Question 266
E-mail traffic from the Internet is routed via firewall-1 to the mail gateway. Mail is routed from the mail gateway, via firewall-2, to the mail recipients in the internal network. Other traffic is not allowed. For example, the firewalls do not allow direct traffic from the Internet to the internal network.
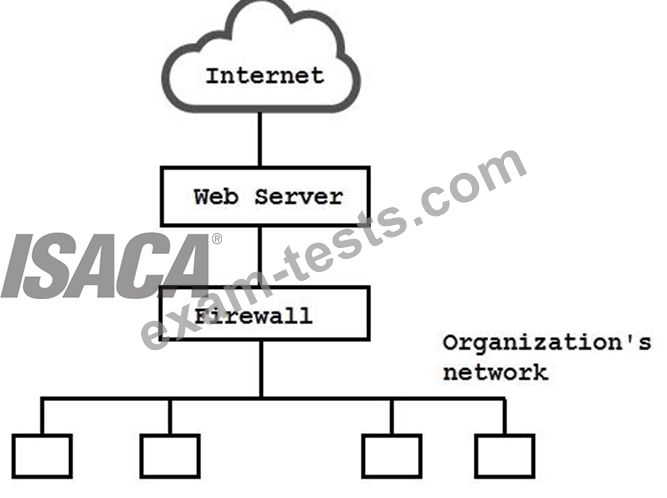
The intrusion detection system (IDS) detects traffic for the internal network that did not originate from the mail gateway. The FIRST action triggered by the IDS should be to:

The intrusion detection system (IDS) detects traffic for the internal network that did not originate from the mail gateway. The FIRST action triggered by the IDS should be to:
Question 267
A transaction processing system interfaces with the general ledger. Data analytics has identified that some transactions are being recorded twice in the general ledger. While management states a system fix has been implemented, what should the IS auditor recommend to validate the interface is working in the future?
Question 268
Prior to the of acquired software into production, it is MOST important that the IS auditor review the:
Question 269
Which of the following is an advantage of using electronic data interchange (EDI)?
Question 270
An IS auditor finds that, in accordance with IS policy, IDs of terminated users are deactivated within 90 days of termination. The IS auditor should:

