Question 131
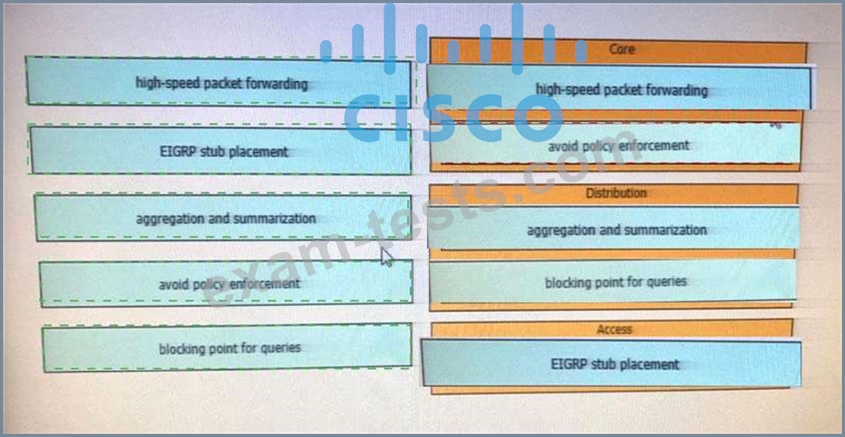
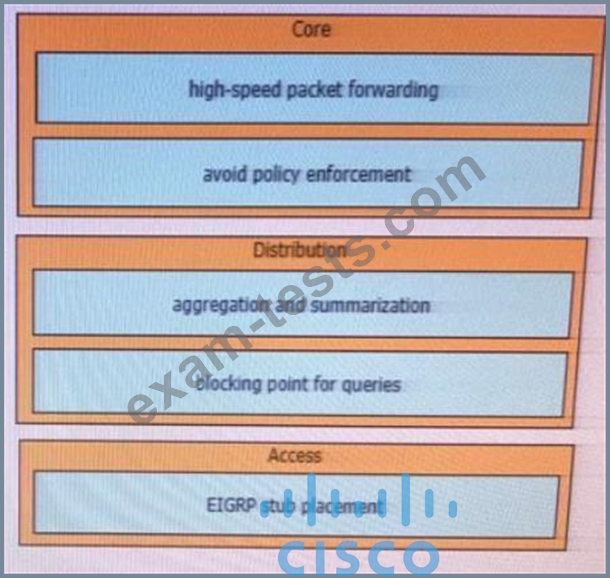
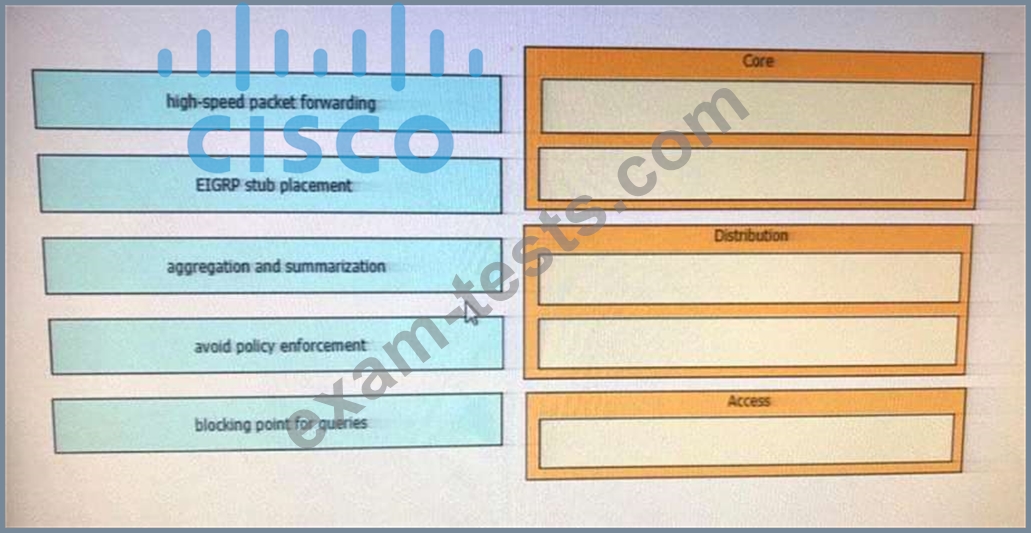
Drag and drop the EIGRP design considerations from the left onto the corresponding hierarchical layer characteristics on the right

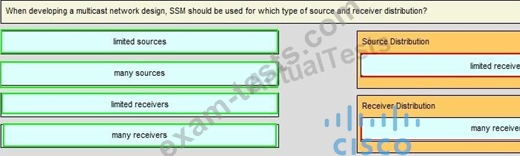
Question 132
DRAG DROP
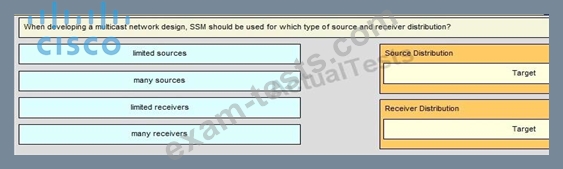

Question 133
Refer to the exhibit.
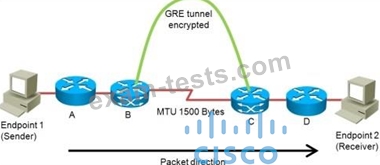
You are planning the design of an encrypted WAN. IP packets will be transferred over encrypted GRE tunnels between routers B and C.
The packet size is limited to a maximum of 1500 bytes inside the WAN between routers B and C.
If endpoint 1 tries to send 1500-byte IP packets to endpoint 2, in what three ways will the network design handle the fragmentation in three different possible network configurations?
(Choose three.)

You are planning the design of an encrypted WAN. IP packets will be transferred over encrypted GRE tunnels between routers B and C.
The packet size is limited to a maximum of 1500 bytes inside the WAN between routers B and C.
If endpoint 1 tries to send 1500-byte IP packets to endpoint 2, in what three ways will the network design handle the fragmentation in three different possible network configurations?
(Choose three.)
Question 134
Refer to the exhibit.

Refer to the exhibit. A route health injector is deployed on the network to monitor reachable services. The route health injector injects /32 prefixes into BGP with the next hop of 98.18.0.2. These /32 prefixes are not being installed into the RIB of router. A which BGP feature must be deployed to make sure this design works?

Refer to the exhibit. A route health injector is deployed on the network to monitor reachable services. The route health injector injects /32 prefixes into BGP with the next hop of 98.18.0.2. These /32 prefixes are not being installed into the RIB of router. A which BGP feature must be deployed to make sure this design works?
Question 135
A company is planning to deploy high-availability cluster support for their servers in a collapsed core data center design. Which issue should be a concern with this design?