- Home
- The SecOps Group Certification
- CNSP Exam
- TheSecOpsGroup.CNSP.v2025-09-08.q20 Practice Test
Question 11
Which of the following is not a DDoS attack?
Correct Answer: D
DDoS (Distributed Denial of Service) attacks aim to overwhelm a target's resources with excessive traffic, disrupting availability, whereas other attack types target different goals.
Why D is correct: Brute force attacks focus on guessing credentials (e.g., passwords) to gain unauthorized access, not on denying service. CNSP classifies it as an authentication attack, not a DDoS method.
Why other options are incorrect:
A: SYN Flood exhausts TCP connection resources, a classic DDoS attack.
B: NTP Amplification leverages amplified responses to flood targets, a DDoS technique.
C: UDP Flood overwhelms a system with UDP packets, another DDoS method.
Why D is correct: Brute force attacks focus on guessing credentials (e.g., passwords) to gain unauthorized access, not on denying service. CNSP classifies it as an authentication attack, not a DDoS method.
Why other options are incorrect:
A: SYN Flood exhausts TCP connection resources, a classic DDoS attack.
B: NTP Amplification leverages amplified responses to flood targets, a DDoS technique.
C: UDP Flood overwhelms a system with UDP packets, another DDoS method.
Question 12
What types of attacks are phishing, spear phishing, vishing, scareware, and watering hole?
Correct Answer: C
Social engineering exploits human psychology to manipulate individuals into divulging sensitive information, granting access, or performing actions that compromise security. Unlike technical exploits, it targets the "human factor," often bypassing technical defenses. The listed attacks fit this category:
Phishing: Mass, untargeted emails (e.g., fake bank alerts) trick users into entering credentials on spoofed sites. Uses tactics like urgency or trust (e.g., typosquatting domains).
Spear Phishing: Targeted phishing against specific individuals/organizations (e.g., CEO fraud), leveraging reconnaissance (e.g., LinkedIn data) for credibility.
Vishing (Voice Phishing): Phone-based attacks (e.g., fake tech support calls) extract info via verbal manipulation. Often spoofs caller ID.
Scareware: Fake alerts (e.g., "Your PC is infected!" pop-ups) scare users into installing malware or paying for bogus fixes. Exploits fear and urgency.
Watering Hole: Compromises trusted websites frequented by a target group (e.g., industry forums), infecting visitors via drive-by downloads. Relies on habitual trust.
Technical Details:
Delivery: Email (phishing), VoIP (vishing), web (watering hole/scareware).
Payloads: Credential theft, malware (e.g., trojans), or financial fraud.
Mitigation: User training, email filters (e.g., DMARC), endpoint protection.
Security Implications: Social engineering accounts for ~90% of breaches (e.g., Verizon DBIR 2023), as it exploits unpatchable human error. CNSP likely emphasizes awareness (e.g., phishing simulations) and layered defenses (e.g., MFA).
Why other options are incorrect:
A . Probes: Reconnaissance techniques (e.g., port scanning) to identify vulnerabilities, not manipulation-based like these attacks.
B . Insider threats: Malicious actions by authorized users (e.g., data theft by employees), not external human-targeting tactics.
D . Ransomware: A malware type (e.g., WannaCry) that encrypts data for ransom, not a manipulation method-though phishing often delivers it.
Real-World Context: The 2016 DNC hack used spear phishing to steal credentials, showing social engineering's potency.
Phishing: Mass, untargeted emails (e.g., fake bank alerts) trick users into entering credentials on spoofed sites. Uses tactics like urgency or trust (e.g., typosquatting domains).
Spear Phishing: Targeted phishing against specific individuals/organizations (e.g., CEO fraud), leveraging reconnaissance (e.g., LinkedIn data) for credibility.
Vishing (Voice Phishing): Phone-based attacks (e.g., fake tech support calls) extract info via verbal manipulation. Often spoofs caller ID.
Scareware: Fake alerts (e.g., "Your PC is infected!" pop-ups) scare users into installing malware or paying for bogus fixes. Exploits fear and urgency.
Watering Hole: Compromises trusted websites frequented by a target group (e.g., industry forums), infecting visitors via drive-by downloads. Relies on habitual trust.
Technical Details:
Delivery: Email (phishing), VoIP (vishing), web (watering hole/scareware).
Payloads: Credential theft, malware (e.g., trojans), or financial fraud.
Mitigation: User training, email filters (e.g., DMARC), endpoint protection.
