Question 21
You need to meet the technical requirements for Cluster3.
What should you include in the solution?
What should you include in the solution?
Question 22
You have five Azure virtual machines.
You need to collect performance data and Windows Event logs from the virtual machines. The data collected must be sent to an Azure Storage account.
What should you install on the virtual machines?
You need to collect performance data and Windows Event logs from the virtual machines. The data collected must be sent to an Azure Storage account.
What should you install on the virtual machines?
Question 23
You have two file servers named Server1 and Server2 that run Windows Server. Server1 contains a shared folder named Data. Data contains 10 TB of data.
You plan to decommission Server1.
You need to migrate the files from Data to a new shared folder on Server2. The solution must meet the following requirements:
* Ensure that share, file, and folder permissions are copied.
* After the initial copy occurs, ensure that changes in \\Server1\Data can be synced to the destination
* without initiating a full copy.
* Minimize administrative effort.
What should you use?
You plan to decommission Server1.
You need to migrate the files from Data to a new shared folder on Server2. The solution must meet the following requirements:
* Ensure that share, file, and folder permissions are copied.
* After the initial copy occurs, ensure that changes in \\Server1\Data can be synced to the destination
* without initiating a full copy.
* Minimize administrative effort.
What should you use?
Question 24
You have an on-premises Active Directory Domain Services (AD DS) domain that syncs with an Azure Active Directory (Azure AD) tenant.
The AD DS domain contains a domain controller named DC1. DC1 does NOT have internet access.
You need to configure password security for on-premises users. The solution must meet the following requirements:
* Prevent the users from using known weak passwords.
* Prevent the users from using the company name in passwords.
What should you do? To answer, drag the appropriate configurations to the correct targets. Each configuration may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.
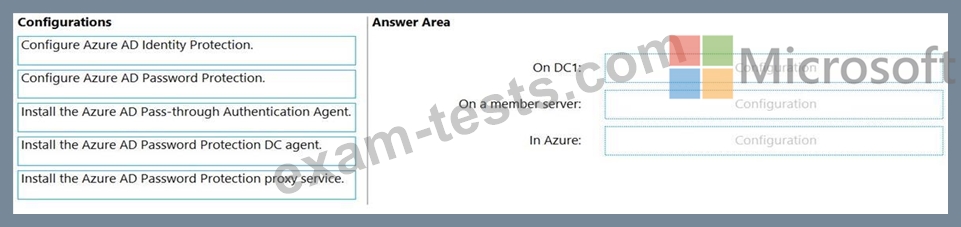
The AD DS domain contains a domain controller named DC1. DC1 does NOT have internet access.
You need to configure password security for on-premises users. The solution must meet the following requirements:
* Prevent the users from using known weak passwords.
* Prevent the users from using the company name in passwords.
What should you do? To answer, drag the appropriate configurations to the correct targets. Each configuration may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.

Question 25
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a server named Server1 that runs Windows Server.
You need to ensure that only specific applications can modify the data in protected folders on Server1.
Solution: From Virus & threat protection, you configure Tamper Protection.
Does this meet the goal?
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a server named Server1 that runs Windows Server.
You need to ensure that only specific applications can modify the data in protected folders on Server1.
Solution: From Virus & threat protection, you configure Tamper Protection.
Does this meet the goal?


