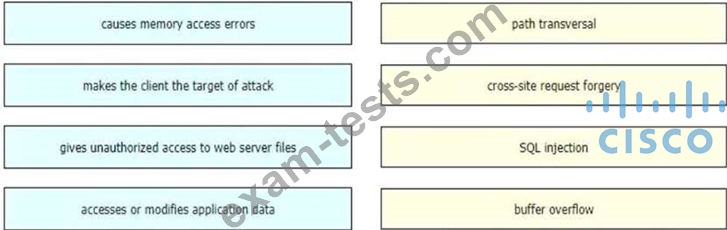
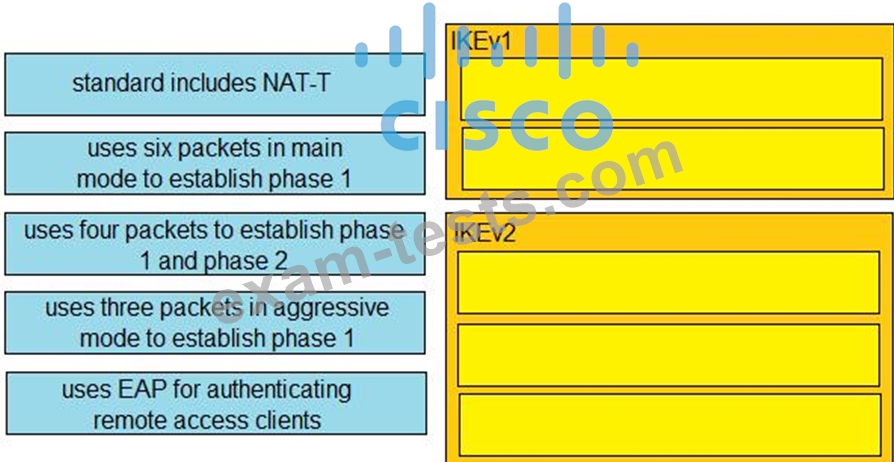
Which compliance status is shown when a configured posture policy requirement is not met?
Correct Answer: D
Explanation Posture is a service in Cisco Identity Services Engine (Cisco ISE) that allows you to check the state, also known as posture, of all the endpoints that are connecting to a network for compliance with corporate security policies. A posture policy is a collection of posture requirements that are associated with one or more identity groups and operating systems. Posture-policy requirements can be set to mandatory, optional, or audit types in posture policies. + If a mandatory requirement fails, the user will be moved to Non-Compliant state + If an optional requirement fails, the user is allowed to skip the specified optional requirements and the user is moved to Compliant state This Qdid not clearly specify the type of posture policy requirement (mandatory or optional) is not met so the user can be in Non-compliant or compliant state. But "noncompliant" is the best answer here. Reference: https://www.cisco.com/c/en/us/td/docs/security/ise/1-3/admin_guide/b_ise_admin_guide_13/ b_ise_admin_guide_sample_chapter_010111.html Posture is a service in Cisco Identity Services Engine (Cisco ISE) that allows you to check the state, also known as posture, of all the endpoints that are connecting to a network for compliance with corporate security policies.
A posture policy is a collection of posture requirements that are associated with one or more identity groups and operating systems.
Posture-policy requirements can be set to mandatory, optional, or audit types in posture policies.
+ If a mandatory requirement fails, the user will be moved to Non-Compliant state
+ If an optional requirement fails, the user is allowed to skip the specified optional requirements and the user is moved to Compliant state This Qdid not clearly specify the type of posture policy requirement (mandatory or optional) is not met so the user can be in Non-compliant or compliant state. But "noncompliant" is the best answer here.
Reference:
Explanation Posture is a service in Cisco Identity Services Engine (Cisco ISE) that allows you to check the state, also known as posture, of all the endpoints that are connecting to a network for compliance with corporate security policies. A posture policy is a collection of posture requirements that are associated with one or more identity groups and operating systems. Posture-policy requirements can be set to mandatory, optional, or audit types in posture policies. + If a mandatory requirement fails, the user will be moved to Non-Compliant state + If an optional requirement fails, the user is allowed to skip the specified optional requirements and the user is moved to Compliant state This Qdid not clearly specify the type of posture policy requirement (mandatory or optional) is not met so the user can be in Non-compliant or compliant state. But "noncompliant" is the best answer here. Reference: https://www.cisco.com/c/en/us/td/docs/security/ise/1-3/admin_guide/b_ise_admin_guide_13/ b_ise_admin_guide_sample_chapter_010111.html