Question 161
Refer to the exhibit.
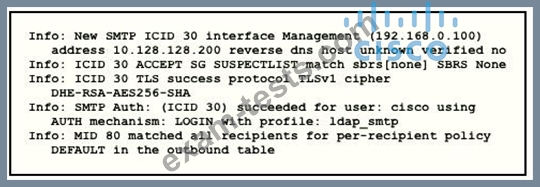
Which type of authentication is in use?

Which type of authentication is in use?
Question 162
Which feature is supported when deploying Cisco ASAv within AWS public cloud?
Question 163
Which endpoint protection and detection feature performs correlation of telemetry, files, and intrusion events that are flagged as possible active breaches?
Question 164
Which algorithm is an NGE hash function?
Question 165
A company identified a phishing vulnerability during a pentest What are two ways the company can protect employees from the attack? (Choose two.)

