Question 56
A cloud security analyst recently performed a vulnerability scan on a web application server across all staging environments. The vulnerability scan determines the directory that houses web content is located on the same drive as the operating system. The analyst then attempts to mitigate the vulnerability in all staging environments. The vulnerability scan is performed again and produces the following results:
PROD
Website XYZ web content is housed on the C: drive.
QA
Website XYZ web content is housed on the G: drive.
DEV
Website XYZ web content is housed on the G: drive.
Given this scenario, which of the following should the test results conclude about the vulnerability?
PROD
Website XYZ web content is housed on the C: drive.
QA
Website XYZ web content is housed on the G: drive.
DEV
Website XYZ web content is housed on the G: drive.
Given this scenario, which of the following should the test results conclude about the vulnerability?
Question 57
Which of the following solutions BEST complies with laws requiring secure data-at-rest for a critical application while keeping in mind the need for reduced costs?
Question 58
An administrator is deploying a new application platform with the following resource utilization:
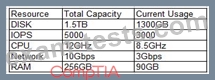
Company policy requires that no resource utilization surpasses 80%. Which of the following resources will need to be upgraded prior to deployment?

Company policy requires that no resource utilization surpasses 80%. Which of the following resources will need to be upgraded prior to deployment?
Question 59
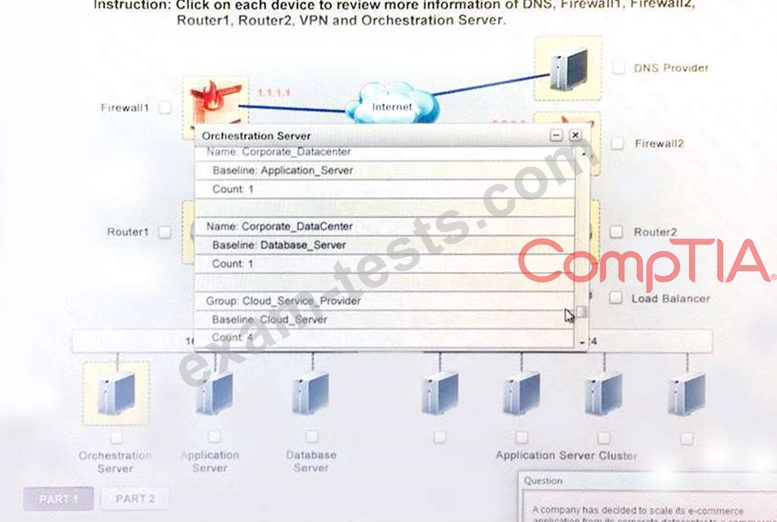
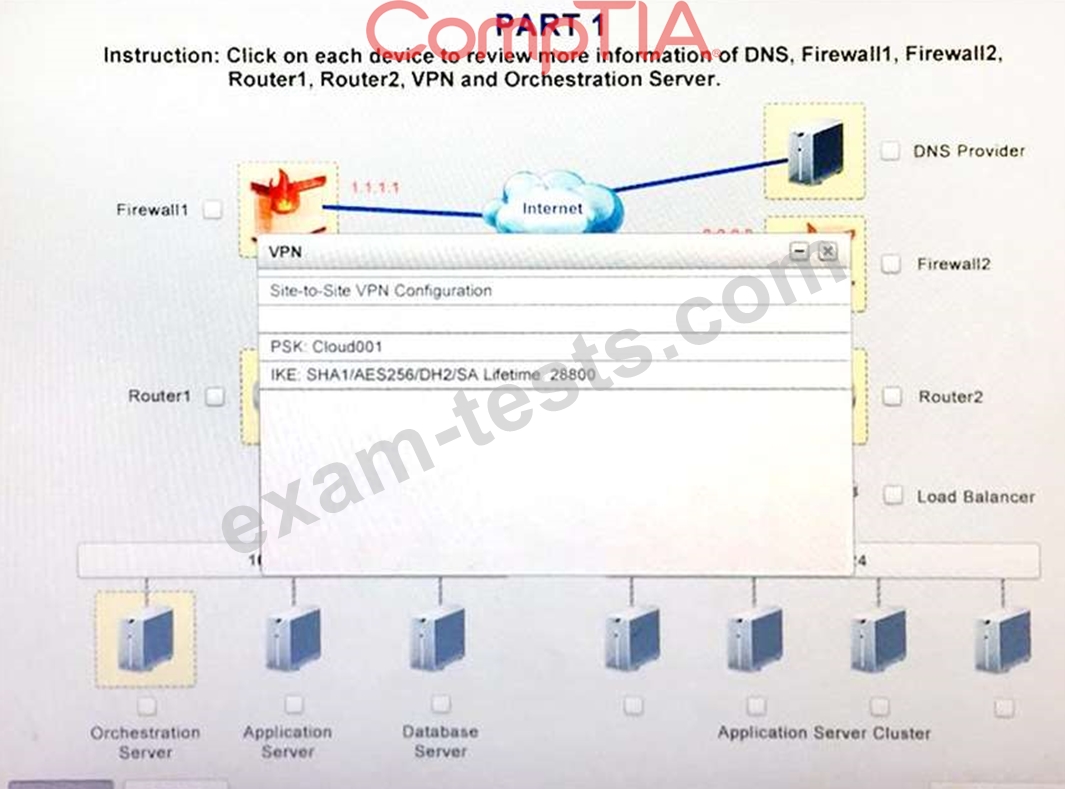
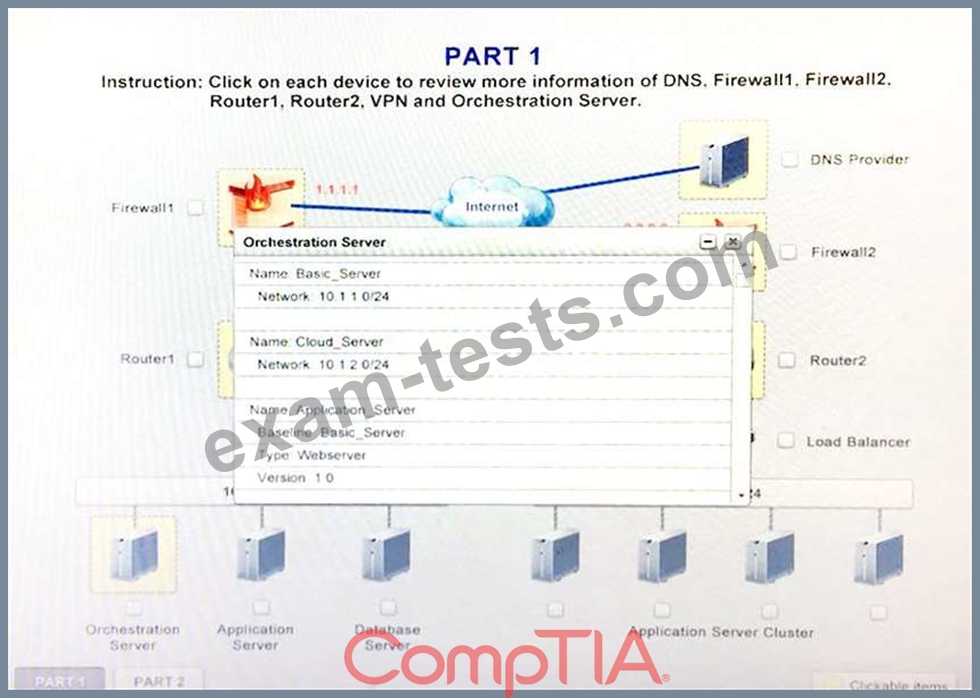
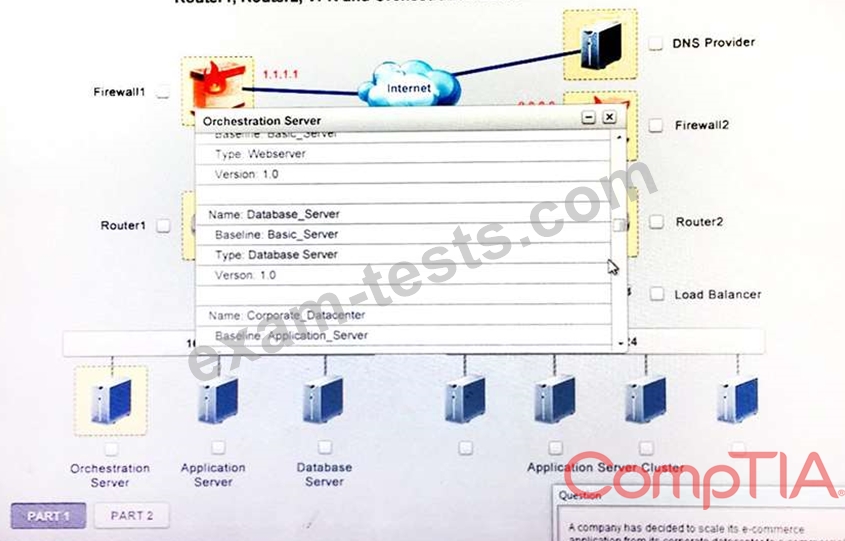
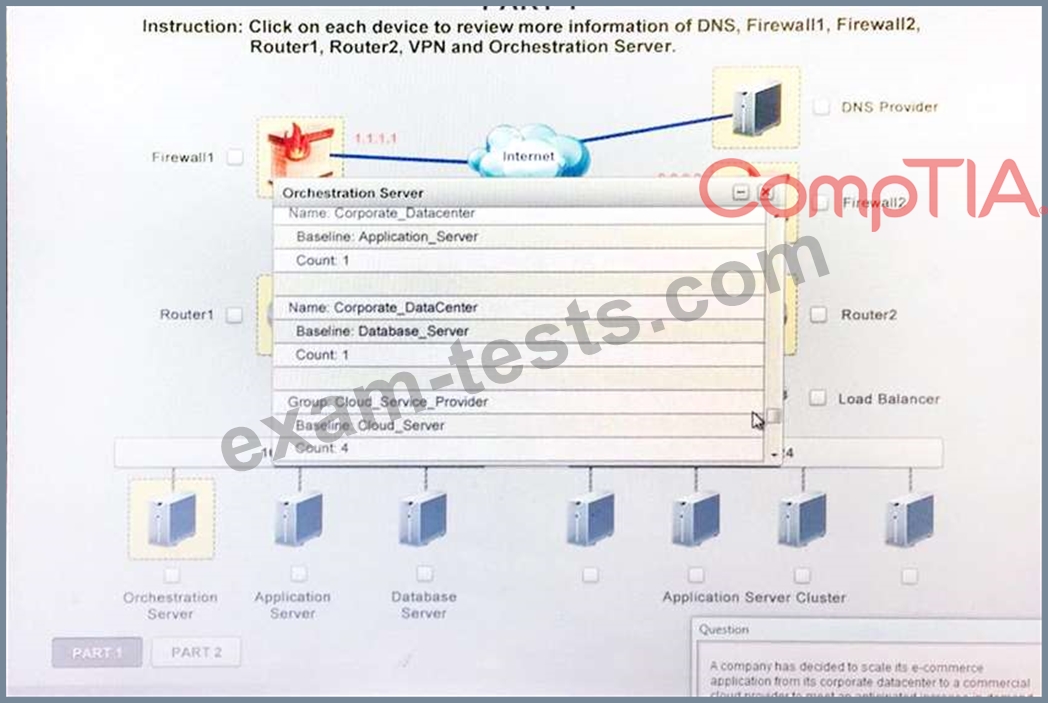
A company has decided to scale its e-commerce application from its corporate datacenter to a commercial cloud provider to meet an anticipated increase in demand during an upcoming holiday.
The majority of the application load takes place on the application server under normal conditions.
