Question 166
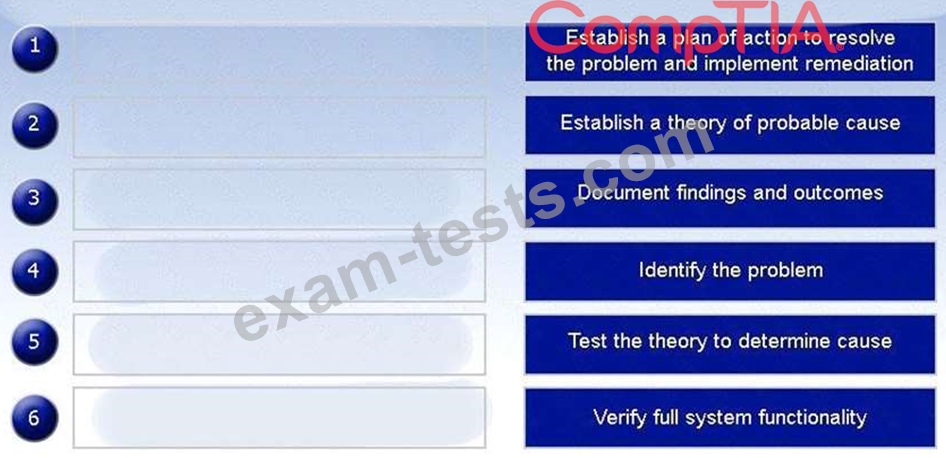
A hosted file share was infected with CryptoLocker and now root cause analysis needs to be performed. Place the tasks in the correct order according to the troubleshooting methodology.

Question 167
Based on demand, an IaaS provider wants to deploy a security application for its customers.
Which of the following is the BEST technique for the IaaS provider to apply this to target systems?
Which of the following is the BEST technique for the IaaS provider to apply this to target systems?
Question 168
A company has deployed a four-node cluster in a COLO environment with server configurations listed below. The company wants to ensure there is 50% overhead for failover and redundancy. There are currently eight VMs running within the cluster with four vCPUs x32GB each. The company wants to better utilize its resources within the cluster without compromising failover and redundancy.
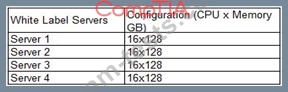
Given the information above, which of the following should a cloud administrator do to BEST accommodate failover and redundancy requirements?

Given the information above, which of the following should a cloud administrator do to BEST accommodate failover and redundancy requirements?
Question 169
An administrator needs to securely troubleshoot an issue with a virtual host from a remote location. Which of the following allows for this by default?
Question 170
A cloud architect created a new delivery controller for a large VM farm to scale up according to organizational needs. The old and new delivery controllers now form a cluster. However, the new delivery controller returns an error when entering the license code. Which of the following is the MOST likely cause?



