Question 826
Read" rights to application files in a controlled server environment should be approved by the:
Question 827
Which of the following resources is MOST helpful to a risk practitioner when updating the likelihood rating in the risk register?
Question 828
Which of the following is the PRIMARY reason for an organization to ensure the risk register is updated regularly?
Question 829
After a high-profile systems breach at an organization s key vendor, the vendor has implemented additional mitigating controls. The vendor has voluntarily shared the following set of assessments:
After a high-profile systems breach at an organization s key vendor, the vendor has implemented additional mitigating controls. The vendor has voluntarily shared the following set of assessments:
Which of the assessments provides the MOST reliable input to evaluate residual risk in the vendor's control environment?
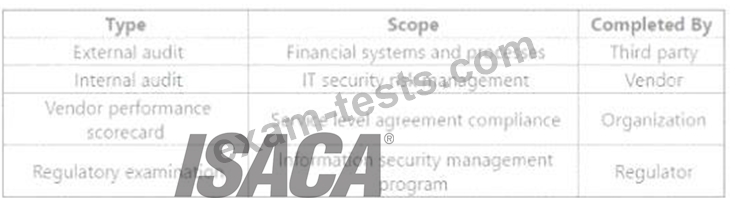
After a high-profile systems breach at an organization s key vendor, the vendor has implemented additional mitigating controls. The vendor has voluntarily shared the following set of assessments:
Which of the assessments provides the MOST reliable input to evaluate residual risk in the vendor's control environment?

Question 830
A risk practitioner has populated the risk register with industry-based generic risk scenarios to be further assessed by risk owners. Which of the following is the GREATEST concern with this approach?