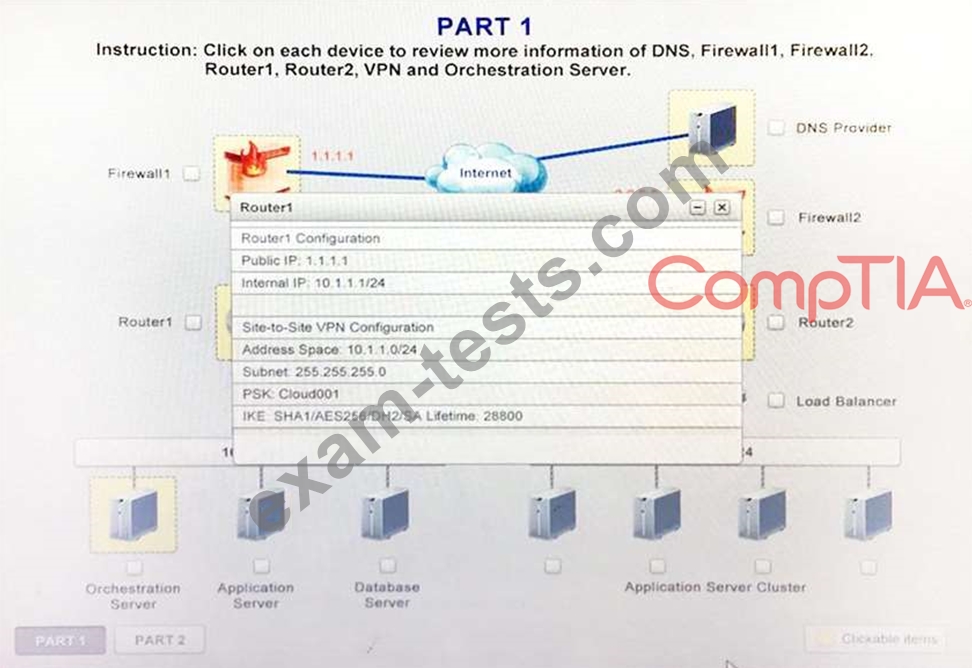
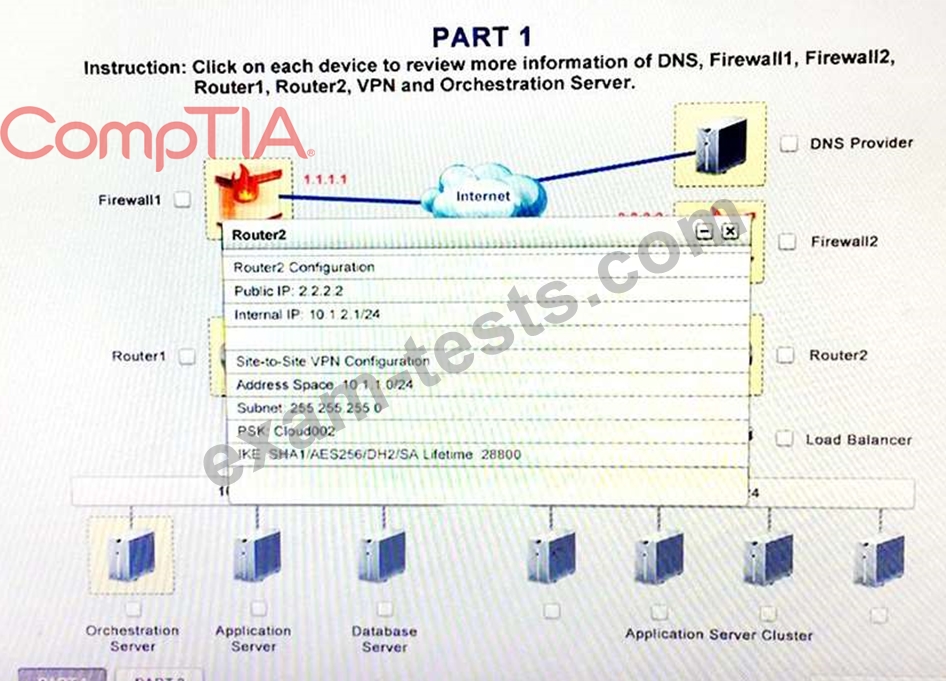
For this reason, the company decides to deploy additional application servers into a commercial cloud provider using the on-premises orchestration engine that installs and configures common software and network configurations.
The remote computing environment is connected to the on-premises datacenter via a site-to-site IPSec tunnel.
