Question 36
Cloud bursting can alleviate which of the following attacks?
Question 37
A customer has requirements for its application data to be copied into a second location for failover possibilities. Latency should be minimized, while RPO and RTO are over 15 minutes. Which of the following technologies BEST fits the customer's needs?
Question 38
A company has just completed a security audit and received initial results from the auditor. The results show that the ethical hacker was able to gain access to the company servers by exploiting non-hardened VMs and hosts as guests and administrators. Which of the following should be implemented to harden the environment?
(Select two.)
(Select two.)
Question 39
With increased traffic to a website, several outages have occurred due to a log files filling the root drive of the web servers. An administrator is considering several possible solutions to prevent future outages.
Which of the following techniques is MOST likely to impact server performance if implemented?
Which of the following techniques is MOST likely to impact server performance if implemented?
Question 40
A company has decided to scale its e-commerce application from its corporate datacenter to a commercial cloud provider to meet an anticipated increase in demand during an upcoming holiday. The majority of the application load takes place on the application server under normal conditions. For this reason, the company decides to deploy additional application servers into a commercial cloud provider using the on-premises orchestration engine that installs and configures common software and network configurations. The remote computing environment is connected to the on-premises datacenter via a site-to-site IPSec tunnel. The external DNS provider has been configured to use weighted round-robin routing to load balance connections from the Internet.
During testing, the company discovers that only 20% of connections completed successfully.
Review the network architecture and supporting documents and fulfill these requirements:
1. Analyze the configuration of the following components: DNS, Firewall1, Firewall2, Router1, Rouler2, VPN and Orchestrator Server.
2. Identify the problematic device(s).
Identify the correct options to provide adequate configuration for hybrid cloud architecture.
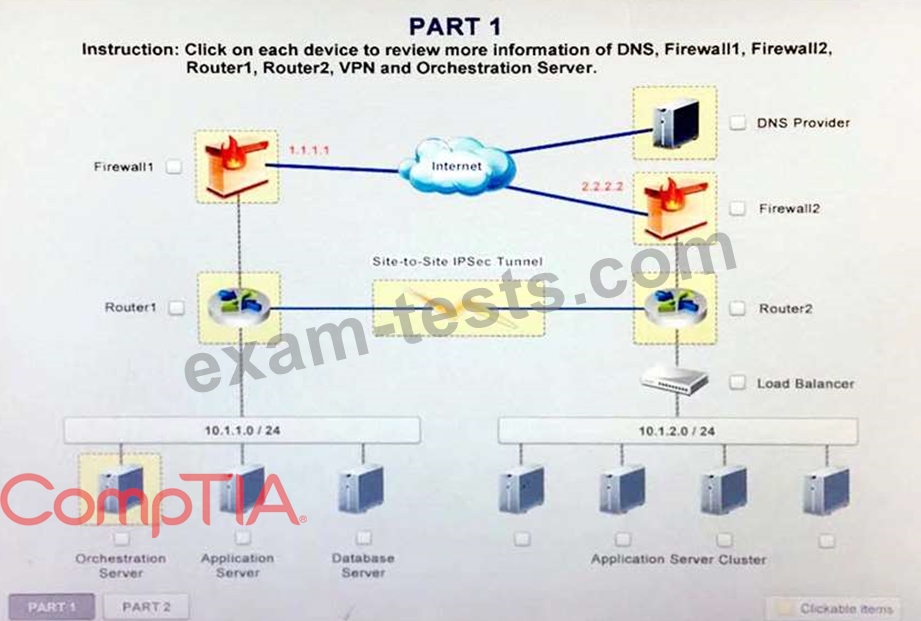
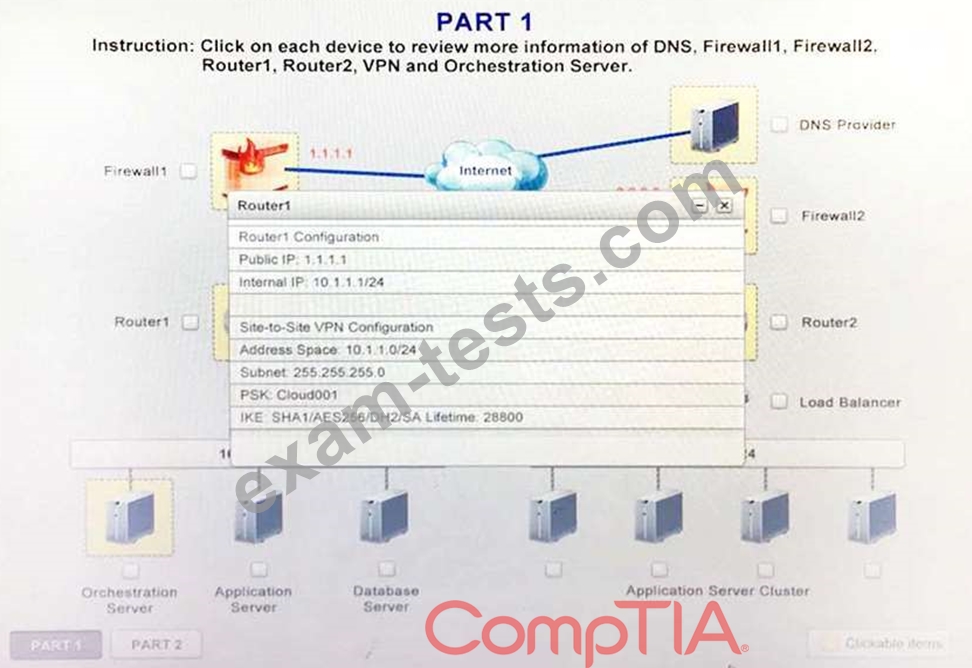
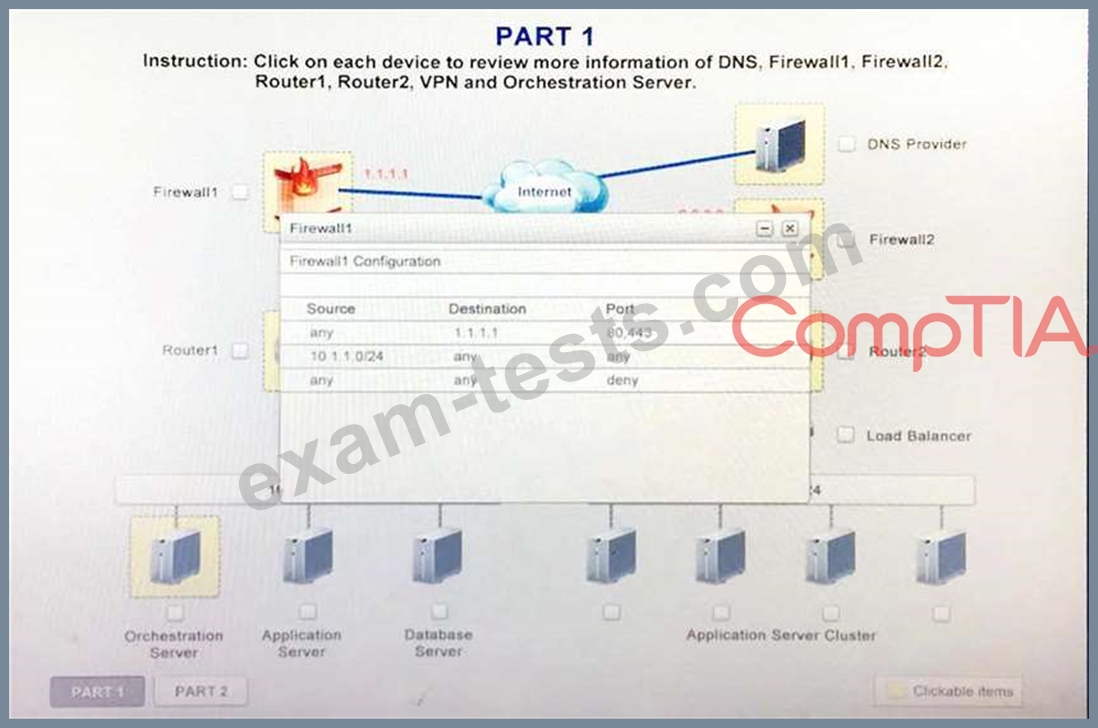
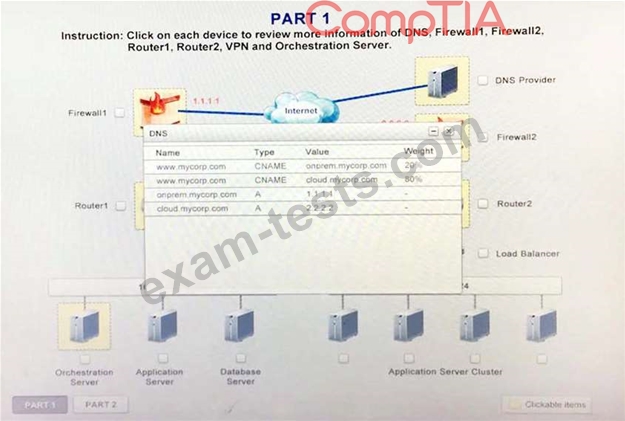
Instruction: Only select a maximum of TWO options from the multiple choice question
During testing, the company discovers that only 20% of connections completed successfully.
Review the network architecture and supporting documents and fulfill these requirements:
1. Analyze the configuration of the following components: DNS, Firewall1, Firewall2, Router1, Rouler2, VPN and Orchestrator Server.
2. Identify the problematic device(s).
Identify the correct options to provide adequate configuration for hybrid cloud architecture.




Instruction: Only select a maximum of TWO options from the multiple choice question

