Question 76
A company created an external application for its customers. A security researcher now reports that the application has a serious LDAP injection vulnerability that could be leveraged to bypass authentication and authorization.
Which of the following actions would BEST resolve the issue? (Choose two.)
Which of the following actions would BEST resolve the issue? (Choose two.)
Question 77
A security analyst is reviewing the following output:
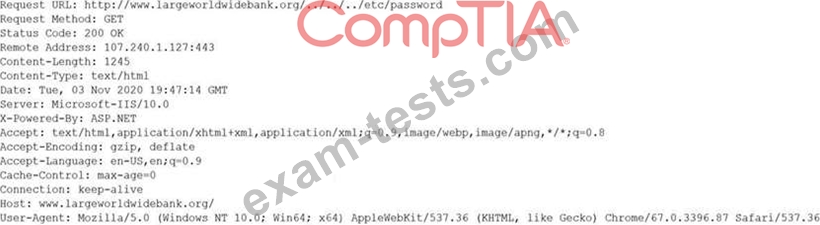
Which of the following would BEST mitigate this type of attack?

Which of the following would BEST mitigate this type of attack?
Question 78
A security engineer thinks the development team has been hard-coding sensitive environment variables in its code.
Which of the following would BEST secure the company's CI/CD pipeline?
Which of the following would BEST secure the company's CI/CD pipeline?
Question 79
A systems administrator is preparing to run a vulnerability scan on a set of information systems in the organization. The systems administrator wants to ensure that the targeted systems produce accurate information especially regarding configuration settings.
Which of the following scan types will provide the systems administrator with the MOST accurate information?
Which of the following scan types will provide the systems administrator with the MOST accurate information?

