Question 136
Refer to the exhibit.
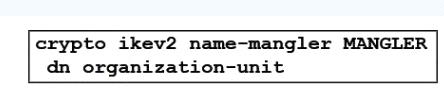
An engineer is implementing a certificate based VPN. What is the result of the existing configuration?

An engineer is implementing a certificate based VPN. What is the result of the existing configuration?
Question 137
Which security solution protects users leveraging DNS-layer security?
Question 138
In which form of attack is alternate encoding, such as hexadecimal representation, most often observed?
Question 139
Refer to the exhibit. When creating an access rule for URL filtering, a network engineer adds certain categories and individual URLs to block. What is the result of the configuration?
Question 140
When configuring ISAKMP for IKEv1 Phase1 on a Cisco IOS router, an administrator needs to input the command crypto isakmp key cisco address 0.0.0.0. The administrator is not sure what the IP addressing in this command issued for. What would be the effect of changing the IP address from 0.0.0.0 to 1.2.3.4?

