Question 171
Which of the following components of a risk assessment is MOST helpful to management in determining the level of risk mitigation to apply?
Question 172
A core system fails a week after a scheduled update, causing an outage that impacts service. Which of the following is MOST important for incident management to focus on when addressing the issue?
Question 173
An organization has recently acquired and implemented intelligent-agent software for granting loans to customers. During the post-implementation review, which of the following is the MOST important procedure for the IS auditor to perform?
Question 174
E-mail traffic from the Internet is routed via firewall-1 to the mail gateway. Mail is routed from the mail gateway, via firewall-2, to the mail recipients in the internal network. Other traffic is not allowed. For example, the firewalls do not allow direct traffic from the Internet to the internal network.
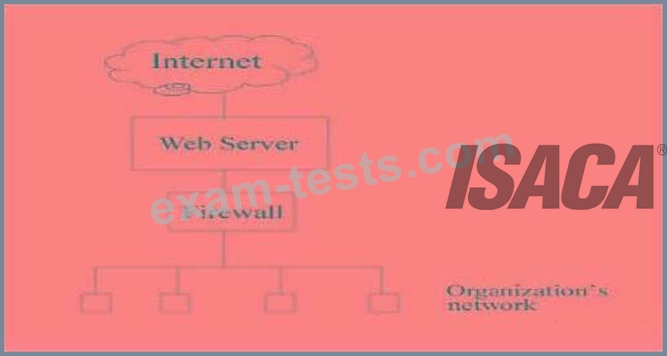
The intrusion detection system (IDS) detects traffic for the internal network that did not originate from the mail gateway. The FIRST action triggered by the IDS should be to:

The intrusion detection system (IDS) detects traffic for the internal network that did not originate from the mail gateway. The FIRST action triggered by the IDS should be to:
Question 175
An IS audit manager has been asked to perform a quality review on an audit that the same manager also supervised. Which of the following is (he manager's BEST response to this situation?

