Question 36
For machine learning to be applied effectively toward security analysis automation, it requires .
Question 37
An organization suspects it has had a breach, and it is trying to determine the potential impact. The organization knows the following:
The source of the breach is linked to an IP located in a foreign country.
The breach is isolated to the research and development servers.
The hash values of the data before and after the breach are unchanged.
The affected servers were regularly patched, and a recent scan showed no vulnerabilities.
Which of the following conclusions can be drawn with respect to the threat and impact? (Choose two.)
The source of the breach is linked to an IP located in a foreign country.
The breach is isolated to the research and development servers.
The hash values of the data before and after the breach are unchanged.
The affected servers were regularly patched, and a recent scan showed no vulnerabilities.
Which of the following conclusions can be drawn with respect to the threat and impact? (Choose two.)
Question 38
A security analyst inspects the header of an email that is presumed to be malicious and sees the following:
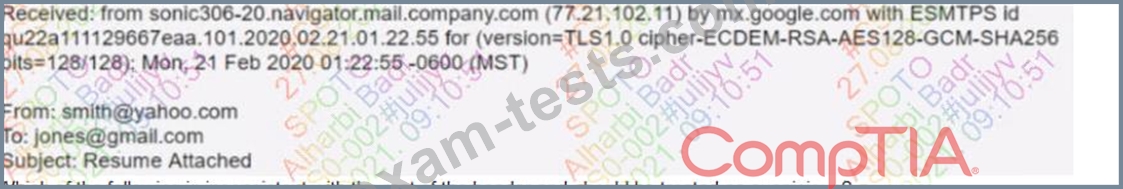
Which of the following is inconsistent with the rest of the header and should be treated as suspicious?

Which of the following is inconsistent with the rest of the header and should be treated as suspicious?
Question 39
A company's change management team has asked a security analyst to review a potential change to the email server before it is released into production. The analyst reviews the following change request:
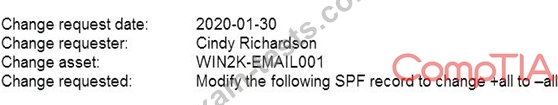
Which of the following is the MOST likely reason for the change?

Which of the following is the MOST likely reason for the change?
Question 40
A SIEM solution alerts a security analyst of a high number of login attempts against the company's webmail portal. The analyst determines the login attempts used credentials from a past data breach.
Which of the following is the BEST mitigation to prevent unauthorized access?
Which of the following is the BEST mitigation to prevent unauthorized access?
Premium Bundle
Newest CS0-002 Exam PDF Dumps shared by BraindumpsPass.com for Helping Passing CS0-002 Exam! BraindumpsPass.com now offer the updated CS0-002 exam dumps, the BraindumpsPass.com CS0-002 exam questions have been updated and answers have been corrected get the latest BraindumpsPass.com CS0-002 pdf dumps with Exam Engine here:

