Question 26
Which tunneling mechanism provides confidentiality and tunneling capabilities?
Question 27
You are designing a fabricpath network that connects to a spine-and-leaf topology using Layer 2 IS-IS as the IGP. The solution must be able to detect changes in the network topology and calculate loop-free paths to other nodes in the network that are being used as top-of -rack switches, which three characteristics of this fabricpath design solution are true? (Choose three)
Question 28
When a design calls for spanning VLANs across a campus network, what are two issues that need to be addressed in the design? (Choose two.)
Question 29
Refer to the exhibit.
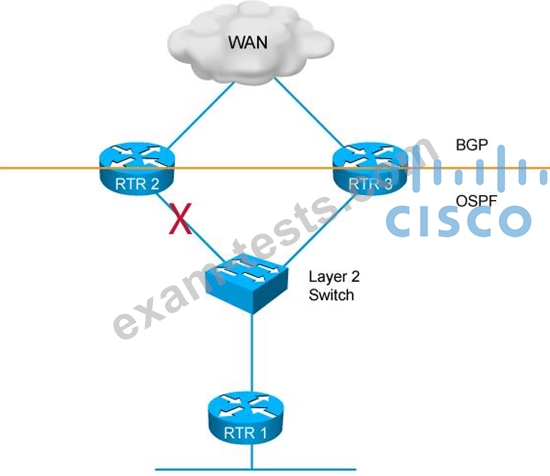
RTR 1 uses RTR 2 as the primary WAN exit point. When a failure occurs in the link connected to RTR 2 LAN, it takes about 40 seconds for RTR 1 to use the backup path via
RTR 3.
Which two mechanisms can be used independently to improve the failure detection time to
1 second or less when RTR 1 failover to RTR3? (Choose two.)

RTR 1 uses RTR 2 as the primary WAN exit point. When a failure occurs in the link connected to RTR 2 LAN, it takes about 40 seconds for RTR 1 to use the backup path via
RTR 3.
Which two mechanisms can be used independently to improve the failure detection time to
1 second or less when RTR 1 failover to RTR3? (Choose two.)
Question 30
20
You are evaluating convergence characteristics of various interior gateway protocols for a new network design. Which technology allows link-state routing protocols to calculate paths to destination prefixes that are functionally similar to feasible successors in Enhanced Interior Gateway Routing Protocol?
You are evaluating convergence characteristics of various interior gateway protocols for a new network design. Which technology allows link-state routing protocols to calculate paths to destination prefixes that are functionally similar to feasible successors in Enhanced Interior Gateway Routing Protocol?

