Question 241
An enterprise solution requires a central monitoring platform to address the growing networks of various departments and agencies that connect to the network. The current vendor products are not adequate due to the growing number of heterogeneous devices. Which of the following is the primary concern?
Question 242
A remote user reports the inability to authenticate to the VPN concentrator. During troubleshooting, a security administrate captures an attempted authentication and discovers the following being presented by the user's VPN client:
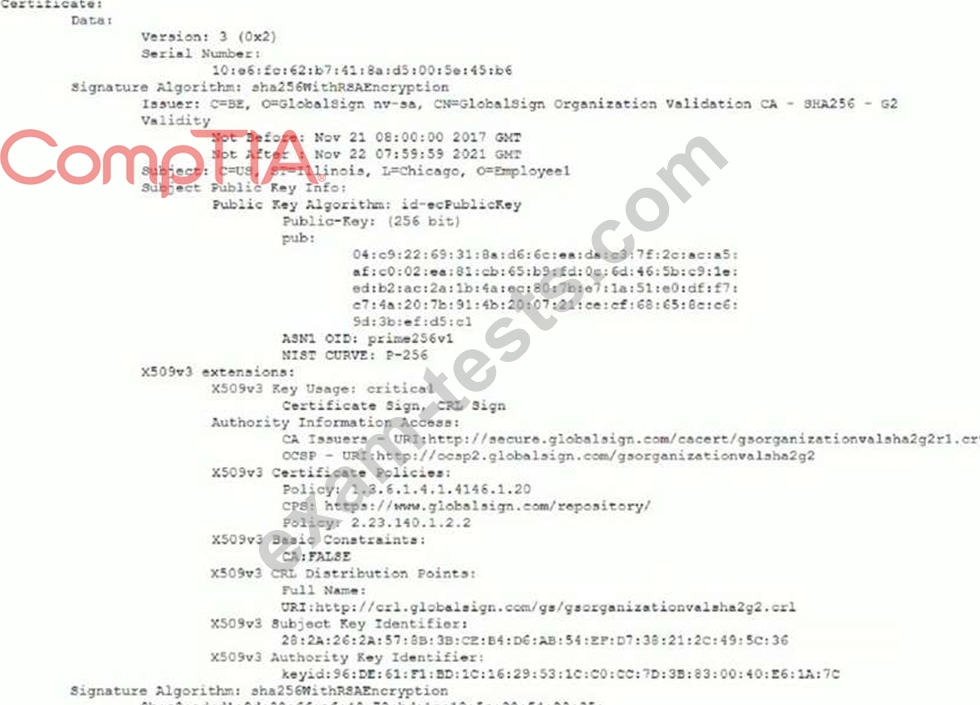
Which of the following BEST describes the reason the user is unable to connect to the VPN service?

Which of the following BEST describes the reason the user is unable to connect to the VPN service?
Question 243
An organization's network security administrator has been using an SSH connection to manage switches and routers for several years. After attempting to connect to a router, an alert appears on the terminal emulation software, warning that the SSH key has changed.
After confirming the administrator is using the typical workstation and the router has not been replaced, which of the following are the MOST likely explanations for the warning message? (Choose two.)
After confirming the administrator is using the typical workstation and the router has not been replaced, which of the following are the MOST likely explanations for the warning message? (Choose two.)
Question 244
A project manager is working with system owners to develop maintenance windows for system pathing and upgrades in a cloud-based PaaS environment. Management has indicated one maintenance windows will be authorized per month, but clients have stated they require quarterly maintenance windows to meet their obligations. Which of the following documents should the project manager review?
Question 245
An information security officer is responsible for one secure network and one office network. Recent intelligence suggests there is an opportunity for attackers to gain access to the secure network due to similar login credentials across networks. To determine the users who should change their information, the information security officer uses a tool to scan a file with hashed values on both networks and receives the following data:
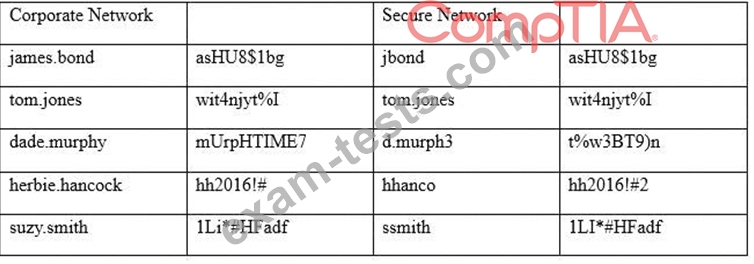
Which of the following tools was used to gather this information from the hashed values in the file?

Which of the following tools was used to gather this information from the hashed values in the file?

