannot. Because push-based 2FA sends notifications through data networks like cellular or Wi-Fi, users must have data access on their mobile devices to use the 2FA functionality. Reference: https://www.cisco.com/c/en/us/products/security/what-is-multi-factor-authentication.html The two most popular authentication factors are knowledge and inherent (including biometrics like fingerprint, face, and retina scans. Biometrics is used commonly in mobile devices).
verification factors to gain access to a resource. MFA requires means of verification that unauthorized users won't have.
Proper multi-factor authentication uses factors from at least two different categories.
MFA methods:
+ Knowledge - usually a password - is the most commonly used tool in MFA solutions. However, despite their simplicity, passwords have become a security problem and slow down productivity.
+ Physical factors - also called possession factors-use tokens, such as a USB dongle or a portable device, that generate a temporary QR (quick response) code. Mobile phones are commonly used, as they have the advantage of being readily available in most situations.
+ Inherent - This category includes biometrics like fingerprint, face, and retina scans. As technology advances, it may also include voice ID or other behavioral inputs like keystroke metrics. Because inherent factors are reliably unique, always present, and secure, this category shows promise.
+ Location-based and time-based - Authentication systems can use GPS coordinates, network parameters, and metadata for the network in use, and device recognition for MFA. Adaptive authentication combines these data points with historical or contextual user data.
A time factor in conjunction with a location factor could detect an attacker attempting to authenticate in Europe when the user was last authenticated in California an hour prior, for example.
+ Time-based one-time password (TOTP) - This is generally used in 2FA but could apply to any MFA method where a second step is introduced dynamically at login upon completing a first step. The wait for a second step-in which temporary passcodes are sent by SMS or email-is usually brief, and the process is easy to use for a wide range of users and devices. This method is currently widely used.
+ Social media - In this case a user grants permission for a website to use their social media username and password for login. This provide an easy login process, and one generally available to all users.
+ Risk-based authentication - Sometimes called adaptive multi-factor authentication, this method combines adaptive authentication and algorithms that calculate risk and observe the context of specific login requests.
The goal of this method is to reduce redundant logins and provide a more user-friendly workflow.
+ Push-based 2FA - Push-based 2FA improves on SMS and TOTP 2FA by adding additional layers of security while improving ease of use. It confirms a user's identity with multiple factors of authentication that other methods cannot. Because push-based 2FA sends notifications through data networks like cellular or Wi-Fi, users must have data access on their mobile devices to use the 2FA functionality.
Reference:
The two most popular authentication factors are knowledge and inherent (including biometrics like fingerprint, Multi-factor Authentication (MFA) is an authentication method that requires the user to provide two or more verification factors to gain access to a resource. MFA requires means of verification that unauthorized users won't have. Proper multi-factor authentication uses factors from at least two different categories. MFA methods: + Knowledge - usually a password - is the most commonly used tool in MFA solutions. However, despite their simplicity, passwords have become a security problem and slow down productivity. + Physical factors - also called possession factors-use tokens, such as a USB dongle or a portable device, that generate a temporary QR (quick response) code. Mobile phones are commonly used, as they have the advantage of being readily available in most situations. + Inherent - This category includes biometrics like fingerprint, face, and retina scans. As technology advances, it may also include voice ID or other behavioral inputs like keystroke metrics. Because inherent factors are reliably unique, always present, and secure, this category shows promise. + Location-based and time-based - Authentication systems can use GPS coordinates, network parameters, and metadata for the network in use, and device recognition for MFA. Adaptive authentication combines these data points with historical or contextual user data. A time factor in conjunction with a location factor could detect an attacker attempting to authenticate in Europe when the user was last authenticated in California an hour prior, for example. + Time-based one-time password (TOTP) - This is generally used in 2FA but could apply to any MFA method where a second step is introduced dynamically at login upon completing a first step. The wait for a second step-in which temporary passcodes are sent by SMS or email-is usually brief, and the process is easy to use for a wide range of users and devices. This method is currently widely used. + Social media - In this case a user grants permission for a website to use their social media username and password for login. This provide an easy login process, and one generally available to all users. + Risk-based authentication - Sometimes called adaptive multi-factor authentication, this method combines adaptive authentication and algorithms that calculate risk and observe the context of specific login requests. The goal of this method is to reduce redundant logins and provide a more user-friendly workflow. + Push-based 2FA - Push-based 2FA improves on SMS and TOTP 2FA by adding additional layers of security while improving ease of use. It confirms a user's identity with multiple factors of authentication that other methods cannot. Because push-based 2FA sends notifications through data networks like cellular or Wi-Fi, users must have data access on their mobile devices to use the 2FA functionality. Reference: https://www.cisco.com/c/en/us/products/security/what-is-multi-factor-authentication.html The two most popular authentication factors are knowledge and inherent (including biometrics like fingerprint, face, and retina scans. Biometrics is used commonly in mobile devices).