Security Implications: Social engineering accounts for ~90% of breaches (e.g., Verizon DBIR 2023), as it exploits unpatchable human error. CNSP likely emphasizes awareness (e.g., phishing simulations) and layered defenses (e.g., MFA).
Why other options are incorrect:
A . Probes: Reconnaissance techniques (e.g., port scanning) to identify vulnerabilities, not manipulation-based like these attacks.
B . Insider threats: Malicious actions by authorized users (e.g., data theft by employees), not external human-targeting tactics.
D . Ransomware: A malware type (e.g., WannaCry) that encrypts data for ransom, not a manipulation method-though phishing often delivers it.
Real-World Context: The 2016 DNC hack used spear phishing to steal credentials, showing social engineering's potency.
Question 13
What is the response from a closed TCP port which is behind a firewall?
Correct Answer: D
TCP (Transmission Control Protocol) uses a three-way handshake (SYN, SYN-ACK, ACK) to establish connections, as per RFC 793. When a client sends a SYN packet to a port:
Open Port: The server responds with SYN-ACK.
Closed Port (no firewall): The server sends an RST (Reset) packet, often with ACK, to terminate the attempt immediately.
However, when a firewall is present, its configuration dictates the response. Modern firewalls typically operate in stealth mode, using a "drop" rule for closed ports rather than a "reject" rule:
Drop: Silently discards the packet without replying, resulting in no response. The client experiences a timeout (e.g., 30 seconds), as no feedback is provided.
Reject: Sends an RST or ICMP "Port Unreachable," but this is less common for security reasons, as it confirms the firewall's presence.
For a closed TCP port behind a firewall, "no response" (drop) is the standard behavior in secure configurations, minimizing information leakage to attackers. This aligns with CNSP's focus on firewall best practices to obscure network topology during port scanning (e.g., with Nmap).
Why other options are incorrect:
A . A FIN and an ACK packet: FIN-ACK is used to close an established TCP connection gracefully (e.g., after data transfer), not to respond to an initial SYN on a closed port.
B . RST and an ACK packet: RST-ACK is the host's response to a closed port without a firewall. A firewall's drop rule overrides this by silently discarding the packet.
C . A SYN and an ACK packet: SYN-ACK indicates an open port accepting a connection, the opposite of a closed port scenario.
Real-World Context: Tools like Nmap interpret "no response" as "filtered" (firewall likely present) vs. "closed" (RST received), aiding in firewall detection.
Open Port: The server responds with SYN-ACK.
Closed Port (no firewall): The server sends an RST (Reset) packet, often with ACK, to terminate the attempt immediately.
However, when a firewall is present, its configuration dictates the response. Modern firewalls typically operate in stealth mode, using a "drop" rule for closed ports rather than a "reject" rule:
Drop: Silently discards the packet without replying, resulting in no response. The client experiences a timeout (e.g., 30 seconds), as no feedback is provided.
Reject: Sends an RST or ICMP "Port Unreachable," but this is less common for security reasons, as it confirms the firewall's presence.
For a closed TCP port behind a firewall, "no response" (drop) is the standard behavior in secure configurations, minimizing information leakage to attackers. This aligns with CNSP's focus on firewall best practices to obscure network topology during port scanning (e.g., with Nmap).
Why other options are incorrect:
A . A FIN and an ACK packet: FIN-ACK is used to close an established TCP connection gracefully (e.g., after data transfer), not to respond to an initial SYN on a closed port.
B . RST and an ACK packet: RST-ACK is the host's response to a closed port without a firewall. A firewall's drop rule overrides this by silently discarding the packet.
C . A SYN and an ACK packet: SYN-ACK indicates an open port accepting a connection, the opposite of a closed port scenario.
Real-World Context: Tools like Nmap interpret "no response" as "filtered" (firewall likely present) vs. "closed" (RST received), aiding in firewall detection.
Question 14
Which one of the following is a phishing email?

