Question 71
You have five .NET Core applications that run on 10 Azure virtual machines in the same subscription.
You need to recommend a solution to ensure that the applications can authenticate by using the same Azure Active Directory (Azure AD) identity. The solution must meet the following requirements:
Ensure that the applications can authenticate only when running on the 10 virtual machines.
Minimize administrative effort.
What should you include in the recommendation? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
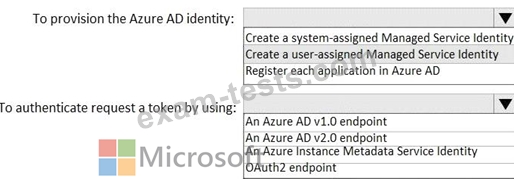
You need to recommend a solution to ensure that the applications can authenticate by using the same Azure Active Directory (Azure AD) identity. The solution must meet the following requirements:
Ensure that the applications can authenticate only when running on the 10 virtual machines.
Minimize administrative effort.
What should you include in the recommendation? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

Question 72
You have an Azure subscription that contains 300 Azure virtual machines that run Windows Server 2016.
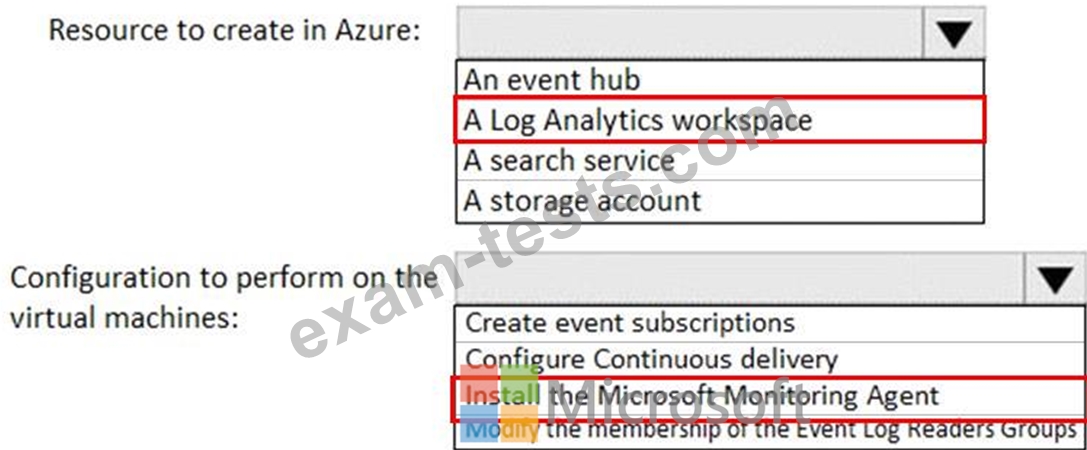
You need to centrally monitor all warning events in the System logs of the virtual machines.
What should you include in the solutions? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

You need to centrally monitor all warning events in the System logs of the virtual machines.
What should you include in the solutions? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

Question 73
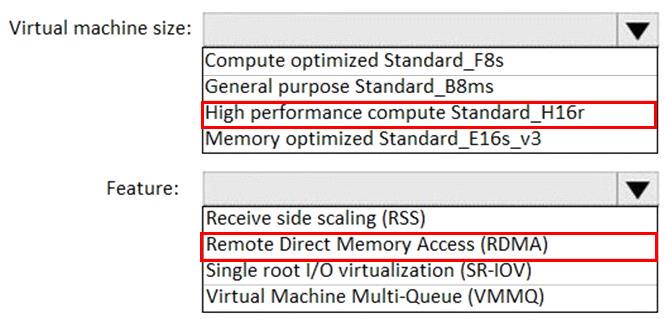
You plan to deploy a network-intensive application to several Azure virtual machines.
You need to recommend a solution that meets the following requirements:
Minimizes the use of the virtual machine processors to transfer data
Minimizes network latency
Which virtual machine size and feature should you use? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
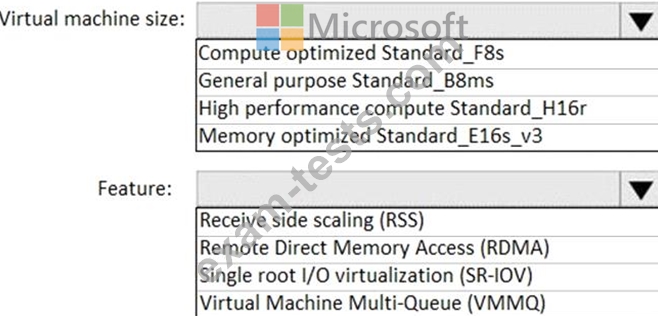
You need to recommend a solution that meets the following requirements:
Minimizes the use of the virtual machine processors to transfer data
Minimizes network latency
Which virtual machine size and feature should you use? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

Question 74
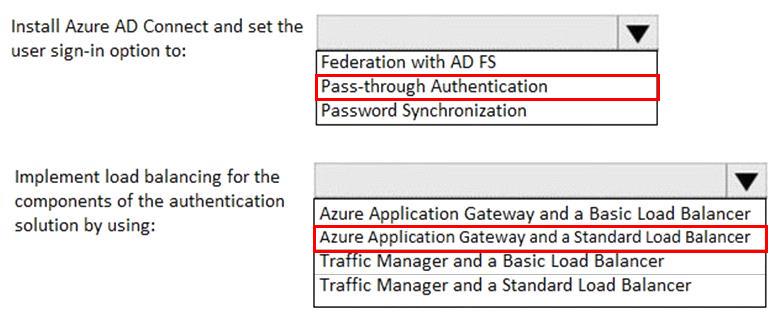
You need to recommend a solution for the users at Contoso to authenticate to the cloud-based services and the Azure AD-integrated applications.
What should you include in the recommendation? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

What should you include in the recommendation? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

Question 75
You nave 200 resource groups across 20 Azure subscriptions.
Your company's security policy states that the security administrator most verify all assignments of the Owner role for the subscriptions and resource groups once a month. All assignments that are not approved try the security administrator must be removed automatically. The security administrator must be prompted every month to perform the verification.
What should you use to implement the security policy?
Your company's security policy states that the security administrator most verify all assignments of the Owner role for the subscriptions and resource groups once a month. All assignments that are not approved try the security administrator must be removed automatically. The security administrator must be prompted every month to perform the verification.
What should you use to implement the security policy?