Question 34
Which type of data exfiltration technique encodes data in outbound DNS requests to specific servers and can be stopped by Cisco Umbrella?
Correct Answer: B
Question 35
A Cisco ESA administrator has been tasked with configuring the Cisco ESA to ensure there are no viruses before quarantined emails are delivered. In addition, delivery of mail from known bad mail servers must be prevented. Which two actions must be taken in order to meet these requirements? (Choose two)
Correct Answer: A,E
We should scan emails using AntiVirus signatures to make sure there are no viruses attached in emails. Note: A virus signature is the fingerprint of a virus. It is a set of unique data, or bits of code, that allow it to be identified. Antivirus software uses a virus signature to find a virus in a computer file system, allowing to detect, quarantine, and remove the virus. SenderBase is an email reputation service designed to help email administrators research senders, identify legitimate sources of email, and block spammers. When the Cisco ESA receives messages from known or highly reputable senders, it delivers them directly to the end user without any content scanning. However, when the Cisco ESA receives email messages from unknown or less reputable senders, it performs antispam and antivirus scanning. Reference: https://www.cisco.com/c/en/us/td/docs/security/esa/esa12-0/user_guide/ b_ESA_Admin_Guide_12_0/b_ESA_Admin_Guide_12_0_chapter_0100100.html -> Therefore Outbreak filters can be used to block emails from bad mail servers. Web servers and email gateways are generally located in the DMZ so Note: The recipient access table (RAT), not to be confused with remote-access Trojan (also RAT), is a Cisco ESA term that defines which recipients are accepted by a public listener.
Note: A virus signature is the fingerprint of a virus. It is a set of unique data, or bits of code, that allow it to be identified. Antivirus software uses a virus signature to find a virus in a computer file system, allowing to detect, quarantine, and remove the virus.
SenderBase is an email reputation service designed to help email administrators research senders, identify legitimate sources of email, and block spammers. When the Cisco ESA receives messages from known or highly reputable senders, it delivers them directly to the end user without any content scanning. However, when the Cisco ESA receives email messages from unknown or less reputable senders, it performs antispam and antivirus scanning.
Reference:
b_ESA_Admin_Guide_12_0/b_ESA_Admin_Guide_12_0_chapter_0100100.html
-> Therefore Outbreak filters can be used to block emails from bad mail servers.
Web servers and email gateways are generally located in the DMZ so
We should scan emails using AntiVirus signatures to make sure there are no viruses attached in emails. Note: A virus signature is the fingerprint of a virus. It is a set of unique data, or bits of code, that allow it to be identified. Antivirus software uses a virus signature to find a virus in a computer file system, allowing to detect, quarantine, and remove the virus. SenderBase is an email reputation service designed to help email administrators research senders, identify legitimate sources of email, and block spammers. When the Cisco ESA receives messages from known or highly reputable senders, it delivers them directly to the end user without any content scanning. However, when the Cisco ESA receives email messages from unknown or less reputable senders, it performs antispam and antivirus scanning. Reference: https://www.cisco.com/c/en/us/td/docs/security/esa/esa12-0/user_guide/ b_ESA_Admin_Guide_12_0/b_ESA_Admin_Guide_12_0_chapter_0100100.html -> Therefore Outbreak filters can be used to block emails from bad mail servers. Web servers and email gateways are generally located in the DMZ so Note: The recipient access table (RAT), not to be confused with remote-access Trojan (also RAT), is a Cisco ESA term that defines which recipients are accepted by a public listener.
