Question 546
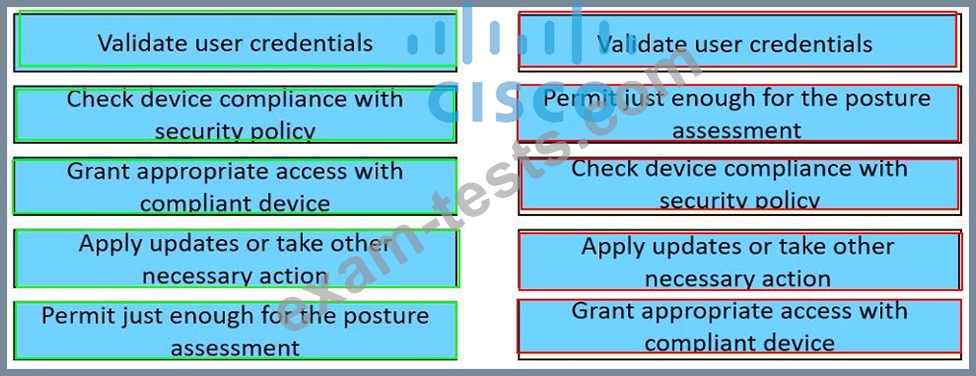
Drag and drop the capabilities from the left onto the correct technologies on the right.

Question 547
An organization has two systems in their DMZ that have an unencrypted link between them for communication. The organization does not have a defined password policy and uses several default accounts on the systems. The application used on those systems also have not gone through stringent code reviews. Which vulnerability would help an attacker brute force their way into the systems?
Question 548
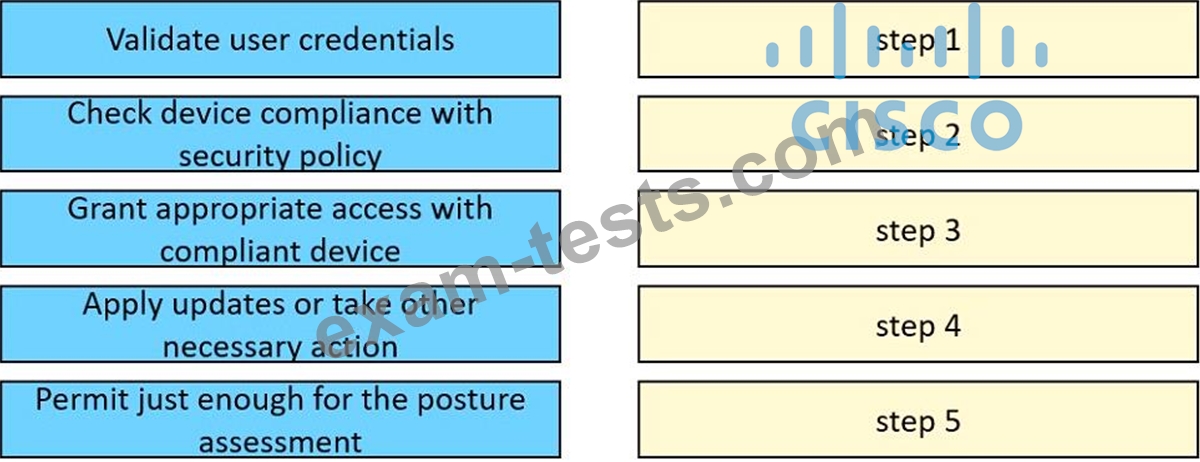
Drag and drop the posture assessment flow actions from the left into a sequence on the right.

Question 549
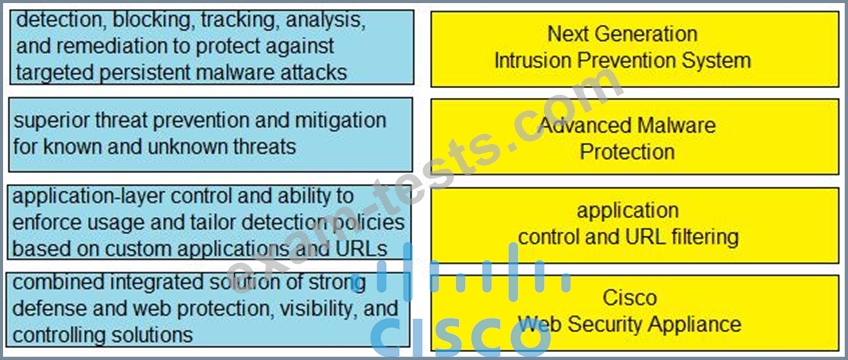
Which Cisco solution extends network visibility, threat detection, and analytics to public cloud environments?
Question 550
Which attack is preventable by Cisco ESA but not by the Cisco WSA?