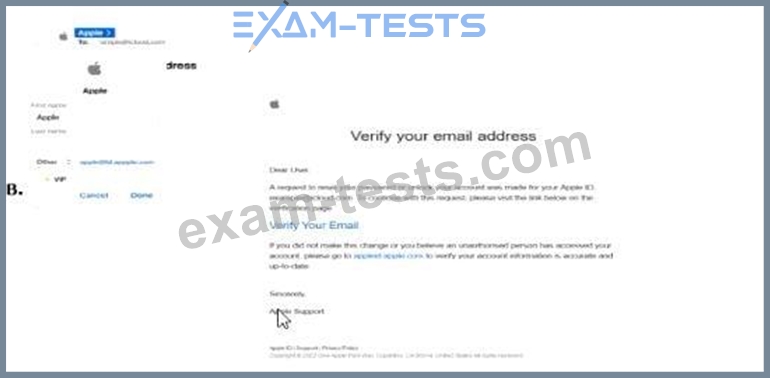


Correct Answer: B
The screenshot shows an email labeled "B" with the subject "Verify your email address" purportedly from Apple. To determine if this is a phishing email, we need to analyze its content and characteristics against common phishing indicators as outlined in CNSP documentation. Since option A is not provided in the screenshot, we will evaluate email B and infer the context for A.
Analysis of Email B:
Sender and Branding: The email claims to be from "Apple Support" and includes an Apple logo, which is a common tactic to establish trust. However, phishing emails often impersonate legitimate brands like Apple to deceive users.
Subject and Content: The subject "Verify your email address" and the body requesting the user to verify their email by clicking a link ("Verify Your Email") are typical of phishing attempts. Legitimate companies like Apple may send verification emails, but the tone and context here raise suspicion.
Link Presence: The email contains a clickable link ("Verify Your Email") that is purportedly for email verification. The screenshot does not show the URL, but phishing emails often include malicious links that lead to fake login pages to steal credentials. CNSP emphasizes that unsolicited requests to click links for verification are a red flag.
Urgency and Vague Instructions: The email includes a statement, "If you did not make this change or believe an unauthorized person has accessed your account, click here to cancel and secure your account." This creates a sense of urgency, a common phishing tactic to prompt immediate action without critical thinking.
Generic Greeting: The email starts with "Dear User," a generic greeting often used in phishing emails. Legitimate companies like Apple typically personalize emails with the user's name.
Suspicious Elements: The email mentions "your Apple ID ([email protected])," which is a placeholder rather than a specific email address, further indicating a mass phishing campaign rather than a targeted, legitimate communication.
Phishing Indicators (per CNSP):
CNSP documentation on phishing identification lists several red flags:
Unsolicited requests for verification or account updates.
Generic greetings (e.g., "Dear User" instead of a personalized name).
Presence of links that may lead to malicious sites (not verifiable in the screenshot but implied).
Urgency or threats (e.g., "click here to cancel and secure your account").
Impersonation of trusted brands (e.g., Apple).
Email B exhibits multiple indicators: the generic greeting, unsolicited verification request, urgent call to action, and impersonation of Apple.
Option A Context:
Since the screenshot only shows email B, and the correct answer is "Only B," we can infer that email A (not shown) does not exhibit phishing characteristics. For example, A might be a legitimate email from Apple with proper personalization, no suspicious links, or a different context (e.g., a purchase confirmation rather than a verification request).
Evaluation of Options:
1. Only A: Incorrect, as email A is not shown, and the correct answer indicates B as the phishing email.
2. Only B: Correct. Email B shows clear phishing characteristics, such as impersonation, a generic greeting, an unsolicited verification link, and urgency, aligning with CNSP's phishing criteria.
3. Both A and B: Incorrect, as A is implied to be non-phishing based on the correct answer.
4. None of the above: Incorrect, as B is a phishing email.
Conclusion: Email B is a phishing email due to its impersonation of Apple, generic greeting, unsolicited verification request with a link, and use of urgency to prompt action. Since A is not shown but implied to be non-phishing, the correct answer is "Only B."
Analysis of Email B:
Sender and Branding: The email claims to be from "Apple Support" and includes an Apple logo, which is a common tactic to establish trust. However, phishing emails often impersonate legitimate brands like Apple to deceive users.
Subject and Content: The subject "Verify your email address" and the body requesting the user to verify their email by clicking a link ("Verify Your Email") are typical of phishing attempts. Legitimate companies like Apple may send verification emails, but the tone and context here raise suspicion.
Link Presence: The email contains a clickable link ("Verify Your Email") that is purportedly for email verification. The screenshot does not show the URL, but phishing emails often include malicious links that lead to fake login pages to steal credentials. CNSP emphasizes that unsolicited requests to click links for verification are a red flag.
Urgency and Vague Instructions: The email includes a statement, "If you did not make this change or believe an unauthorized person has accessed your account, click here to cancel and secure your account." This creates a sense of urgency, a common phishing tactic to prompt immediate action without critical thinking.