Note: A virus signature is the fingerprint of a virus. It is a set of unique data, or bits of code, that allow it to be identified. Antivirus software uses a virus signature to find a virus in a computer file system, allowing to detect, quarantine, and remove the virus.
SenderBase is an email reputation service designed to help email administrators research senders, identify legitimate sources of email, and block spammers. When the Cisco ESA receives messages from known or highly reputable senders, it delivers them directly to the end user without any content scanning. However, when the Cisco ESA receives email messages from unknown or less reputable senders, it performs antispam and antivirus scanning.
Reference:
b_ESA_Admin_Guide_12_0/b_ESA_Admin_Guide_12_0_chapter_0100100.html
-> Therefore Outbreak filters can be used to block emails from bad mail servers.
Web servers and email gateways are generally located in the DMZ so
We should scan emails using AntiVirus signatures to make sure there are no viruses attached in emails. Note: A virus signature is the fingerprint of a virus. It is a set of unique data, or bits of code, that allow it to be identified. Antivirus software uses a virus signature to find a virus in a computer file system, allowing to detect, quarantine, and remove the virus. SenderBase is an email reputation service designed to help email administrators research senders, identify legitimate sources of email, and block spammers. When the Cisco ESA receives messages from known or highly reputable senders, it delivers them directly to the end user without any content scanning. However, when the Cisco ESA receives email messages from unknown or less reputable senders, it performs antispam and antivirus scanning. Reference: https://www.cisco.com/c/en/us/td/docs/security/esa/esa12-0/user_guide/ b_ESA_Admin_Guide_12_0/b_ESA_Admin_Guide_12_0_chapter_0100100.html -> Therefore Outbreak filters can be used to block emails from bad mail servers. Web servers and email gateways are generally located in the DMZ so Note: The recipient access table (RAT), not to be confused with remote-access Trojan (also RAT), is a Cisco ESA term that defines which recipients are accepted by a public listener.
- Other Version
- 1466Cisco.350-701.v2025-10-04.q562
- 1076Cisco.350-701.v2025-06-19.q238
- 1555Cisco.350-701.v2024-12-18.q472
- 2720Cisco.350-701.v2023-08-01.q405
- 3399Cisco.350-701.v2023-05-04.q372
- 2329Cisco.350-701.v2023-03-16.q218
- 7256Cisco.350-701.v2022-07-08.q453
- 4200Cisco.350-701.v2022-02-02.q204
- 116Cisco.Prepawaypdf.350-701.v2021-12-15.by.ellen.316q.pdf
- Latest Upload
- 126USGBC.LEED-AP-Homes.v2026-01-02.q36
- 115SAP.C-THR94-2505.v2026-01-02.q29
- 135MedicalProfessional.CHFM.v2026-01-01.q37
- 116SAP.C-BCSPM-2502.v2026-01-01.q9
- 118Microsoft.MB-335.v2026-01-01.q142
- 120SAP.C_THR70_2505.v2026-01-01.q55
- 157Salesforce.Financial-Services-Cloud.v2026-01-01.q121
- 183Fortinet.FCSS_SDW_AR-7.4.v2025-12-31.q73
- 162UiPath.UiPath-SAIAv1.v2025-12-30.q89
- 213HP.HPE0-V25.v2025-12-29.q138
[×]
Download PDF File
Enter your email address to download Cisco.350-701.v2022-10-19.q571 Practice Test

