Question 71
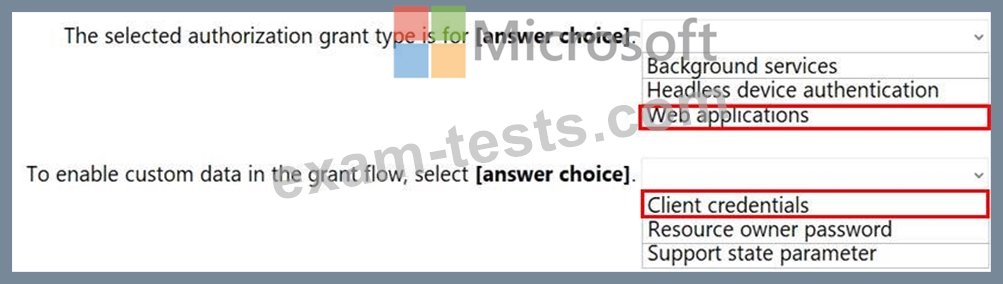
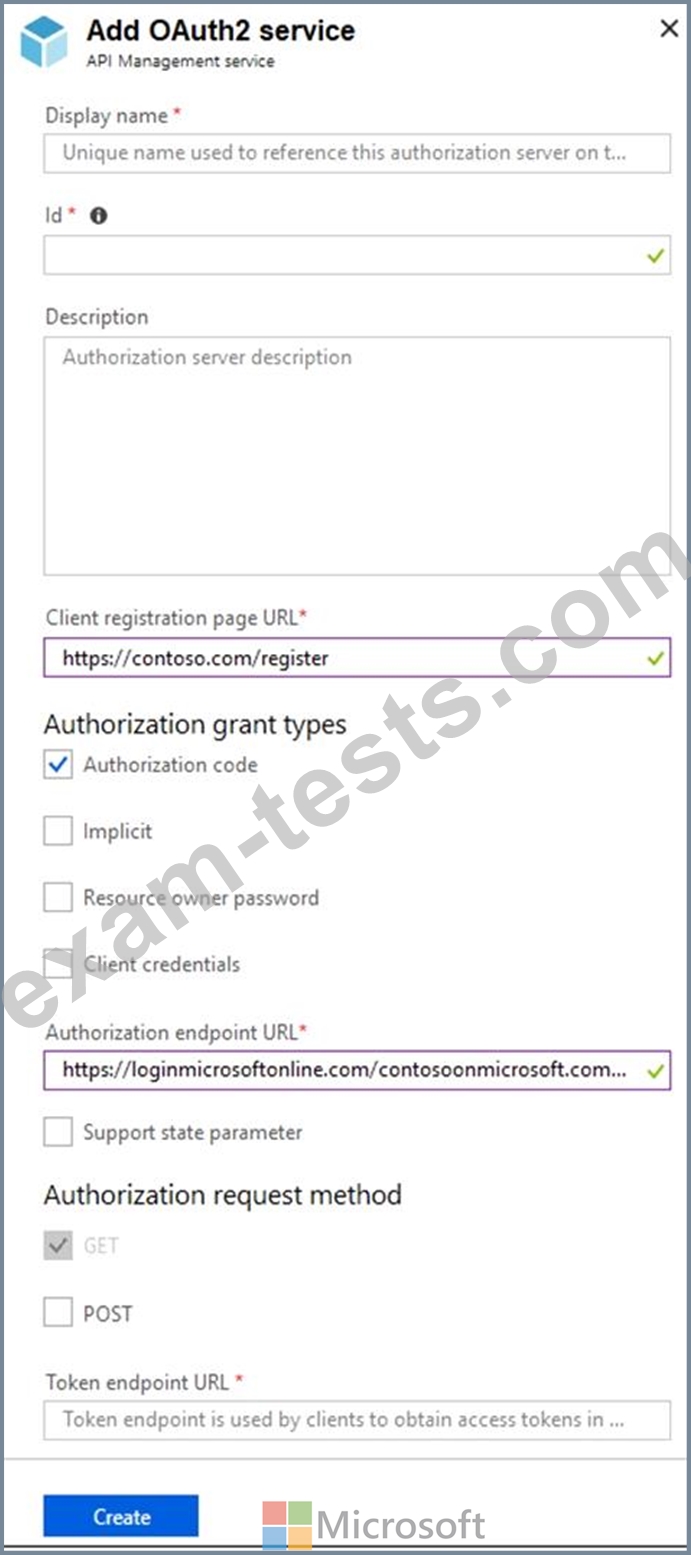
You configure OAuth2 authorization in API Management as shown in the following exhibit.
Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic.
NOTE: Each correct selection is worth one point.
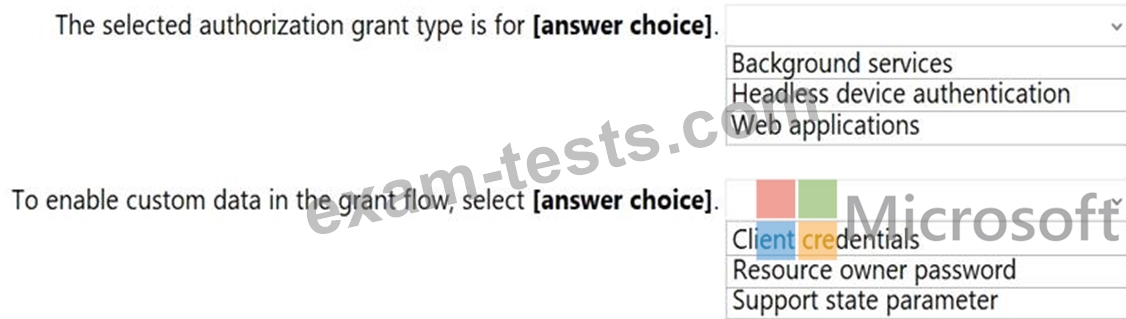

Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic.
NOTE: Each correct selection is worth one point.

Question 72
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You plan to deploy multiple instances of an Azure web app across several Azure regions.
You need to design an access solution for the app. The solution must meet the following replication requirements:
Support rate limiting.
Balance requests between all instances.
Ensure that users can access the app in the event of a regional outage.
Solution: You use Azure Traffic Manager to provide access to the app.
Does this meet the goal?
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You plan to deploy multiple instances of an Azure web app across several Azure regions.
You need to design an access solution for the app. The solution must meet the following replication requirements:
Support rate limiting.
Balance requests between all instances.
Ensure that users can access the app in the event of a regional outage.
Solution: You use Azure Traffic Manager to provide access to the app.
Does this meet the goal?
Question 73
You have 70 TB of files on your on-premises file server.
You need to recommend solution for importing data to Azure. The solution must minimize cost.
What Azure service should you recommend?
You need to recommend solution for importing data to Azure. The solution must minimize cost.
What Azure service should you recommend?
Question 74
You are designing a solution for a stateless front-end application named Application1. Application1 will be hosted on two Azure virtual machines named VM1 and VM2.
You plan to load balance connections to VM1 and VM2 from the Internet by using one Azure load balancer.
You need to recommend the minimum number of required public IP addresses.
How many public IP addresses should you recommend using for each resource? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
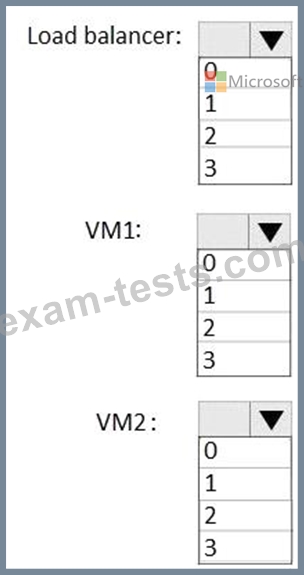
You plan to load balance connections to VM1 and VM2 from the Internet by using one Azure load balancer.
You need to recommend the minimum number of required public IP addresses.
How many public IP addresses should you recommend using for each resource? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

Question 75
You have an Azure SQL Database elastic pool.
You need to monitor the resource usage of the elastic pool for anomalous database activity based on historic usage patterns. The solution must minimize administrative effort.
What should you include in the solution?
You need to monitor the resource usage of the elastic pool for anomalous database activity based on historic usage patterns. The solution must minimize administrative effort.
What should you include in the solution?
Premium Bundle
Newest AZ-304 Exam PDF Dumps shared by BraindumpsPass.com for Helping Passing AZ-304 Exam! BraindumpsPass.com now offer the updated AZ-304 exam dumps, the BraindumpsPass.com AZ-304 exam questions have been updated and answers have been corrected get the latest BraindumpsPass.com AZ-304 pdf dumps with Exam Engine here: