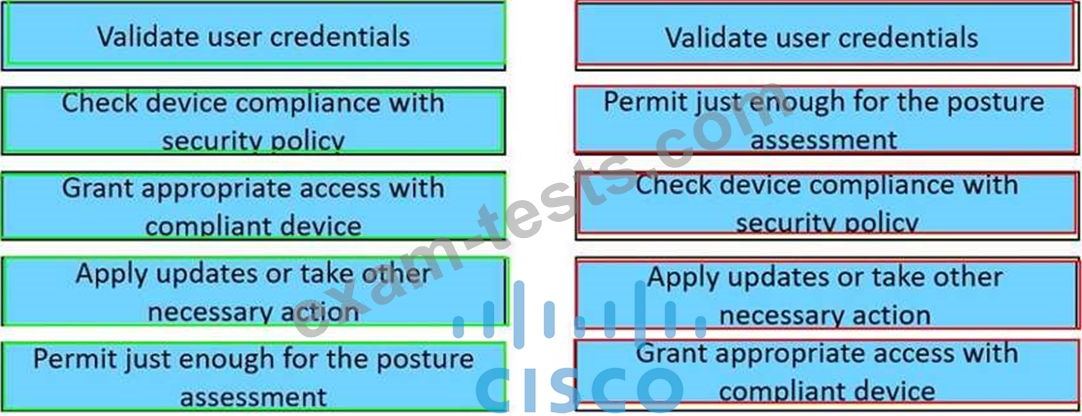
Question 56
Drag and drop the posture assessment flow actions from the left into a sequence on the right.


Question 57
In which type of attack does the attacker insert their machine between two hosts that are communicating with each other?
Question 58
A network engineer has entered the snmp-server user andy myv3 auth sha cisco priv aes 256 cisc0383320506 command and needs to send SNMP information to a host at 10.255.254.1. Which command achieves this goal?
Question 59
In which two ways does Easy Connect help control network access when used with Casco TrustSec? Choose two.)
Question 60
Which DevSecOps implementation process gives a weekly or daily update instead of monthly or quarterly in the applications?