Generic Greeting: The email starts with "Dear User," a generic greeting often used in phishing emails. Legitimate companies like Apple typically personalize emails with the user's name.
Suspicious Elements: The email mentions "your Apple ID ([email protected])," which is a placeholder rather than a specific email address, further indicating a mass phishing campaign rather than a targeted, legitimate communication.
Phishing Indicators (per CNSP):
CNSP documentation on phishing identification lists several red flags:
Unsolicited requests for verification or account updates.
Generic greetings (e.g., "Dear User" instead of a personalized name).
Presence of links that may lead to malicious sites (not verifiable in the screenshot but implied).
Urgency or threats (e.g., "click here to cancel and secure your account").
Impersonation of trusted brands (e.g., Apple).
Email B exhibits multiple indicators: the generic greeting, unsolicited verification request, urgent call to action, and impersonation of Apple.
Option A Context:
Since the screenshot only shows email B, and the correct answer is "Only B," we can infer that email A (not shown) does not exhibit phishing characteristics. For example, A might be a legitimate email from Apple with proper personalization, no suspicious links, or a different context (e.g., a purchase confirmation rather than a verification request).
Evaluation of Options:
1. Only A: Incorrect, as email A is not shown, and the correct answer indicates B as the phishing email.
2. Only B: Correct. Email B shows clear phishing characteristics, such as impersonation, a generic greeting, an unsolicited verification link, and urgency, aligning with CNSP's phishing criteria.
3. Both A and B: Incorrect, as A is implied to be non-phishing based on the correct answer.
4. None of the above: Incorrect, as B is a phishing email.
Conclusion: Email B is a phishing email due to its impersonation of Apple, generic greeting, unsolicited verification request with a link, and use of urgency to prompt action. Since A is not shown but implied to be non-phishing, the correct answer is "Only B."
Question 15
Which is the correct command to change the MAC address for an Ethernet adapter in a Unix-based system?
Correct Answer: A
In Unix-based systems (e.g., Linux), the ifconfig command is historically used to configure network interfaces, including changing the Media Access Control (MAC) address of an Ethernet adapter. The correct syntax to set a new MAC address for an interface like eth0 is ifconfig eth0 hw ether AA:BB:CC:DD:EE:FF, where hw specifies the hardware address type (ether for Ethernet), followed by the new MAC address in colon-separated hexadecimal format.
Why A is correct: The hw ether argument is the standard and correct syntax recognized by ifconfig to modify the MAC address. This command temporarily changes the MAC address until the system reboots or the interface is reset, assuming the user has sufficient privileges (e.g., root). CNSP documentation on network configuration and spoofing techniques validates this syntax for testing network security controls.
Why other options are incorrect:
B: hdw is not a valid argument; it's a typographical error and unrecognized by ifconfig.
C: hdwr is similarly invalid; no such shorthand exists in the command structure.
D: hwr is incorrect; the full keyword hw followed by ether is required for proper parsing.
Why A is correct: The hw ether argument is the standard and correct syntax recognized by ifconfig to modify the MAC address. This command temporarily changes the MAC address until the system reboots or the interface is reset, assuming the user has sufficient privileges (e.g., root). CNSP documentation on network configuration and spoofing techniques validates this syntax for testing network security controls.
Why other options are incorrect:
B: hdw is not a valid argument; it's a typographical error and unrecognized by ifconfig.
C: hdwr is similarly invalid; no such shorthand exists in the command structure.
D: hwr is incorrect; the full keyword hw followed by ether is required for proper parsing.
- Latest Upload
- 110Google.Professional-Cloud-Network-Engineer.v2025-09-09.q179
- 112SAP.C-S4EWM-2023.v2025-09-08.q83
- 143TheSecOpsGroup.CNSP.v2025-09-08.q20
- 173CFAInstitute.ESG-Investing.v2025-09-08.q173
- 128PECB.ISO-IEC-27001-Lead-Implementer.v2025-09-06.q132
- 131Salesforce.Data-Architect.v2025-09-05.q216
- 126Adobe.AD0-E605.v2025-09-05.q50
- 162Nutanix.NCP-MCI-6.10.v2025-09-05.q55
- 113Oracle.1z0-591.v2025-09-05.q104
- 185Supermicro.SDLCSA.v2025-09-04.q14
[×]
Download PDF File
Enter your email address to download TheSecOpsGroup.CNSP.v2025-09-08.q20 Practice Test

