Question 1
____ is the degree to which a set of inherent characteristics fulfills requirements.
Question 2
In a risk assessment exercise of a software implementation program, the business analyst (BA) has successfully computed the probability of occurrence (POC) and the cost of impact for each of the identified risks as follows:
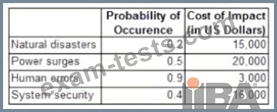
Which of the following will have the highest negative impact to value?

Which of the following will have the highest negative impact to value?
Question 3
Which of the following processes measures the maturity level of the security program?
Question 4
A health insurance provider undertakes enhancements to its mobile application platform and finalizes the following capabilities as part of the scope of the next release:
L Ability to integrate online maps and global positioning system (GPS) technology with the mobile application in real time to display location of service providers in the subscriber's that participate in the subscriber's plan network.
Ability for the subscriber to lookup the service providers by specifying either a postal code on a search area radius in miles.
III. Ability for the subscriber to initial the download of fee information for one more service providers in a single request.
Through requirements workshops the business analyst elicits the following detailed business requirements:
1. The company's mobile application platform must support real time integration with the following third party systems:
1. GPS System
2. Postal Code Validation
2. The service providers available for selection must participate in the subscriber's medical plan network as of the current system date.
3. The map display shall highlight the boundary of the search area with a dotted yellow line.
4. The extent and shape of he searches area shall be determined based on one of the following user choices:
A postal code-Subscriber location acquired from GPS shall be used to determine and populate........................
Which of the following is the appropriate technique to define communication flows between the Postal Code validation system with other systems?
L Ability to integrate online maps and global positioning system (GPS) technology with the mobile application in real time to display location of service providers in the subscriber's that participate in the subscriber's plan network.
Ability for the subscriber to lookup the service providers by specifying either a postal code on a search area radius in miles.
III. Ability for the subscriber to initial the download of fee information for one more service providers in a single request.
Through requirements workshops the business analyst elicits the following detailed business requirements:
1. The company's mobile application platform must support real time integration with the following third party systems:
1. GPS System
2. Postal Code Validation
2. The service providers available for selection must participate in the subscriber's medical plan network as of the current system date.
3. The map display shall highlight the boundary of the search area with a dotted yellow line.
4. The extent and shape of he searches area shall be determined based on one of the following user choices:
A postal code-Subscriber location acquired from GPS shall be used to determine and populate........................
Which of the following is the appropriate technique to define communication flows between the Postal Code validation system with other systems?
Question 5
A business analyst (BA) is working on a payment system (PS) implementation. A set of systems which should interact with a new system has been identified. The business analyst defined that a user with role of "Supervisor" in the PS must pass a two-factor authentication before an execution of the functions: "Change system parameters" and "Set up new supervisor." A user must have the role of "Supervisor" to use the standard functions "Send mail notification" or "Send SMS notification".
The BA defined the following use cases:
* "Change system parameters"
* "Setup new supervisor"
* "Send mail notification"
* "Send SMS notification"
* "Send notification"
* "Pass a two-factor authentication"
The BA wants to create a Use Case diagram.
What standard relationship should be defined between "Change system parameters", "Setup new supervisor" and "Pass a two-factor authentication"?
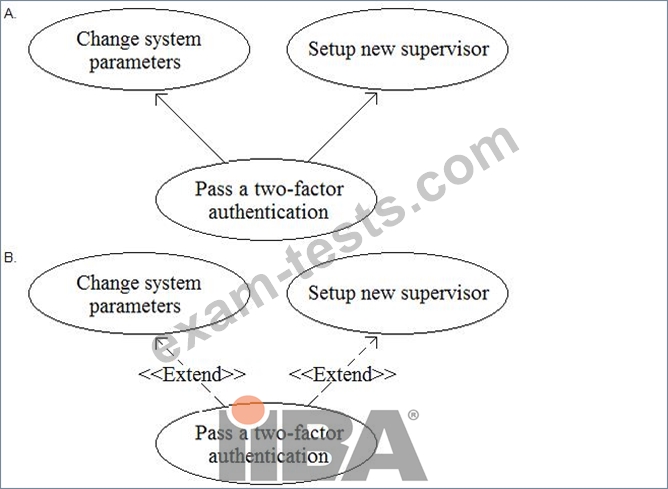
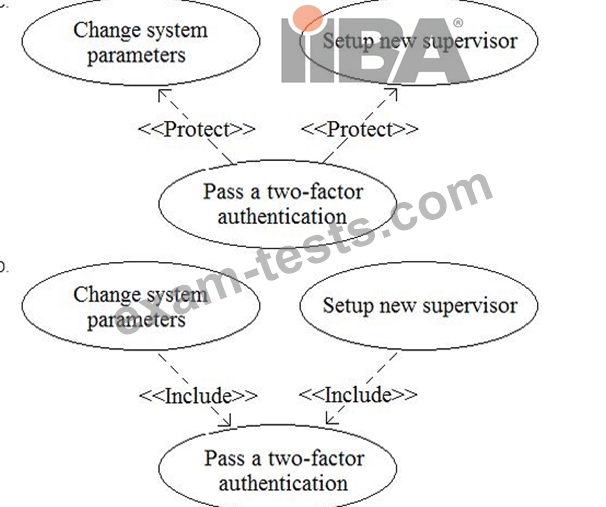
The BA defined the following use cases:
* "Change system parameters"
* "Setup new supervisor"
* "Send mail notification"
* "Send SMS notification"
* "Send notification"
* "Pass a two-factor authentication"
The BA wants to create a Use Case diagram.
What standard relationship should be defined between "Change system parameters", "Setup new supervisor" and "Pass a two-factor authentication"?




Is this correct