Question 26
Management has requested a post-implementation review of a newly implemented purchasing package to determine to what extent business requirements are being met. Which of the following is MOST likely to be assessed?
Question 27
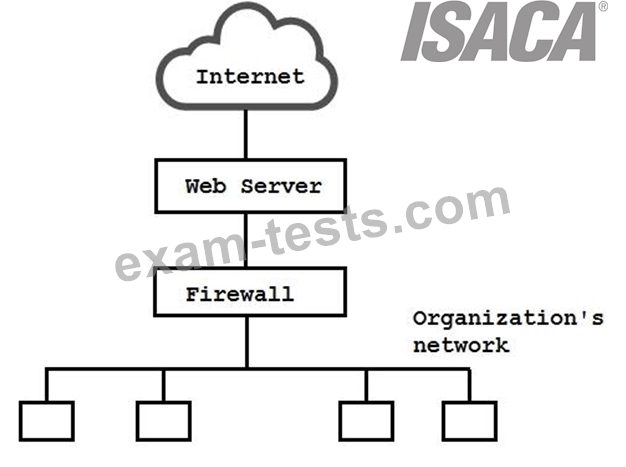
To detect attack attempts that the firewall is unable to recognize, an IS auditor should recommend placing a network intrusion detection system (IDS) between the:

Question 28
Which of the following tests is MOST likely to detect an error in one subroutine resulting from a recent change in another subroutine?
Question 29
Iptables is based on which of the following frameworks?
Question 30
An IS auditor has discovered that a key control has been designed properly but is not operating effectively.
Which of the following should the auditor do NEXT?
Which of the following should the auditor do NEXT?