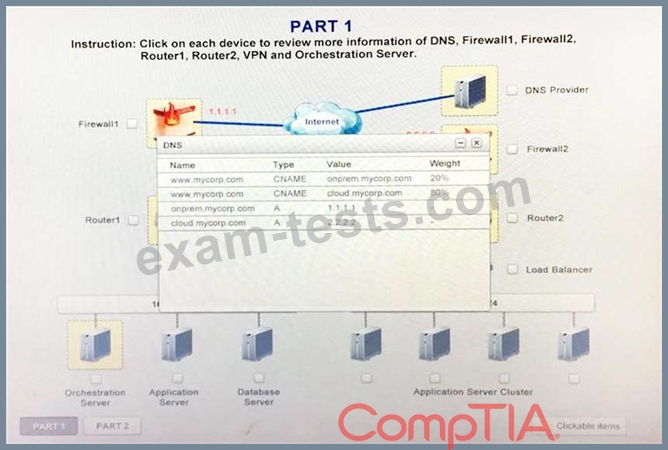
The external DNS provider has been configured to use weighted round-robin routing to load balance connections from the Internet.
During testing, the company discovers that only 20% of connections completed successfully.
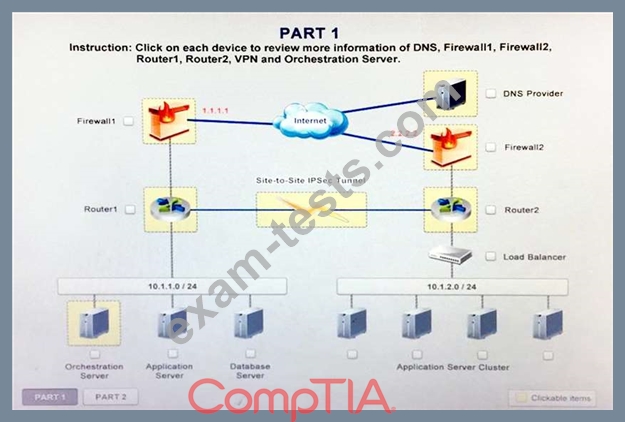
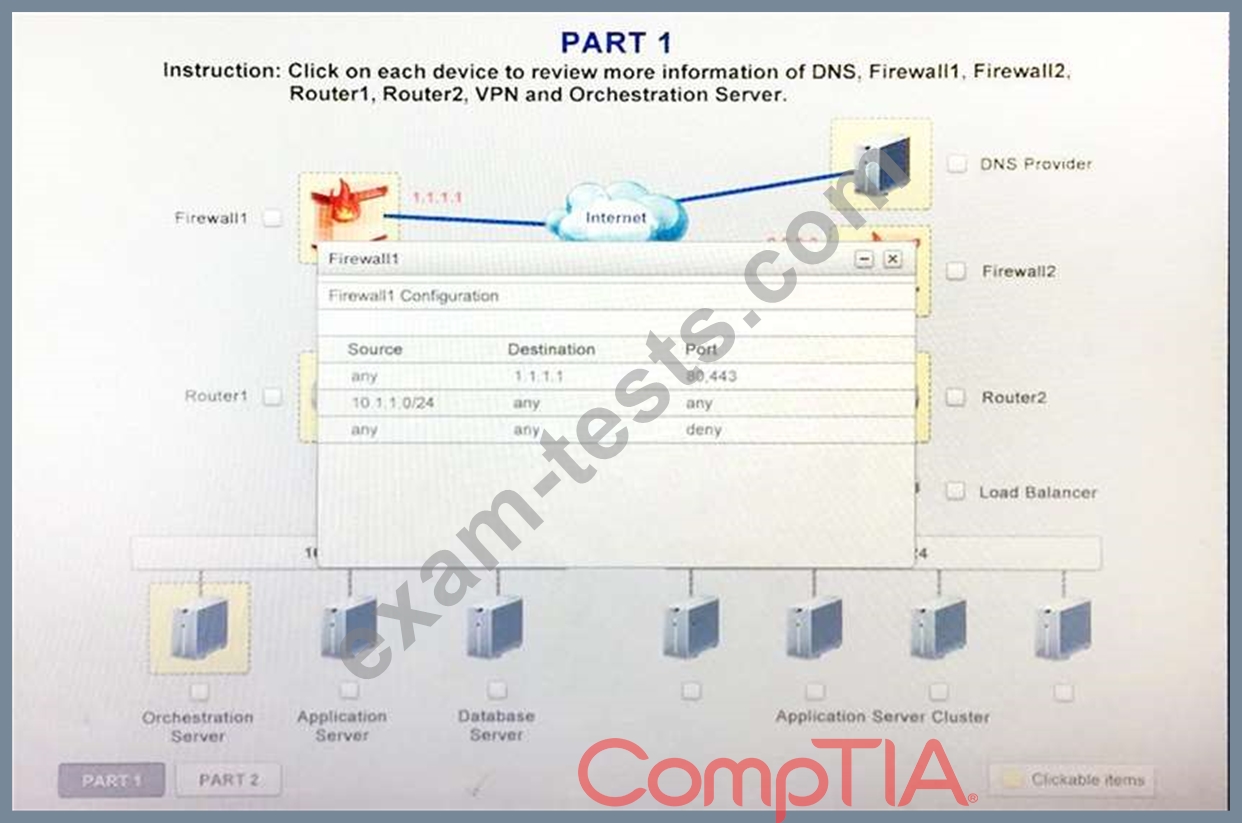
Review the network architecture and supporting documents and fulfill these requirements:
Part1:
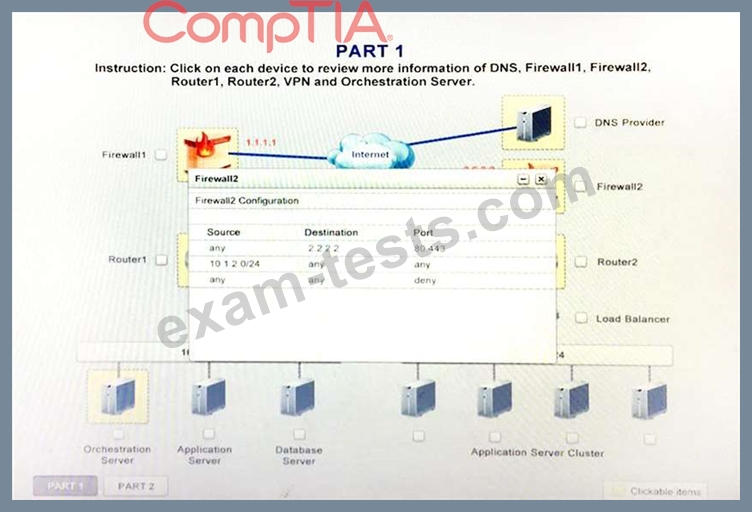
1. Analyze the configuration of the following components: DNS, Firewall1, Firewall2, Router1, Rouler2, VPN and Orchestrator Server.
2. Identify the problematic device(s).
Instructions:
If at any time you would like to bring back the initial state of the simulation, please select the Reset button. When you have completed the simulation, please select the Done button to submit. Once the simulation is submitted, please select the Next button to continue.
Simulation
The majority of the application load takes place on the application server under normal conditions.
For this reason, the company decides to deploy additional application servers into a commercial cloud provider using the on-premises orchestration engine that installs and configures common software and network configurations.
The remote computing environment is connected to the on-premises datacenter via a site-to-site IPSec tunnel.
The external DNS provider has been configured to use weighted round-robin routing to load balance connections from the Internet.
During testing, the company discovers that only 20% of connections completed successfully.
Review the network architecture and supporting documents and fulfill these requirements:
Part1:
1. Analyze the configuration of the following components: DNS, Firewall1, Firewall2, Router1, Rouler2, VPN and Orchestrator Server.
2. Identify the problematic device(s).
Instructions:
If at any time you would like to bring back the initial state of the simulation, please select the Reset button. When you have completed the simulation, please select the Done button to submit. Once the simulation is submitted, please select the Next button to continue.
Simulation










Question 60
A hosted file share was infected with CryptoLocker and now root cause analysis needs to be performed. Place the tasks in the correct order according to the troubleshooting methodology.